Dark web monitoring scans hidden web networks like Tor and I2P for personal or corporate data, alerting users if any sensitive data is exposed. An organization can sometimes be the victim of a data breach without even realizing it. Dark web monitoring services can instantly identify this stolen information before it results in widespread damage to a company.
Searchlight Cyber Enhances Its DarkIQ Dark Web Traffic Monitoring Capabilities
- In addition to scanning for data breach information, a dark web monitoring service can be used to classify risks from unknown sources.
- Our team uses Breachsense data to gain initial access during pen testing and red team engagements.
- A research team investigating a data breach can use TorBot to efficiently gather and monitor relevant dark web pages, enhancing their ability to respond to threats effectively.
- Dark web monitoring searches the dark web for information about your organization, including leaked or stolen data, compromised or breached credentials, intellectual property, and other sensitive materials.
A major part of the service involves detecting accounts that have already been compromised. Experian offers Dark Web Surveillance through its Premium and Family memberships. These paid services also provide several other credit monitoring and identity theft features and protections. With Premium or Family memberships, Experian will scan 600,000 dark web pages every day and send you a notification if it finds potentially compromising information. The dark web is a hidden network of websites that requires a special web browser to access.

Monitor Dark Web Traffic: A Key Indicator Of Malicious Activity
Dark web monitoring helps you detect data breaches in your organization in real time, notifying you the moment there’s a mention of any sensitive information related to your organization. While you won’t be able to delete these mentions on the dark web, you will be able to apply preventative measures by canceling accounts, changing passwords, and so on, mitigating the potential damage. Using powerful NLP and OCR algorithms, we process data in all languages and formats, relying on autonomous translation and image-to-text extraction of content to deliver real-time insight into dark web threats. Leveraging advanced AI and ML algorithms, we index, correlate, analyze, tag and filter each bit of intelligence, enriching it with context about the nature, source and evolution of the threat.
Can Dark Web Monitoring Prevent Identity Theft?

IdentityForce, a TransUnion company, offers strong identity theft protection that includes Dark Web monitoring. Paid plans come with advanced monitoring features, a smart SSN tracker, junk mail opt-outs, and fast fraud alerts. Dark web monitoring is a legitimate service and can help in tracking cases of exposure. It can pinpoint instances where sensitive information is being stolen or leaked. Organizations can find out who are behind these data leaks or selling insider information for nefarious purposes by using various dark web monitoring tools. Dark web monitoring reveals loopholes and vulnerabilities that you can’t easily spot on the clear net.
- While this is offset by community support, it can be less reliable and less timely.
- In the 2021 Facebook data leak, a phishing scam led to the exposure of 533 million users’ phone numbers and personal details, which were later posted for free on Dark Web forums.
- Dark Web monitoring involves various techniques to detect and track stolen data.
- Fortunately, there are specific tools that can help you to keep you and your loved ones safe, and ensure that there is constant monitoring, even in the murkiest parts of the internet.
- Aura’s service does not monitor for all content or your child’s behavior in real time.
Stop Cyber Attacks Dead With DarkIQ: Our Dark Web Monitoring Tool
Schedule a demo to discover how Kaseya 365 keeps leaked data on the dark web from leading to account corruption and unwanted consequences. Kaseya’s Business Enablement Program is structured to support MSPs in adapting to the dynamic IT landscape while delivering premier client services. Tap into expert training, marketing assistance, and business consulting to elevate your offerings and maximize revenue. Google’s free tool goes a step further, offering people a button on the results about you page to request Google remove their personal information from search results as well. To make the best use of dark web intelligence, you want to be alerted only when new and relevant information emerges and be able to quickly determine what requires further investigation or escalation.
Cybersecurity Info You Can’t Live Without
Using dark web monitoring scanners, individuals and companies can proactively map, monitor, and reduce the rising digital threat landscape. They can protect their sensitive data, intellectual property, and brand reputation from emerging threats. Individuals can also take action, such as changing their passwords and boosting their privacy. The dark web is also a source of intelligence on the operations, tactics, and intent of criminal groups.
What Is Dark Web Monitoring And Do I Need It

Its comprehensive platform includes threat intelligence feeds, risk analysis, and incident response support. DarkOwl’s advanced analytics and machine learning capabilities help detect and prioritize threats, enabling proactive security measures. Its user-friendly dashboard allows for easy access to detailed reports and actionable insights. With its extensive coverage and advanced analytics, Digital Shadows helps detect compromised credentials, data leaks, and other malicious activities. Monitoring the dark web gives businesses and people helpful information about the areas of the internet where criminal activity is most prevalent. Organizations may proactively identify dangers, safeguard sensitive data, and defend their brand and assets by tracking and analyzing dark web material.
Best Laptops For Cybersecurity Students In 2025 The U
There are tools and services that monitor the dark web for compromised data and provide critical intelligence and visibility into areas of the dark web that are potentially outside your view. Several real data breaches showed the importance of dark web monitoring in maintaining corporate security. Compromised customer details, stolen financial data, and employee credentials usually get traded on these dark web forums. The following are some real-time examples that show how important dark web monitoring is for the cybersecurity strategy. Terbium Labs is a cybersecurity company specializing in dark web monitoring and threat intelligence. Their flagship product, Matchlight, provides continuous, automated monitoring of the dark web to detect the exposure of sensitive data.

The RedLine Stealer malware has been actively used to steal passwords and browser-stored credentials from thousands of victims worldwide. Infected users unknowingly provided hackers with access to their online banking and cryptocurrency accounts. The criteria for organisations to choose a suitable dark web monitoring service will vary depending on the specific business needs. However, here are the main factors to consider when you’re searching for a suitable tool for your business. A smart approach to dark web monitoring is to use dark web monitoring tools where much of the heavy lifting in exploring the dark web has already been done.

ZeroFox continuously monitors deep and dark web channels to detect and alert teams to information leakage and contextual analysis of cyberattacks. Flashpoint Ignite is an advanced threat intelligence platform designed to help organizations proactively detect, analyze, and respond to emerging cyber threats. Dark web monitoring software is a tool that can scan, identify, analyze, and report activities on the dark web that are relevant to your organization. Since this part of the internet is not indexed by standard search engines, threat actors often use it for illicit activities including buying and selling stolen sensitive information. The LastPass password manager also comes with an impressive dark web monitoring tool. It’s an add-on feature included in the Security Dashboard, which gives an overview of the health and security of the stored credentials.
Immuniweb Dark Web Monitoring Tool

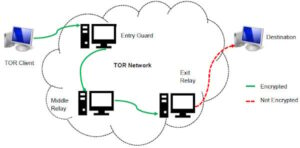
Cybersecurity teams encountering Tor IPs may need to adapt their approach for the dark web. Flare enables you to automatically scan the dark, deep, and clear web for leaked or stolen account credentials. In simple terms dark web scanners are services that identify and scour websites that buy, sell, and share stolen data. ACID Intelligence is a leading threat intelligence company that protects companies from cyberattacks on the dark web. It continuously scans and monitors the dark web forums and websites to detect attacks early in the planning stage. After in-depth analysis, it provides real-time information about the potential attacks targeting the organization.
Using a Dark Web scanner is one of the more reliable ways to check if you’ve been a victim in a data breach. This can give you a head start when it comes to avoiding follow-on cyber threats such as hacking, phishing, and malware attacks. Award-winning identity theft protection with AI-powered digital security tools, 24/7 White Glove support, and more. The presence of your data on dark web marketplaces indicates that criminals already have access to some of your information and may be actively planning to exploit it.