For obvious reasons—I don’t want to get you or me into trouble, after all—I’m not going to get too specific when it comes to what you can find for sale on the dark web. A lot of transactions are handled via cryptocurrencies such as Bitcoin, which is relatively (but not completely) private and anonymous. Another private cryptocurrency you’ll find being used is Monero, which prides itself on being untraceable.
- Meanwhile our company intranet is hidden from search engines, and requires a password.
- Invest in strong cybersecurity measures; including firewalls; intrusion detection systems; and encryption protocols to protect sensitive data from unauthorised access.
- Also, try its services risk-free with the 30-day money-back guarantee.
- However, the Dark web is a portion of the deep web that can only be acquired through special tools.
- Having been repealed by the OSA 2023, the offence under section 33 CJCA 2015 remains available for offences committed on or after 13 April 2015 and prior to the date of commencement of Part 10 OSA 2023 on 30 January 2024.
Frequently Asked Questions (FAQs) About Dark Web Marketplaces
In 2008, the first Tor Browser was released, making it easier for any internet users to access the dark web. In 2002 the dark web began to grow significantly when researchers backed by the U.S. The Tor Network provided a way to open safe communication channels for political dissidents, while also offering a channel for American intelligence operatives to communicate from around the globe. Journalists in overly restrictive countries also appreciate the anonymity of the dark web. The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose.
Internet Of Things (IoT)

Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for. Some of these sites can be found through regular web browsers, but you’ll then need to switch over to Tor once you’ve got the onion links you want to follow. The dark web, which is what I’m discussing here, is a small subset of the deep web, and refers to websites that are specifically trying to stay out of sight.
Should I Only Use A VPN To Access The Dark Web?
Speaking about the shock arrest of Mr Durov, Mr Gray said on his podcast Risky Business that Telegram has been a haven for crime for a long time. This information can be used to target ads and monitor your internet usage. Also, there’s a vast amount of unsavory content on the dark web, as well as a significantly high number of hackers and scammers looming on the platform. The advantage of using a dedicated computer just to browse the dark web is that your main computer isn’t exposed to any of the threats or risks tied to entering the dark web.
What Is The Dark Web, What’s On It & How To Access It
Only a tiny portion of the internet is accessible through a standard web browser—generally known as the “clear web”. This was calculated by dividing a country’s total number of stolen data points by total population. The team repeated this method to find out the countries with the most data breaches per person. Keep an eye on your financial accounts for any suspicious transactions.
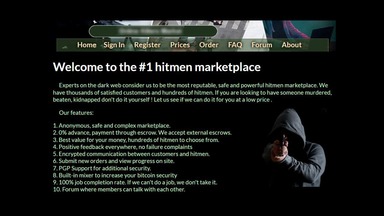
By familiarising yourself with the dark web and the tactics threat actors use, you can better prepare yourself and your organisation to mitigate the risks posed by this hidden corner of the internet. The dark web presents various threats, including malicious software and computer viruses, posing risks to users’ systems and data security. Users also face the potential danger of government monitoring and surveillance — or scams and fraud, and other activities that can lead to financial loss and identity theft. It offers its users secrecy and makes it very difficult to track their activities. This has led to it becoming a marketplace for selling drugs, stolen data and weapons.

Method II – VPN Over Tor
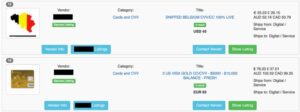
Silk Road became one of the most famous online black markets on the dark web for illegally selling drugs. First, let me explain that this article is intended for users who want to use the dark web for legal and needed purposes, such as finding censored news, blocked websites, and other much-needed services. When European law enforcement shut down the Hansa market in July 2017, investigators had been running it for weeks. Its operators had been arrested in Germany nearly a month earlier, but this was kept quiet, so Dutch police could continue the market’s operations to gather more information about Hansa’s users. This type of darknet is primarily used for illegal activities such as drug trafficking and pornography. Empire Market is the most prominent online market in the English-speaking community and is the largest marketplace on the dark web in the Western Hemisphere.
If a dynamic address is not in use, it can be automatically assigned to a different device. A database is an organized collection of structured information, or data, typically stored electronically in a computer system. A user’s authentication information used to verify identity – typically one, or more, of passwords, taken, certificate. The act of attempting to crack passwords in order to gain access to a computer system by testing them against every possible arrangement of upper case and lower case letters, numbers, punctuation marks and other characters.
It is a small amount of faster, more expensive memory used to improve the performance of recently or frequently accessed data. Artifacts are residual traces left behind by the actions of attackers or malicious actors within a computer system or network. These artifacts can include log files, event records, system logs, network traffic captures, timestamps, registry entries, and more. Anonymisation is the process of turning personal data into anonymous information so that an individual is not (or is no longer) identifiable. A Username is a special name given to a person to uniquely identify them on a computer network. Also called account names, login IDs, or user IDs, usernames are given to a person by the network administrator or they are selected by the user.
CSO Executive Sessions: How AI And LLMs Are Affecting Security In The Financial Services Industry
The darknet is the underlying network infrastructure—overlay networks built on top of the standard internet that require specific configurations or tools to access. These networks, such as Tor, I2P, and Freenet, are designed to enhance privacy, resist surveillance, and allow anonymous communication. There are various technical reasons why a website is not registered with a web search engine.

Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online. Social networks, such as Facebook, have created dark web versions of their sites to address privacy problems related to their surface web versions. ExpressVPN had created a .onion version of its website to allow greater privacy and anonymity for Tor browser users. Known for its publicity stunt releasing millions of stolen card details for free, BidenCash specializes in credit card fraud and identity theft. Users can find numerous tutorials that explain how to accomplish this securely in forums and markets.

Having been repealed by the OSA 2023, the offence under section 33 CJCA 2015 remains available for offences committed on or after 13 April 2015 and prior to the date of commencement of Part 10 OSA 2023 on 30 January 2024. Initially limited to offences of ‘disclosing’, the offence was extended from 29 June 2021 to include ‘threatening’ to disclose private photos/film. It is important to remember that evidence of bullying online may be indicative of bullying and possible further offences offline too. In instances where an individual offers fake identity documents online, prosecution should also be considered under the Identity Documents Act 2010, where the document is one prescribed under section 7.
Ratings are easily manipulated, and even sellers with long track records have been known to suddenly disappear with their customers’ crypto-coins, only to set up shop later under a different alias. Dark web search engines exist, but even the best are challenged to keep up with the constantly shifting landscape. The experience is reminiscent of searching the web in the late 1990s. Even one of the best search engines, called Grams, returns results that are repetitive and often irrelevant to the query.
Related Content
Opennet connections are easier to use, but darknet connections provide more security against attackers on the network. In opennet mode, the network will automatically assign you to other users on Freenet’s network. As I mentioned previously, the dark web is quite popular with journalists, political bloggers and news publishers, and others who run the risk of imprisonment in countries like Iran and others. The last thing you need to do is to start researching vendors and determine what marketplace is a possible vendor to buy the products from. Click on “Safest.” As you’ll see, JavaScript and a few other features will be automatically disabled on all sites.