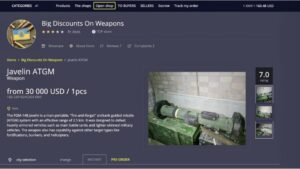
Where it’s legal, accessing the dark web can serve legitimate purposes for threat analysts, privacy advocates, and security practitioners. In one case, the Rhadamanthys stealer developer explicitly states they want purchasers to crypt the malware, with posts from the developer highlighting partnerships with crypting services. “This proliferation of a niche services ecosystem makes cybercrime more accessible to less technical actors while enabling more sophisticated attacks through specialization,” tells Carroll. While DDoS-for-hire services have existed for years, their scale and popularity are growing. The sharing of illegal pornography and discussion of illegal sex acts account for a significant portion of dark web traffic.

Darknet Search Engines:
The dark web’s infrastructure allows users to bypass censorship and maintain privacy, which has legitimate uses, such as secure communications for whistleblowers. However, the same anonymity also facilitates illegal activities, including data breaches and unauthorized sales. Businesses are encouraged to conduct regular cybersecurity risk assessments to prevent their data from being traded on the dark web. The surface web is the most familiar layer, comprising websites indexed by search engines like Google or Bing. This layer includes publicly accessible platforms such as news websites, e-commerce stores, and social media. As when visiting ordinary websites, stay alert to security risks on onion sites.
This ensures greater security and privacy, making it much more difficult for snoopers to get in. Another standout feature is that the servers can’t see what you type, copy, paste, or send. To increase the security level, add password protection and determine the expiration time for messages.
These pages can also help circumvent some forms of government censorship. Dark web websites are pages that exist on a part of the internet that isn’t indexed by traditional search engines like Google. Also known as deep web sites, these pages typically have URLs ending in .onion and are only accessible through special software like the Tor Browser. Norton 360 Deluxe provides a comprehensive suite of protection that can help block malware and dangerous links in real time, and even detect scams using cutting-edge AI detection. Plus, it features a built-in VPN to encrypt your connection, hiding your IP address and online activity, for more anonymous and private browsing.
The Dark Web Is A Vibrant Marketplace That Trades In Illicit Goods And Services
In addition, you can connect your Keybase account with X, GitHub, or Reddit to let people easily trust that they are talking to the actual person. Also, the platform has a feature of automatic deletion of messages – set a timer and they will be deleted after a set period. However, we do not recommend using this platform without taking proper precautions, such as anti-malware and a VPN. You can also use it on the surface web, but it is still unadvisable without proper safety measures. To provide freedom of speech and keep journalism a strong pillar of the economy, the BBC made this Tor mirror. When you try to enter a .onion website, it will reroute your access request around the internet, bouncing it off three random servers before you reach the target website.
PRIVACY ALERT: Websites You Visit Can See These Details About You:
One of the most dangerous aspects of the Dark Web is its potential to facilitate large-scale cyberattacks. Hackers can purchase everything from stolen data to zero-day vulnerabilities (security flaws in software) that allow them to exploit systems before the vulnerabilities are patched. The Dark Web often carries a stigma, primarily due to its association with illegal activities. However, it also serves as a tool for privacy-conscious individuals, activists, and others who need to operate in secrecy. To access the Dark Web, you cannot simply type a URL into a standard browser. Instead, users must use specialized browsers designed to provide a high level of anonymity.
History Of Dark Web Marketplaces
In addition, the content on the pages don’t need any special or custom configuration to access. It might sound weird that Google doesn’t index these pages, but it does carry some logical sense. Google’s purpose is to show the most relevant information to all of its users quickly and easily. That means that Google wants to minimize the amount of time users spend searching for certain queries. Did you know that Google only shows you a glimpse of all the websites that actually exist?

Our Data Can End Up Landing Anywhere
However, it’s up to us to take control of our personal privacy in a world of bulk data collection, surveillance, and personalized ad tracking. There are many legitimate uses for dark web services and communication. As search engine crawlers do not catalog these pages, you would need to know the exact link to access a website in this area of the internet. This could include government services to access your records, health care services, members-only areas, intranets, or corporate resources. Before you go exploring the dark web, it’s crucial to recognize that it is much more dangerous than the surface web — and not just because of all the illegal activity happening on the dark web. Even if you’re a law-abiding citizen only looking to see what’s in the dark, hidden alleys of the internet, there are many dangers that can befall you.
I also recommend covering your webcam and disabling location services before accessing .onion sites. A reliable VPN encrypts your traffic before it enters the Tor network, preventing surveillance from your ISP or malicious actors. During my tests, ExpressVPN’s military-grade encryption and verified no-logs policy provided consistent protection against tracking and monitoring. The kill switch feature also ensures your real IP stays hidden if your connection drops. Tor Metrics is a set of tools and data provided by the Tor Project that offers insights into the performance, usage, and activity of the Tor ecosystem and its nodes. Besides monitoring and improving the network, the data can be used to detect possible censorship or attacks.
- If this sounds similar to The Wayback Machine, the concept is indeed the same.
- The surface web is the open part of the internet, which includes publicly accessible websites and resources.
- There are also reports of “evil GPT” products sold on dark forums or via private messaging, according to Vishavjit Singh, senior threat intelligence researcher at eSentire.
- Like the regular surface web, the dark web offers its own social media sites and web forums.
- Instead, users must use specialized browsers designed to provide a high level of anonymity.
IV Verifying The Authenticity Of Links And Resources
NordVPN offers a 30-day, no-risk trial subscription when you sign up on this page. This provides a full month’s access to all of the features of the #1 VPN for the Dark Web. This is an excellent way for Dark Web users to provide additional privacy protection when accessing the Dark Web.
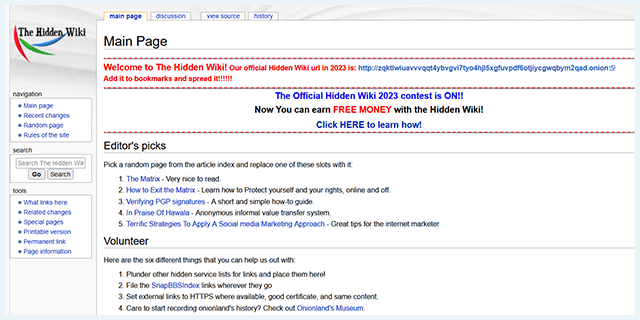
Yes, but you need to be cautious because there are many malicious sites on the dark web. The best way to do that is to get the link from legitimate sources, like The Hidden Wiki. What’s more, you should always use a VPN (like ExpressVPN) with Tor to protect yourself from IP leaks. I also recommend using an antivirus (like Norton 360) to protect your device from malware infections. ProPublica has a clearnet site, but its dark web version won’t see your IP address, so you get better privacy. You can also use its .onion link via the Tor network to access the site in restrictive countries, where it might be unavailable.
By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet. We don’t want to leave you with the impression that everything on the dark web is nefarious or illegal. The Tor network began as an anonymous communications channel, and it still serves a valuable purpose in helping people communicate in environments that are hostile to free speech. “A lot of people use it in countries where there’s eavesdropping or where internet access is criminalized,” Tiquet said.
SecureDrop uses Tor to provide a safe way for whistleblowers to contact various news outlets. Prominent organizations like The Guardian, The New York Times, and ProPublica have implemented it. The software requires two-factor authentication to receive what’s been uploaded by the whistleblower and allows two-way communication between the anonymous contact and the media outlet.
- The dark web is a mysterious place that can only be accessed with specific tools and services.
- The Hidden Wiki is a longstanding directory of dark web sites that offers a way to browse onion services.
- If you choose to explore the dark web, do so ethically and legally to avoid potential risks.
- Onion sites aren’t really dangerous, but they could be when accessed through unfamiliar or suspicious links.
- You can usually select the location you want to appear to originate from and VPNs will use a collection of servers and relays to make tracing your IP difficult.
ProPublica is a prominent investigative journalism platform on the regular and dark web. This duality allows users to choose whether to access the platform openly or anonymously. The dark web version of Facebook isn’t malicious, but if you log into it, it will keep your data. With each random server, your traffic bounces off, and a layer of encryption gets added. These layers upon layers give this network its iconic “onion” name—as the onion itself has layers upon layers.