Daniel’s Hosting specializes in anonymous hosting services optimized for Tor sites, providing secure environments and DDoS mitigation. The Tor Project’s official onion site offers secure downloads of the Tor Browser and developer resources, helping users access and contribute safely to the Tor ecosystem. These platforms underpin the technical infrastructure necessary for dark web functionality. Another critical advantage of the Hidden Wiki lies in its resistance to censorship. This makes it an essential resource for users living under oppressive regimes or in countries with strict internet controls. The Hidden Wiki empowers people to access alternative viewpoints, engage in uncensored discussions, and exercise freedom of information that surface web search engines cannot guarantee.
How AI Is Revolutionizing Automated Malware Classification Technique
- Leveraging these essential tools with caution and awareness will greatly enhance your ability to find dependable .onion links and navigate the dark web safely.
- Impreza Hosting’s .onion link provides hosting services designed for Dark Web users, offering anonymous and secure solutions for websites and applications.
- Once you have the Tor Browser installed and optionally connected to a VPN, you can access the Hidden Wiki by entering its .onion URL directly into the browser’s address bar.
- It aims to preserve the internet’s scientific and cultural heritage.
- This space for private free speech also carries the risk of exposing you to harmful content.
Exploring the dark web can seem mysterious, but with the right guidance, it becomes a valuable tool for privacy, security, and uncensored access to information. Please check your local laws to ensure your use of VPN complies with statutory requirements. Download Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. Install Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. Privacy advocates frown upon it because of the way it harvests data and profiles users. These concerns are valid because using Facebook undoubtedly exposes users to some of the highest levels of surveillance capitalism anywhere on the web.
Do I Need A VPN If I Use Tor?
This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. Being a passionate engineer and new technologies advocate, writing about new pieces of stuff is what a.k.a Scorpion gets engrossed more often. He takes a deep interest in Dark Web and thus spends most of his time knowing and writing about the nitty gritty of the Dark Web Market, Deep Web Links and Websites.

Best Dark Web Sites To Know In 2025 – Detailed List
Because dark web sites can only be reached with a dark web browser like Tor browser, the best dark web sites, best onion sites, and best Tor websites are all one and the same. And because they aren’t searchable via Google or Bing, onion site lists are important roadmaps to help users find what they’re looking for on the dark web. Please be aware that accessing and using .onion sites comes with risks and legal implications. Use these resources responsibly and be cautious of potential security threats. Always double-check the spelling of a link and compare it against a trusted directory or the official announcement thread (if available on Dread or Reddit). Avoid clicking links posted on surface web comment sections or unverified forums.
D Onion Websites: Between Anonymity And Risks
Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally. Activists and government critics prefer to remain anonymous, fearing repercussions if their identities are revealed. Besides, victims of crime may want to hide their identities from their perpetrators. Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble.
Can I Be Tracked Using A Dark Web Search Engine?
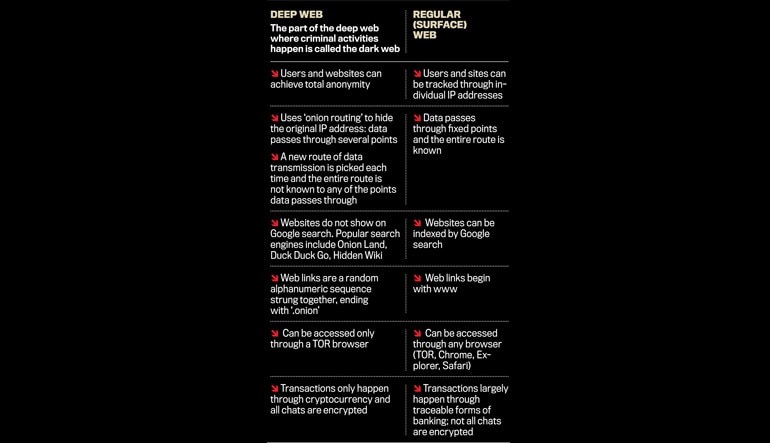
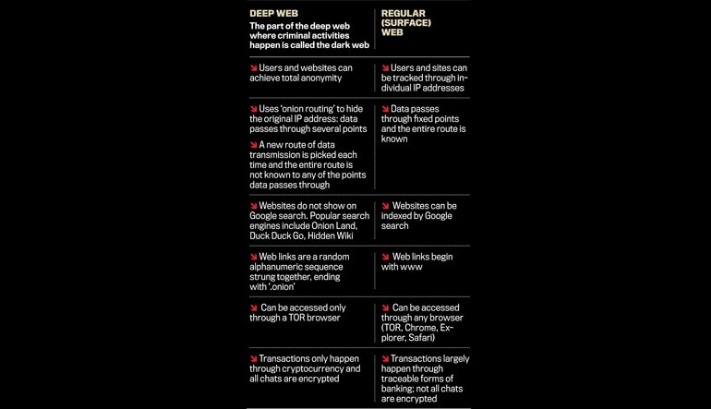
Many news publications, like the ones listed above, have a SecureDrop on their .onion sites. Founded by security researcher Juha Nurmi, Ahmia is essentially a list of “hidden” sites that do want to be found. Onion sites are “crawled” and added to the list provided their “robots.txt” file permits it, and if it is not on their blacklist of sites with abuse material. Site operators can also submit their own .onion sites for indexing. Onion sites are considered part of the deep web because search engines like Google and Bing can’t index them.
It’s an interesting resource that translates Tor internet traffic levels into easy-to-digest stats. Although Hidden Answers offers an outlet for anonymous dialogs, users should stay cautious while browsing. Posts on controversial or even illegal topics are fair game, so the Tor website is a double-edged sword.

By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet. Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools. For journalists, students, researchers, and security professionals, it’s a powerful tool when used ethically and safely. A curated collection of darknet resources for educational purposes, offering insights into darknet frameworks, tools, and security practices.
Mantener Actualizado El Navegador Tor
On the contrary, you can also purchase information from the website. As stated by the website, the whole process of exchange involves the seller, the buyer, the agent and the guarantor of transactions. It is the biggest online psychedelics store (dark web links for android) on the darknet. The drug market offers products such as LSD, Mescaline HCL pure, and DMT Freebase. The website claims that all the products are tested by them and reagent or are lab tested.

That said, the social network’s data collection and tracking practices may seem at odds with many of the principles motivating dark web users. Concerns about how Meta treats user data have led many people to delete their Facebook profiles or at least limit their social media presence. To access them, copy and paste the hyperlinks provided into the Tor browser. In contrast, sites hosted on the dark web can only be accessed via onion routing with Tor, or another dark web browser.
Many users rely on the Hidden Wiki to find reliable dark web resources safely and efficiently. One of the primary reasons users prefer the Hidden Wiki and similar dark web directories over Google is privacy. Google’s business model depends heavily on tracking user behavior, collecting vast amounts of personal data to tailor ads and search results. By contrast, accessing the Hidden Wiki through the Tor Browser offers anonymity and minimal data exposure. Tor encrypts and routes internet traffic through multiple relays, masking the user’s IP address and online activity from trackers and surveillance. This means users can browse sensitive content, communicate securely, or access restricted services without fear of profiling or monitoring.
Disable JavaScript and other potentially risky browser features unless necessary, as they can be exploited to reveal your identity. Avoid downloading files or opening attachments from unknown sources, as these can contain malware. Use strong, unique passwords and enable two-factor authentication where possible. The Tor Browser looks and feels similar to a regular web browser but is configured to prioritize privacy and security by default.
Top 10 Dark Web Search Engines Of 2025 For Safe & Private Access
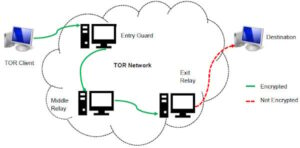
This is especially important for individuals in regions where press freedom is restricted or where government surveillance poses risks to journalists and activists. Unlike the surface web, where pages are easily searchable, dark web sites use encryption to hide their IP (Internet Protocol) addresses. This sequence offers less anonymity because your real IP address is still partially exposed along the Tor path. Plus, it’s slower since your data travels through the same four steps – entry node, relay node, exit node, and then the VPN server. It’s not illegal per se to access an onion website, but that doesn’t mean your actions while connected to the dark web are immune from law enforcement. It’s still illegal to commit crimes while connected to Tor, regardless of whether or not you think you’ll be caught.