
This is especially valuable for people in censorship-heavy regions or under surveillance. These docs walk users through secure browsing, file storage, and messaging practices, all while maintaining the integrity of anonymous operating environments. Many phishing sites imitate trusted platforms like the Hidden Wiki to trick users. These clones often use nearly identical URLs to lure visitors into scams or malware traps.
Don’t Be The Next Dark Web Statistic: Protect Yourself Against Cybercrime And Stolen Data

Cryptocurrencies such as Bitcoin have been the dark web currency even before they became available to the general public. Right now, you can use many cryptocurrency .onion sites to buy or sell all types of cryptocurrencies. While this is not much compared to standard email services, it is enough for PGP-encrypted messages.
Finding Onion Sites In 2025, Safe Ways To Explore The Dark Web
Wasabi Wallet isn’t free to use, but, for a small fee, you get reliable and anonymous cryptocurrency transactions. SecureDrop is one of the most reliable file-sharing sites on the deep web. SecureDrop helps whistleblowers anonymously send sensitive material to media outlets via a unique SecureDrop URL. The files are automatically encrypted, and the sender’s IP is not logged. To help you make educated choices about cybersecurity to keep you (and your data) safe and secure, by providing detailed, accurate, and practical information based on thorough testing. SecureDrop stands out as the leading platform for secure document sharing used by major news organizations.
Use A VPN

Your ISP, and possibly the authorities, may decide to start monitoring your activity more closely to look for threats or illegal activity. That’s why we always recommend using a VPN over Tor—even if you feel you have nothing to hide. This just involves turning on your VPN before you open Tor and connect to dark web sites. A favorite of journalists and their anonymous sources, SecureDrop makes it easy to share confidential information without revealing your identity.
Rise Of Smaller, Encrypted Markets
- Crypto services use various measures to keep cryptocurrency wallets secure and make sure your Bitcoin is safe.
- mark it means it has been verified as a scam service and it should be avoided.
- Instead, use a dark web-friendly email provider like ProtonMail’s .onion version or Mail2Tor.
- In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites.
- Set Tor Browser’s security level to “Safest” for critical dark web activity.
|
- The dark web, a subset of the deep web, is where anonymity and secrecy intensify.
- Though they have their limitations, most of the time you’ll see irrelevant or spammy links for your search results.
- Built-in features like script blocking and anti-tracking ensure a safer browsing experience.
- But, honestly, if you are going on the dark just to enjoy free music, we recommend that you go for free torrent platforms on the surface web instead.
- These tools are open-source, regularly audited, and trusted by privacy communities around the world.
- This traditional search engine is also compatible with the dark web and can help you find dark web websites.
}
A robust antivirus can help block malware and other online threats, even on the dark web. Download Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. Install Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. ZLibrary hosts free file-sharing access to academic texts, scholarly articles, and general-interest books.

There are already many services on the dark net that sell AI-made malware for a hefty price. Even though AI technology has come a long way it is still not up to its full potential. It is still in a growing phase and as AI tech becomes more powerful and advanced so does the malware on the dark web sites. This also means that there are going to be hackers looking for new and advanced malware that will keep the market going. According to a study, by the year 2025, the damage because of cyber-attacks is expected to reach $10.5 trillion and AI is going to play a big part in that.
Best Dark Web Sites In 2025 + How To Stay Safe
- Hidden Wiki was originally the name of a .onion hidden service on the Tor network, hosting a directory for links to websites on the Tor dark web.
- The dark web in 2025 still holds power, but only for users who browse smartly.
- The official Tails OS documentation is also accessible through an .onion mirror, offering users critical setup and usage guides directly over Tor.
- ProPublica is one of the most popular legitimate sites on the dark net.
- Follow the below tips to increase your online safety while browsing websites on the Dark Web.
However, the effectiveness of these regulations will depend on their implementation and enforcement by the authorities. The impact of cryptocurrency regulations on dark net markets will vary depending on the type of market. Experts from all countries should come together to design a framework for regulating the use of cryptocurrencies on the dark net. They should all present the challenges that they might face in their countries regarding the regulations for the use of cryptocurrencies on the dark net.
From state-sponsored groups to ransomware gangs, criminal activity is innovating at a rapid pace on the dark web. Businesses must stay vigilant and proactive in addressing these threats, using tools like CybelAngel to monitor dark web activity and protect their assets. The proliferation of IoT and 5G devices will provide new attack vectors for infostealer gangs. As AI becomes more accessible, hackers may use AI-driven tools to automate data theft on a massive scale. Unlike Chrome, Bing, or Firefox, people can’t access the dark web without certain software or configurations.
Top 20 Benefits Of Using Agentic AI For Businesses
So always take proper security precautions on the Dark Web before using it. Dark Websites can only be accessed using specialized privacy browsers, which encrypt your online data. Connect to the VPN before launching the Tor Browser, ensuring all your traffic is routed through the encrypted VPN tunnel first. Although this combination improves privacy, it can also further slow your connection speed, so balance your need for security with usability. Using a VPN is optional but highly recommended for users seeking maximum anonymity or those accessing sensitive content on the dark web. Hidden Wiki was originally the name of a .onion hidden service on the Tor network, hosting a directory for links to websites on the Tor dark web.
That said, if ProtonMail doesn’t suit your needs, there are other Dark Web email platforms available, such as RiseUp and Mail2Tor. For example, RiseUp is an invite-only platform, meaning that you will need an invitation to use it. Stay safe and informed as you explore the deeper layers of the internet. Some do, like Ahmia; others like Torch index nearly everything, including illicit content. Use Tor Browser, a reliable VPN, and never use your real identity or login credentials. Recon is used to find information about darknet vendor profiles and monitor their activity.
Popular Dark Web Links & Websites
Tor Network, short for “The Onion Router”, is a network consisting of volunteer servers that encrypt Internet traffic and route it through multiple nodes. This technology makes it very difficult to track the identity or location of users. This is particularly useful for people living in countries with internet censorship, journalists, activists or simply for those who want to protect their privacy. Keep a private list of bookmarked .onion sites you’ve verified yourself.
Keep Tor Browser Updated
Despite its name, the marketplace operates primarily in English and serves a global audience. It has gained a reputation for being a reliable source of high-quality data for cybercriminals. It has built a reputation for being a reliable source of stolen credit card data and PII.
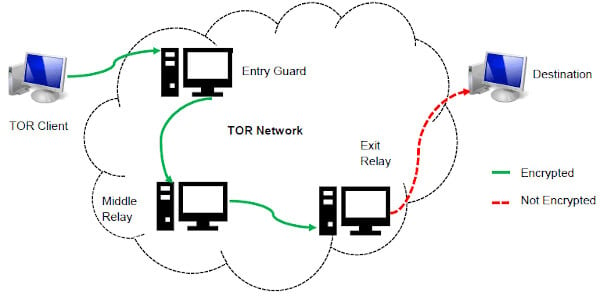
Built-in features like script blocking and anti-tracking ensure a safer browsing experience. As digital landscapes evolve, so do the methods of accessing hidden content and maintaining anonymity. As the most widely used anonymity network, Tor routes your internet traffic through a series of volunteer-run servers (relays) around the world. This “onion” routing masks your IP address and encrypts your data multiple times, peeling away layers of encryption at each relay. Crypto services use various measures to keep cryptocurrency wallets secure and make sure your Bitcoin is safe.
No user names are tied to actual identities, and no moderation like one may find on Reddit. Users leverage these platforms to organize protests, whistleblow, share survival guides, or share files P2P. These are the primary sources of what the general public thinks of as “dark web.” Online marketplaces selling hacked credit cards, fake passports, malware kits, untraceable drugs, anything. Onion links have no regular domain names registered under the domain name registry. Instead, they are designed using a cryptographic key and can be accessed only through software like the Tor browser. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction.


