You can archive any site you want, or retrieve historical records wherever available. This was the price of a hacked account on the peer-to-peer exchange LocalBitcoins, which has since shut down. Unsurprisingly, facts about the Dark Web show that accounts on the more popular exchanges had higher asking prices. They ranged from $85 for a Blockchain.com account to $300 for a Crypto.com account to $1,170 for a Kraken account. Hacked and verified Wirex and N26 accounts commanded the highest prices — $2,300 and $2,650, respectively.

Legitimate Chrome VPN Extension Turns To Browser Spyware
ProPublica is a popular online publication that won five Pulitzers in 2016. It aims to expose abuses of power and betrayal of public trust through investigative journalism. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired. As a Premium user you get access to background information and details about the release of this statistic. As a Premium user you get access to the detailed source references and background information about this statistic.
Changing Prices In Payment Processing Services

The dark webmarket saw a rise in posts related to stealer malware, designed to pilfersensitive information such as login credentials, financial details, andpersonal data. Cybercriminals sell this data to other malicious actors foridentity theft, financial fraud, or other illicit activities. Last year, Kaspersky experts witnessed a significant uptick in stealers and extortion activities on the dark web market.
Encrypted Communication Tools
One way to see how authorities takedown the marketplace’s criminal infrastructure is to look at the example of intelligence gathering for Operation SpecTor. Manual monitoring of the dark web is inefficient and risky due to the sheer volume of data involved. This early detection allows organizations to identify and respond to threats quickly, reducing the chances of unauthorized access, financial loss, or damage to brand reputation. The market is especially well-known for providing access to freshly compromised data, often obtained from recent breaches and stealer logs. Since its inception, the market has catered to criminals looking for high-quality counterfeit items, such as fake IDs, passports, and branded luxury goods. FreshTools, founded in 2019, specializes in selling stolen account credentials and data, particularly webmail, RDPs (Remote Desktop Protocols), and cPanels.
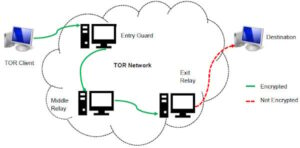
A VPN protects your connection against everyone, not just your ISP and the authorities. It encrypts your connection to prevent outsiders from being able to read your data and masks your IP address with one from a VPN server—so whoever’s looking can’t get any useful information. This process also prevents your ISP from seeing your data or where it’s going. Since the ISP can’t detect you’re accessing dark web URLs, it won’t trigger any alarms about your online activity. The deep web is the part of the internet you can’t access through search engines like Google and Bing. Also referred to as “non-indexed” content, it’s any content hidden behind some kind of access control such as a log-in or code word.
To expand their reach, some marketplaces established parallel channels on Telegram. This further complicates monitoring efforts because now you need to search for the related Telegram channels and track activity there and on the marketplace itself. As far as financial recourse for victims, some banks and insurance companies have provided payouts and will include those funds as damages in lawsuits against Genesis Market cybercriminals. As for Genesis Market cybercriminals located in the Netherlands, three have already been convicted and received prison sentences considered severe for that jurisdiction. The third convicted cybercriminal — the biggest Dutch user and the number 10 user worldwide — received a four-year sentence. By consistently applying these straightforward security tips, you can significantly mitigate risks and better protect your privacy, finances, and legal standing when interacting with dark-web marketplaces.
Exploring The World Of TV Series Dark: Analysis Of Symbolism
- Between January 2019 and September 2023, the majority of those queries came from underdeveloped countries with well-documented instances of internet censorship.
- In the case of a registered or reputable user, you may also receive a private address, which is used to increase the availability of the market in the event that the main address suffers a successful DDoS attack.
- He recommends verifying market employees carefully, and to weed out law enforcement infiltration through barium meal tests.
- In 2025, darknet markets continue to provide a secure and efficient platform for the trade of pharmaceuticals and recreational substances.
- Cryptomarkets on the darknet remain a key resource for those seeking privacy and efficiency in online trade.
- The only way to access the dark web is by using the correct browser and knowing the URLs of the pages you want to visit.
If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web. You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. Additionally, the rise of cryptomarkets has introduced innovative solutions for seamless transactions. These platforms utilize decentralized technologies to eliminate single points of failure, reducing the risk of shutdowns or data breaches.
FAQ: More About Onion Sites

“Dark” is a must-watch for anyone who loves sci-fi, mystery, or great television in general. Scammed funds are also increasingly moving through decentralized protocols. One of the most notable markets is PhantomX, which has gained popularity for its robust escrow system and multi-signature wallet integration. This ensures that funds are only released once both parties confirm the transaction, significantly reducing the risk of fraud. Additionally, PhantomX employs a decentralized hosting model, making it resistant to takedowns and ensuring continuous availability. Ruheni Mathenge specializes in writing long-form content dedicated to helping individuals and businesses navigate and understand the constantly evolving online security and web freedom worlds.
Can WiFi Owners See Your Internet History?
As the show progresses, the characters’ relationships and motivations become more complex, making for a compelling and immersive viewing experience. In terms of vendor behavior, the change is largely dominated by wholesale vendors. Meanwhile, retail vendors, who operate on a smaller scale, are holding more of their illicit earnings in personal wallets, delaying conversion to fiat to avoid detection. “Last year, DNM vendors sent a significantly higher portion of their funds to DeFi than they did historically,” the report read. In today’s digital era, where information is constantly on the move across all digital platforms, an… The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China.
Essentially, these payment processors provide a white label service for darknet markets and fraud shops, and a seamless checkout experience for those services’ customers. UAPS, shown in the chart above, is one such example of a payment processor that many fraud shops, including the OFAC-designated Genesis Market, used in 2023. The value received by UAPS in this chart includes payments sent to multiple fraud shops using the service as a payment processor.

The increased law enforcement activities of the past year are changing the landscape of cybercrime—one of the dark web trends about which we can all be happy. Usually, criminals sell access to exploits and stolen data, but increasingly sites such as 0day.today are releasing more free material, from exploits to data dumps. This is a popular dark web site that peddles software exploits which hackers can use to break into your computer or network.
In another study, Labrador et al. 24 evaluated multiple characteristics of selling products, vendors, and markets by implementing a custom crawler. This is often the reason why it is challenging to conduct large-scale longitudinal studies in dark web markets. Furthermore, Campobasso and Allodi 8 proposed a trainable, scalable crawler tool that makes it possible for researchers without computer backgrounds to use their tool for data collection in underground forums.
The market is also known for its listings related to financial fraud, such as phishing tools and stolen credit card information. Fake online casinos and social networks are common methods for distributing malware. To avoid infection, it’s best to avoid downloading anything from untrusted sources or websites. Criminals can use this data to impersonate people on the internet and even open online accounts in their names. The main reason why people purchase these accounts is to access content that is not available on their own accounts.
These attacks involve hackers gaining access to sensitive information and then demanding a ransom in exchange for not revealing or exposing it. It is important to note that engaging in any illegal activities on the dark web is highly risky and illegal, and users should exercise extreme caution and discretion. Join us as we explore the best dark web markets, revealing the secrets and dangers that lurk in its digital depths. Using a VPN when accessing the dark web adds an extra layer of security by encrypting your traffic and masking your IP address, making it harder for third parties to track your online activity. Using a VPN like Forest VPN not only enhances your security but also contributes positively to global causes.