Although visitors of these forums used nicknames to communicate online, they were very aware that their true identity could easily be exposed, either by hackers or by the police. The deep web is where private data such as governmental and legal documents, medical information and academic records can be found. Data on these sites are encrypted, so only authorized users can access the sensitive information. Simply, the deep web is the part of the Internet that isn’t accessible to standard search engines. But beyond the deep web lies a host of hidden dangers that parents should be aware of – the darknet.
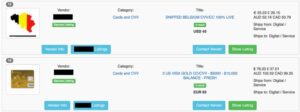
This group is tied to the broader BidenCash ecosystem and focuses on discussions around stolen financial data. Members exchange tips on using compromised credit cards, highlight recent data dumps, and discuss market-related updates. BidenCash is known for releasing large batches of credit card information publicly to attract buyers, with one of the most recent leaks exceeding 900,000 cards. Besides having a very prominent presence on various dark web forums, the Daisy Cloud admin runs one of the most consistent log sharing groups on Telegram, uploading daily stealer logs for both free and premium buyers. NoName057(16) is a prolific pro-Russian hacktivist group that targets NATO countries, Ukraine, and Ukraine’s allies in DDoS attacks.

Parents Text Content
McIntosh later confirmed to authorities that this was a reference to 13-year-old Abigail Williams and 14-year-old Liberty German, two children murdered in 2017 by a man in Indiana. The attorney stressed that McIntosh’s managerial role on the website was different from that of his codefendants. He said McIntosh mostly oversaw the site’s fantasy and roleplay rooms, where “sick people engage in a game” of pretend sexual abuse. The IWF has a policy of not naming and shaming offenders, preferring to continue trying to engage with websites and platforms that have become the destination of choice for peadophiles. “When other international hotlines have tried to name and shame they’ve received legal challenges for their work,” Langford says. The IWF’s list of 320,000 unique image hashes, a vast database of illegal images that is shared with industry partners, has also been partly integrated into a new automated system, freeing up human analysts from often repetitive data entry tasks.
DuckDuckGo Onion Search
Depending on forum policy, “full members,” “registered members,” and “inactive members” can be distinguished. Full members have registered on the forum and meet all other requirements of membership, such as, for instance, a minimum number of posts to forum threads. Registered members have begun the process of registering on the forum but have yet to meet other requirements of membership.
How Telegram Became A Safe Haven For Threat Actors
- (c) We execute text-based CSAM detections against the content of these distinct domains.
- The following year, Congress passed legislation that acknowledged the severity of the crisis.
- The site was “one of the first to offer sickening videos for sale using the cryptocurrency bitcoin,” the UK’s National Crime Agency said.
- The Post reported that in the past few months, NCMEC has fielded “a sharp uptick of reports of AI-generated images,” as well as more “reports of people uploading images of child sexual abuse into the AI tools in hopes of generating more.”
One recent example of this is Will Horley, an English teen who had a fatal reaction to a drug called tramadol. The drug was reportedly bought by Horley from a friend, who bought it from a seller on the Dark Web. The rise of online gaming has attracted unwanted attention from criminals looking to groom children. The Dark Web can be accessed through particular software and programmes.
There’s also a much more sensitive proposal that could only proceed with government approval. Companies could train AI models on fake child sexual exploitation images to build more sophisticated detection systems. Without proper safeguards, though, that route could result in companies developing AI models that are even better at producing even more lifelike images. To search for the onion URLs, you need access to a deep web search engine. If you’re new to the deep/dark web, DuckDuckGo’s onion link should be your first port of call.
How To Protect Your Teen From The Dangers Of The Dark Web
● The open web is the publicly visible part of the internet that most of us use every day, and which we access through search engines such as Google or Yahoo. If your teen insists that they’re merely using Tor to surf the web anonymously, let them know that they can use Google’s Incognito mode instead. As an added layer of protection, use a VPN to keep your family’s online activity hidden from cybercriminals. You may also want to consider installing antivirus and anti-malware to protect your home network, and see to it that all your devices are up to date with the latest security features. Understanding online safety and the risks of being online, including grooming and bullying, is vital to keeping children safe online. To access hidden services and to establish anonymity requires a level of skill.
If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web. You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. ● The deep web is the part of the internet which is generally hidden from public view. Unlike the open web, the deep web is not accessed via the usual search engines. Much of it is very ordinary; organisations have websites that can only be read by authorised people such as their employees, with their information password-protected.
Dark Web Links For News
It is a component of Whonix, an operating system that functions as a whole inside a virtual computer. It includes all the essential productivity software, including MS Word and an email client. The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address.
Table Of Contents
SCP has been shown to reduce criminal behaviour43, and these tactics might be effective against CSAM44. Repetitive pornography use has similar effects to substance addiction31. Many people continually use CSAM and display addictive behaviours32, and the intensity of CSAM use often has properties that users call addictive33. In the search engine data, we notice that users who seek help often refer to their condition as ‘child porn addiction’. Understanding the commonalities between CSAM use and addiction is beneficial to prevention and treatment.

Here, it would be possible to predict an individual’s standing within the offending community based on online behavior (liking of posts, badges, awards). Finally, getting a better sense of the criminogenic needs and risk profiles of the darknet users would be essential as the current evidence base suggests variability in user characteristics. The TOR browser, on its own merits, is an application and preforms as an Internet browser, enabling the user to access the world wide web, while ensuring anonymity for the end user. In addition to these “clearweb” sites, the TOR browser accommodates darknet sites or onion sites—websites whose url ends with .onion. These darknet sites are websites, forums, and other online archives that are not indexed by publicly recognized search engines, referred to as “hidden services” or HSes. It may also include encouraging youth to send sexually explicit pictures of themselves which is considered child sexual abuse material (CSAM).
What Percentage Of The Internet Is Dark Web?

One example is your medical history; this can be accessed from anywhere, by authorised persons. The dark web is a hub for illegal activities like drug trafficking, weapons trading, human trafficking, and cybercrime, making it a treacherous environment, especially for teens. Due to its anonymity and lack of regulation, the dark web facilitates these malevolent acts, posing significant risks. Teens who venture into this shadowy part of the internet may inadvertently engage in or be exposed to illicit activities, facing harmful content and potential legal consequences. To understand more about these dangers and how they affect adolescents, the website Evolve Treatment discusses the alarming implications of dark web exposure for teens. It’s a place where you’ll find data leaks and illegal trades, but also legitimate, legal online activities users want to carry out without attracting the attention of law enforcement agencies or governments.
Onion Links: How To Access Them
McIntosh revealed some of those offenses voluntarily in interviews with investigators, Serafini said. Though his codefendants didn’t disclose prior instances of abuse, the attorney called it “wildly unlikely” that their involvement in the website was their “first rodeo.” Though Schiller suggested that McIntosh’s history of abuse made him the worst of the site’s four leaders, Serafini disagreed.