While its .onion address doesn’t make it much easier to maintain an anonymous account, it does make Facebook more accessible in places where it’s censored. One of the most popular ways to get around the dark web is not to use a search engine at all. Just like in the old days of the internet, the dark web maintains numerous indexes of sites, like The Hidden Wiki.
- They list verified mirrors and often display digital PGP signatures posted by site administrators.
- Their tools often spread through phishing campaigns or compromised software downloads, enabling crimes such as identity theft.
- It’s an easy and simple way to de-couple your internet usage from Google’s monopoly over the web.
- Ransomware threat actors use malware to lock users out of their systems, demanding payment to restore access.
The Dark Web—a hidden part of the internet accessible only through specialized software like Tor—has become increasingly significant as we enter 2025. They help users find real dark web links, verify them through uptime tracking, and avoid dangerous clones. Whether you’re browsing out of curiosity or pursuing sensitive research, using dark web sites that are safe in 2025 is a matter of both security and responsibility. Many directories are outdated or cloned, while others include malicious .onion addresses.
Excavator Search Engine
Choose a trustworthy VPN service that has a strict no-logs policy and supports connection without DNS leaks. Avoid free VPNs as they often lack adequate security or monetize user data. The dark web is highly dynamic; sites frequently change addresses, disappear, or become scams. This ongoing maintenance ensures users can safely and confidently navigate the dark web with the help of the Hidden Wiki. These are the top 10 dark web search engines that allow easier access to the hidden corners of the internet.
With its emphasis on user privacy and a diverse community that spans various interests, Galaxy2 redefines social interactions in the anonymous digital realm. From intriguing forums and bustling marketplaces to enlightening libraries and insightful blogs, the platform provides a snapshot of the Dark Web’s offerings. The platform is regularly updated, ensuring that dead links are removed and new sites are added. From forums and marketplaces to information resources, The Hidden Wiki offers a starting point for Tor newcomers.
Is Using The Tor Network Illegal?
Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy. As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction.
Other Hidden Sites
OnionLand offers a clean design with a simple user interface that includes search suggestions. The search engine allows you to look for old V2 onion addresses, images, and content on I2P. It also conducts searches across both the clearnet and dark web by leveraging multiple indices, so you can filter searches to focus exclusively on the darknet or span both realms. In exploring the top 10 dark-web marketplaces in 2025, we’ve examined their core operations, diverse use-cases, inherent risks, and evolving trends.
Dark Web Sites Name List: Where To Find Secure Marketplaces
If you upgrade to the premium plan, you gain access to advanced search features. Using this feature, you can find historical content or sites that aren’t even active anymore. Our data is available to the public free of charge, and we encourage you to use it to inform your personal or business decisions. If you choose to republish our data on your own website, we simply ask that you provide a proper citation or link back to the respective page on Market.us Scoop. We appreciate your support and look forward to continuing to provide valuable insights for our audience.
Cybersecurity News
The dark web is a complex part of the internet, and specialized search engines are essential for safely experiencing it. It delivers an uncensored search experience, granting users access to a diverse array of information while effectively excluding illegal content. It is that hidden corner of the internet that is hidden from the public and can only be used by a limited number of people.

An easy way to find content on the dark web is to receive a link from someone who already knows about it. These sites aren’t just important resources; they’re like lifelines used to serve readers living under oppressive regimes. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged. There are often copious amounts of how-to articles, software exploits, and hacked credentials for sale. Not every visitor is a criminal, but this is where most cybercrimes begin. Keybase is a fantastic onion website that lets you cryptographically bring your different online identities together.
Best Dark Web Sites To Know In 2025 – Detailed List
However, the dark web environment can be unpredictable and sometimes dangerous, filled with scam links, phishing sites, and other malicious threats. That is why we emphasize caution, vigilance, and adherence to best security practices when exploring these hidden corners of the internet. While the surface web is easily accessible, the Dark Web offers anonymity, uncensored content, and resources that are hidden from traditional search engines like Google or Bing.
Think about what matters most for your browsing and security, and make informed choices to navigate the dark web safely. The dark web is a part of the internet that isn’t accessible with regular browsers or search engines like Google and Bing. To explore it, you need special tools like the Tor browser (short for The Onion Router) and search engines designed specifically for the dark web. Overall, dark-web marketplaces inherently involve substantial risk, and users must thoroughly understand these threats. Understanding both the lawful and unlawful scenarios helps provide a balanced view of their practical applications in 2025. Platforms that provide clear guidelines for maintaining operational security (OpSec) and offer built-in tools for data obfuscation are especially favored.
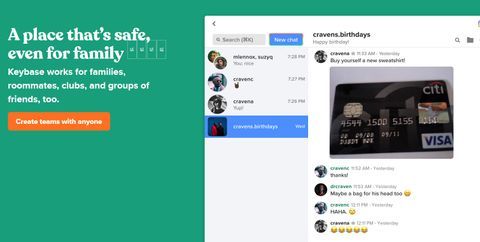
These docs walk users through secure browsing, file storage, and messaging practices, all while maintaining the integrity of anonymous operating environments. Onion sites aren’t really dangerous, but they could be when accessed through unfamiliar or suspicious links. The dark web also helps individuals communicate about or sell illegal items such as weapons, drugs, malware, etc.
- Such social media sites allow people to communicate anonymously and without government oversight.
- Take advantage of Prey’s no-risk, 14-day trial and give you and your business the protection it deserves.
- The competitive landscape remained unchanged, with no significant innovations reported.
- In addition, many dark web websites are configured to block or mislead regular crawlers.
- Scroll on to learn more about dark web links (also called Tor links or onion sites), get the right links for some of the best Tor sites, and find out how to visit them safely.
- This includes password-protected sites, private databases, academic journals, and, notably, dark web services accessible only through networks like Tor or I2P.
Social Engineering And Identity Exposure

It began as a simple, categorized directory of .onion links — helping new users find forums, search engines, whistleblowing tools, and more. Back when reliable dark web search engines were limited, the Hidden Wiki served as a trusted compass for exploring the hidden layers of the internet. The Hidden Wiki remains one of the most popular dark web directories, but it’s also the most frequently cloned. The original offers categorized .onion links, from forums to file-sharing tools. While many users begin their dark web journey here, caution is strongly advised.
Businesses should prepare for more sophisticated ransomware campaigns, potentially leveraging AI to exploit security gaps. The takedown of major groups like LockBit, AlphaBay and Hansa in 2024 demonstrates improved global collaboration among law enforcement agencies. However, this will likely lead to the rise of new, decentralized groups like RansomHub. Crypto-laundering threat actors specialize in stealing and hiding the origins of their cryptocurrency. Cryptojacking involves secretly mining for cryptocurrency via the victim’s device.
Darknet is your best source for the latest hacking tools, hacker news, cyber security best practices, ethical hacking & pen-testing. Sheharyar is a passionate tech-writer who believes in the digital freedom and online privacy of all. He regularly tests and analyzes different VPNs to give accurate and up-to-date user-guides and comparisons.