When a hacker writes up new malware, steals a database, or phishes someone for their credit card number, the next step is often toward dark net marketplaces. These black markets allow buyers and sellers to make anonymous transactions using a combination of encrypted messages, aliases, and cryptocurrency. Hundreds of millions of payment card details have been stolen from online retailers, banks and payment companies before being sold on online marketplaces such as UniCC.
Antivirus Software
Family Dollar is one-half of a consumer’s dream; they offer low-priced goods for families in 8,200 locations nationwide. Delta Dental of California (DDC), Delta Dental Insurance Company, Delta Dental of Pennsylvania, and other subsidiaries may have exposed data; the compromised data is not a product of the organizations. Xfinity is the name of Comcast Communications’ internet, TV, and phone service; it is the most significant cabled internet service in the states, with more than 32 million residential customers.
- Depending on the type of account a cybercriminal compromises, they can gain access to many types of personal information, including your credit card information.
- This anonymity allows criminals to conduct illegal activities without fear of being traced by law enforcement agencies.
- Furthermore, participating in these illegal activities carries the constant risk of being caught by law enforcement agencies.
- For instance, BidenCash saw a surge in user activity following its free data leaks.
Developer Verification: A Promised Lift For Android Security
It has built a reputation for being a reliable source of stolen credit card data and PII. Renowned for its extensive inventory of financial data and sophisticated operating methods, Brian’s Club is a key player in the underground economy of financial cybercrime. Alongside the trade of credit card data on the dark web, complimentary tools named checkers are often offered and sold on the dark web. Checkers are tools used by individuals and organizations to verify the validity and authenticity of credit card information and are used by threat actors to check the illicit information they purchase. Be cautious when making online transactions, especially when it comes to sharing credit card information on the dark web.
Cybersecurity News
Hijacking a PayPal account requires a different approach than stealing a credit card number. Instead of card numbers and CVVs, criminals steal usernames and passwords that they’ve gathered either through phishing or malware. They can then sell the account credentials to a buyer who can log in and drains the funds, or the vendor can transfer the requested amount of money from the victim’s account to the buyer’s account. Freezing or locking your credit accounts ensures that fraudsters are unable to open new accounts in your name. You can freeze your credit by contacting each of the three major credit bureaus. If your email has been compromised, your financial accounts could also be at risk.
“No Place In Our Networks”: FCC Hangs Up On Thousands Of Voice Operators In Robocall War
The dark web provides a breeding ground for illegal activities like carding. Its anonymity attracts cybercriminals who can freely operate without fear of being identified. Law enforcement agencies face significant challenges in tracking down and shutting down these illicit carding sites due to the dark web’s encryption and decentralized nature. The dark web is a precautionary tale of how powerful technology can be turned into a force of evil by bad actors. A recent complaint filed in the US District Court for the Southern District of Florida revealed that a cybercriminal group posted “National Public Data” on a dark web forum for sale at a price of $3.5 million.
Darknet Search Engines:
A letter posted on its homepage said it had been “a great pleasure to work with most vendors and users”. We’re back with another video in our Webz Insider video series on everything web data. Given the platform’s history of providing genuine data in previous releases, it seems improbable that the shop would risk tarnishing its reputation with a fake pack.
- When one goes down, two more emerge with new ideas, better technology, and greater difficulty to track.
- Transactions can be quickly flagged or blocked, making fraud attempts risky and unreliable.
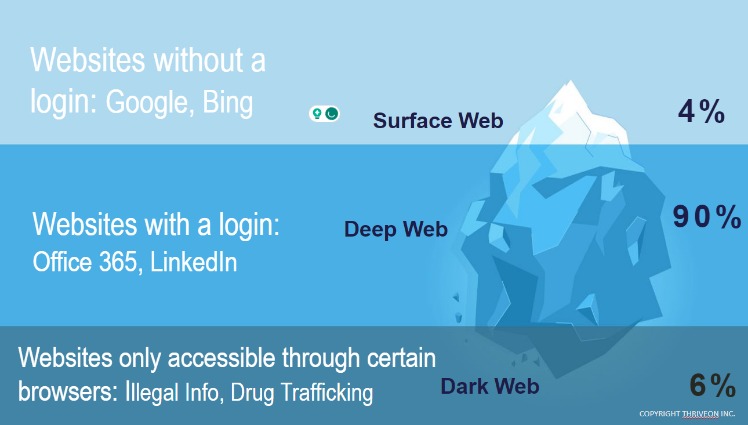
- These are websites such as newspapers, blogs, Wikipedia, etc., that can be accessed through traditional search engines and don’t require any special efforts or credentials to access.
- Because of the level of anonymity, these sites allow cybercriminals, it is critical to use powerful dark web monitoring tools, such as Webz.io’ Lunar, to track emerging financial and reputational threats.
Cool Augmented Reality Examples To Know About

More bogus credit card data, personal information, and documents were sold in 2021 compared to 2020, while products, like hacked cryptocurrency accounts and web services such as Uber, are more available. When you purchase an item or service online, you may be prompted to save your credit card information to the website for faster purchases in the future. While this is convenient, it places your credit card information at risk of being exposed in public data breaches, so it’s best to never save it on websites.
This includes using a secure and anonymous internet connection, using a reputable VPN (Virtual Private Network), utilizing trusted marketplaces and vendors, and practicing good online security hygiene. In addition to just selling credit card details, some threat actors offer a “complete package” often referred to as “Fullz”. Fullz includes full personal details as well as financial details such as bank account details or social security numbers, which can be used for a full account takeover or identity theft. Legitimate users of the dark web include activists, or people who live under oppressive regimes, but they only account for a small percentage of the dark web.
Top Cybersecurity Discord Servers To Join
A popular tool for accessing the dark web is TOR (The Onion Router) network, developed on 20 September 2002, by scientists Roger Dingledine and Nick Mathewson. Through TOR browser, users can navigate the dark web’s contents and reach hidden websites. Funded by the US Naval Research Laboratory as a way to communicate with intelligence sources around the world without getting tracked, the tool anonymises online activities and protects online privacy. The TOR project 2 was released publicly in 2004, and is the most popular publicly available access to the dark web. Once your credit card number has made its way onto the dark web, it’s virtually impossible to have it removed. The dark web is a vast and decentralized network where information is traded anonymously.
N 2025, dark web websites frequently change domains and are often short-lived. Accessing them may require .onion links and the Tor browser, but caution is advised due to legality and cybersecurity risks. No, black market websites operate illegally and pose high risks of scams, fraud, and law enforcement action. By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet. The dark web is a subset of the deep web that is intentionally hidden, requiring a specific browser—Tor—to access, as explained below. No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet.

The data then gets parsed, sorted by bank type and location, and sold in batches. One compromised payment processor or e-commerce platform can yield thousands of card numbers at once. The pricing varies based on the card type, with premium cards from certain banks fetching higher prices. Rather than individual hackers working alone, the reality is that we’re dealing with sophisticated criminal enterprises that function like businesses, complete with customer service and quality guarantees.
Keeping Your Data Safe
Back in the day, carding forums were the busiest of online crime hangouts, selling packs of stolen credit card data to anyone with the cash. That was then; now, you are more likely to find a roaring trade being made on the dark web in the likes of stolen passwords and account credentials, phishing exploit kits and malware-as-a-service platforms. A new report has revealed that the B1ack Stash crime forum has just given away more than a million stolen credit cards for free. Carding shops are a type of dark web marketplace that hosts the trade of credit cards and other stolen financial information. These platforms serve as hubs for cybercriminals to buy and sell compromised payment card details.
Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem. Join us as we break down and discover the methodologies of card fraud using our dark web monitoring tool, Lunar. One of the biggest problems cybersecurity teams face isn’t a lack of tools — it’s too many alerts. Although some of these markets prohibit certain extreme content such as violence or exploitation, most operate with very few rules beyond ensuring the security and anonymity of their users. For instance, BidenCash saw a surge in user activity following its free data leaks.