Plus, there’s a thorough vetting process for new buyers and sellers to keep the community more secure. In a way, it feels more like a private club than an open market, and that’s exactly how the operators want it. The dark web is a hidden section of the internet that you cannot reach with common search engines like Bing or Google. The only way in is through the use of special software that renders all users anonymous and untraceable. A 27-year-old science teacher, Matthew Shaw, lost £3,500 in savings after selling his identity on the dark web for $10.
Moreover, 66% of migrating users choose to move their activity to the same coexisting marketplace. These markets also prioritize user feedback and reviews, allowing buyers to make informed decisions based on the experiences of others. The combination of advanced technology, user-centric design, and a commitment to privacy ensures that darknet markets remain a viable option for secure and reliable drug trade in 2025. The rise of verified market lists has further simplified access to these platforms, ensuring users can connect to legitimate and secure marketplaces without the risk of phishing or scams.
Security And Anonymity Features
Take the first step toward securing your business by exploring our solutions on Cybernod. Together, we can build a strong defense against the risks posed by the dark web and ensure your organization’s safety in the digital realm. Over the years, dozens of large DNMs have been established and eventually shut down by law enforcement, including AlphaBay, Dream Market, Wall Street, and, most recently, Hydra. DNMs are located on the “darknet,” which is unreachable on standard internet browsers like Chrome, Firefox, or Safari because the darknet is unindexed.
The Top 7 Dark Web Marketplaces In 2025

They’re hinting at going decentralized in 2025—less downtime, more trust, right in line with the decentralized trend. The site’s slick, with vendor stats updating live and a checkout that’s a breeze. I’ve used it a few times, and it’s never let me down—great for folks who like their dark web with a modern twist.
22 Password & Personal Identification Number (PIN)
For instance, cybercriminals can buy credit card details with a $5,000 balance for just $110. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. While hiring a hacker might sound like something out of a movie, it’s a very real threat. Businesses may use these services to sabotage their competitors, while individuals may seek revenge or simply want access to private information about someone. It’s also a marketplace for digital mercenaries; you’ll find everything from solo hackers offering their skills to well-organized groups that take on more complex or high-stakes projects. Some even have connections to criminal organizations and, in more serious cases, government-backed operations.
- But these efforts of law enforcement don’t go in vain; hackers and criminals lose trust if a website or marketplace goes down.
- It uses PGP encryption, two-factor authentication, and OPTP authentication to ensure users’ security.
- In 2025, this trend is expected to continue, pushing cybercriminals to adopt more sophisticated and anonymous operating models, such as closed, invitation-only forums.
- Sellers often need to pay a deposit to prove they’re serious, and they build their reputation through positive reviews.
- In the Bohemia market, there was betrayal and division within the operations team.
- Darknet markets operate within this hidden space, often hosting illegal activity, while the deep web primarily consists of everyday private or password-protected content.
Navigating Ransomware Attacks While Proactively Managing Cyber Risks
For each entity, we keep track of the cumulative values of the six features for each transaction performed by the entity over time. To be classified as a seller, an entity must simultaneously satisfy the six feature threshold criteria, as follows. 7, we show the largest component of the S2S network one year before the operation Bayonet and one year after. However, the evolution of the S2S network shows a different pattern than that observed in both the multiseller and the multibuyer networks.
Shaw, who was on holiday with his wife Davina, received a notification stating he had just paid £3,500 for a hotel room. He immediately called First Direct, who informed him that someone from Romania had opened an account in his name with a digital financial services company called Monese. The scammer linked Matthew’s details to his First Direct account to pay for a hotel.
DrugHub Market
Facebook’s onion mirror allows people to access it in countries that block the platform, allowing people to connect across digital borders. That said, the social network’s data collection and tracking practices may seem at odds with many of the principles motivating dark web users. Concerns about how Meta treats user data have led many people to delete their Facebook profiles or at least limit their social media presence. The CIA’s onion site allows users to securely report threats or suspicious activity, especially in regions where online surveillance is common. Its presence on the dark web also supports intelligence gathering and helps track cybercriminal activity.
🛡️ How Axis Intelligence Strengthens Cybersecurity
Their design mirrors legitimate e-commerce platforms, but their operations revolve around illegal products and services. The existence and operations of dark web markets underscore a growing challenge for cybersecurity. The tools and techniques used to keep these platforms running reveal vulnerabilities that businesses must guard against. Companies today face constant threats of data theft, intellectual property leaks, and other dangers that originate from the dark web.
Classification Of Sellers And Buyers
This weakness would make them more prone to being disrupted by a third party. This would often result in the loss of data and trust, which in turn might encourage users to switch to competitor markets. It is not only used to display the identity in the market, but also is part of the account security mechanism.

The marketplace is well-known for its bug bounty programs and robust security mechanisms, including mandatory 2FA. However, if we’re being honest, the majority of activity on darknet markets involves illegal or heavily regulated items. A 2020 study found that almost 57% of sites on the Tor network hosted some form of illegal content. In fact, everything is in English, and the site picks up users everywhere in the world.
They measured the response times in AlphaBay, and highlighted that the average response time for I2P was 5.6 s, which is faster than the 9.1 s for Tor. In 13, other researchers have shown that although I2P generally features better latency results than Tor, the latter seems to offer, in general, better throughput and download times than I2P. For example, Tor got to an average speed of 51 kB/s while I2P only got to approximately 13 kB/s.
Some are looking for illegal stuff they can’t buy elsewhere, like drugs or counterfeit documents. If you think the Dark web marketplaces are just online shops, you’re wrong — these sites are the actual weapon stores for criminals. They provide criminals with access to everything they need, from launching attacks to stealing data, etc. Just like on the regular internet, phishing is a big problem on the dark web as well. Fraudsters create fake versions of popular darknet sites to trick users into entering login details or personal data. If you fall for it and log in, they immediately steal your credentials and either sell or use them for other scams.
STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity. Although some of these markets prohibit certain extreme content such as violence or exploitation, most operate with very few rules beyond ensuring the security and anonymity of their users. Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024. In 2019, there were approximately 8,400 active sites on the dark web, selling thousands of products and services daily. However, you can trace its roots to the development of technologies like the Tor network or Freenet. In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet.

DrugHub Market: Categories, Listings, And Buying Process

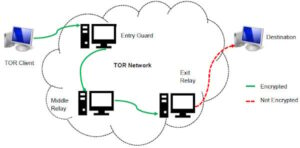
They offer anonymity to their users by using and developing specialized tools. DWMs are accessed through darknet browsers supporting the onion routing protocol (e.g., Tor), which provides anonymous communication connections35. Additionally, transactions are made with cryptocurrencies, mostly Bitcoin, which also provide anonymity to the transaction parties6,36.