But it is far from harmless, firstly because it can be created from real photos of children, including images that are completely innocent. In the last few decades, the threat against children from online abuse has multiplied at a concerning rate. According to the Internet Watch Foundation, which tracks down and removes abuse from the internet, there has been an 830% rise in online child sexual abuse imagery since 2014.
Network18 Group Sites
Surfshark supports unlimited simultaneous connections to protect as many devices as possible. Also, try its services risk-free with the 30-day money-back guarantee. The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption. This is high-level protection; no one can intercept your data or activities. It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. It adds an extra encryption layer and passes your traffic through a secondary server of your choice, preventing anyone from seeing that you are accessing the web via Tor.

Investigations

Alicia Kozakiewicz, who was abducted by a man she had met on the internet when she was 13, said the lack of follow-through was disheartening. Now an advocate for laws preventing crimes against children, she had testified in support of the 2008 legislation. In some sense, increased detection of the spiraling problem is a sign of progress.
One Of World’s Largest Dark Web Paedophile Networks With 1,800,000 Users Uncovered
- Bing was said to regularly submit reports that lacked essential information, making investigations difficult, if not impossible.
- This type of monitoring could help you catch identity theft before extensive damage is done.
- Norton VPN fortifies your internet connection with ultra-secure AES-256 encryption, masks your IP, and never logs your activity.
- Some have focused on the youngest and most vulnerable victims, while others have cut back on undercover operations, including infiltrating chat rooms and online forums.
Your data is encrypted in the Tor browser before reaching the ZeroBin servers. Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web). It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource.
Breaking News

Onion sites aren’t really dangerous, but they could be when accessed through unfamiliar or suspicious links. The biggest and most frustrating part about dark websites is that they live for a short span of time. These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. Unlike other search engines, it does not collect or share web activities and personal data of users. When viewed through this lens, the dark web’s legality is based on how you as a user engage with it. You might fall to the wayside of legal lines for many reasons that are important for the protection of freedom.
An Explosion In Online Child Sexual Abuse: What You Need To Know
In March, the police conducted coordinated raids across 31 nations in what Europol’s Guido Limmer described as the “largest operation ever” of its kind. Before authorities took it down on March 11, 2025, Kidflix was expanding at an alarming rate, with 3.5 new videos being uploaded every hour. Germany’s top security official thanked the authorities for their success. He warned that many children unknowingly expose themselves to danger simply by sharing explicit pictures either with a partner or friend. Before these children realise it, they are trapped in a world they could never imagine. He explains that the perpetrators do not work in silos, but rather as part of a larger network which makes it difficult to track down those truly in control.

HTML Attachments: A Gateway For Malware?
Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites. It is the dark web’s version of Wikipedia with a massive links directory. You will find all the necessary .onion links to access any content or service on the dark web. Identity theft monitoring is critical if you want to keep your private information from being misused.
Onion Links: How To Access Them
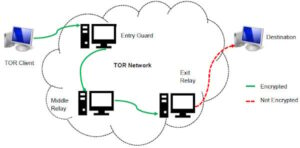
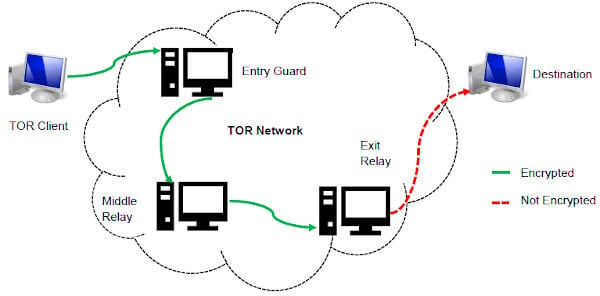
Dark web exchangers bypass this smoke signal by primarily using cryptocurrencies. Regular internet transactions typically leave a trail, marking their presence to authorities. Naval Research Laboratory developed Tor in the 1990s to conceal American dissidents or operatives communicating within oppressive regimes.
- Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.
- This scale is especially troublesome when dark web materials lack physical residue.
- The surface web (often referred to as the “visible web”) is the portion of the web available to the general public and indexed in the standard web search engines such as Google, Bing, and Yahoo.
- Did you know that Google only shows you a glimpse of all the websites that actually exist?
DuckDuckGo is a privacy-focused search engine that works as Tor browser’s primary search engine. It doesn’t track searches or store personal data, making it a strong option for users seeking more anonymous private browsing. However, DuckDuckGo doesn’t index dark web content — it only accesses surface and deep web sites through Tor. Facing criminal investigations or charges for Internet sex crimes can be overwhelming and disappointing. In some cases, you may feel hopeless going up against the large investigatory bodies of the U.S. state and federal governments. However, you have legal options you can leverage to protect your rights, defend your innocence, and challenge the charges against you.

The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. Instead, you need a specific configuration, software, or authorization, such as Tor, to access it. Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages. Some users also share links on encrypted apps like Telegram or Keybase that you can check.
This provides a full month’s access to all of the features of the #1 VPN for the Dark Web. This is an excellent way for Dark Web users to provide additional privacy protection when accessing the Dark Web. There are multiple search engines on the dark web that can help you find what you’re looking for. DuckDuckGo’s no-track dark web search service can be accessed in the Tor browser and is an excellent resource for information about the dark web. Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia. The same anonymity that publishers enjoy on the dark web can be utilized by users who want to read the available information.
The fallout for law enforcement, in some instances, has been crushing. McIntosh, shackled in orange prison garb, scanned the empty seats reserved for his family as deputies led him from the courtroom. His hearing came one day before the man who killed Abby and Libby was sentenced to prison, too. Instead, he apologized to Cannon, to the children he’d victimized, and to his family, none of whom attended the hearing. “It isn’t pretty, it isn’t fun, and it isn’t right,” he said, but it doesn’t require the abuse of actual children.