There is no need to visit darknet marketplaces yourself to know whether your data was leaked. On one hand, it offers privacy for whistleblowers, journalists, and citizens in oppressive countries. On the other hand, it’s notorious for enabling illegal activity, including drug sales, weapons trafficking, counterfeit ID trading, hacking services, and the exchange of stolen personal data. This can include everything from full names, email logins, and passwords to credit card details, social security numbers, and bank account information.
However, Monero, on the other hand, is untraceable and the most trusted payment method on these markets. Therefore, most cybersecurity experts recommend using Monero while shopping on darknet markets. Some vendors offer services to help people “clean” illegally obtained funds using cryptocurrency and fake transactions. They mix and transfer funds through various privacy wallets and escrow services to hide the original source and make the illicit transactions harder to trace.
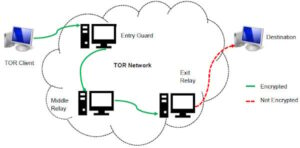
Use your common sense to steer clear of online scams and illegal activity. In the cryptic corners of the internet, a world thrives where privacy is paramount – the realm of anonymous markets. These online marketplaces, hidden from conventional search engines, operate in a secluded layer of the internet accessible only through specialized software like Tor. Here, a wide array of goods and services are exchanged, with a focus on privacy and anonymity. Behind the scenes of dark web transactions, various anonymity measures enhance the security of both users and their financial dealings.
Identifying Key Players In Dark Web Marketplaces Through Bitcoin Transaction Networks
While we highly recommend that you avoid such marketplaces, if you do want to visit one, make sure you use a VPN before connecting with Tor. Despite the rising popularity of the cryptocurrencies, it might still be a challenge to purchase them before placing an order. However, the majority of the darknet markets publishes an explicit guide with detailed instructions and a list of trusted wallets. Please note that accessing Darknet markets involves significant risks and illegal activities. Among the top 5 dark net marketplaces that security professionals are deeply concerned about, one name stands out – Cosmos Market. This hidden realm has gained a reputation for its extensive product listings and seamless user experience.
Government Monitoring

These collaborations increase the scope and impact of attacks, often targeting infrastructure, defense systems, and financial institutions. Rivalries between nation-state actors have also spilled into the dark web, with turf wars emerging between different sponsored groups over control of marketplaces and services. Government-sponsored hacking groups actively exploit the dark web for intelligence operations, financial gain, and sabotage. These groups use dark web platforms to sell stolen secrets, acquire hacking tools, or coordinate with other criminal organizations.
- The internet’s favorite alternative to Google made a name for itself by not logging your search activity yet still providing decent results.
- ProPublica is an investigative news site owned by an independent nonprofit that exposes abuses of power and corruption.
- SecureDrop is an open-source submission system that nonprofit organizations (NGOs), journalists, and news organizations can use to share and receive sensitive files securely.
- They can also take advantage of legitimate software to hide their tracks.
Did The Silk Road Marketplace Go Under?
Providing regular training on phishing prevention and cybersecurity best practices empowers employees to recognize and avoid potential threats. Dark web monitoring tools allow businesses to detect and respond to exposed credentials before they are exploited. These tools provide alerts about compromised information, enabling businesses to take immediate corrective actions, such as resetting passwords or disabling accounts. By proactively addressing vulnerabilities, SMEs can better protect themselves, maintain compliance with cybersecurity regulations, and minimize the likelihood of becoming a victim of dark web-related attacks. Data breaches also present a critical challenge, as stolen credentials allow attackers to infiltrate systems and extract sensitive information, including customer data and trade secrets.
How To Keep Track Of Evolving Darknet Marketplaces

However, you can trace its roots to the development of technologies like the Tor network or Freenet. In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet. This was the initial framework for anonymous communication and file sharing. Later in 2022, the US Naval Research Laboratory built on Freenet’s idea to create a secure and encrypted network for sensitive communications, which was later released to the public as open-source software.
Risks And Dangers

The Silk Road was the first popular DNM which appeared on the scene in back in 2011. Many other DNMs have sprung up since selling drugs, stolen merchandise, stolen information, and more. This early detection allows organizations to identify and respond to threats quickly, reducing the chances of unauthorized access, financial loss, or damage to brand reputation. The market is especially well-known for providing access to freshly compromised data, often obtained from recent breaches and stealer logs.
The Escrow Process
The dark web, a subset of the deep web, operates on encrypted networks like Tor, requiring specialized tools for access. Unlike the surface web, it’s not indexed by traditional search engines, making it a haven for anonymity seekers. In 2025, it hosts over 2.5 million active users daily, with markets facilitating billions in cryptocurrency transactions annually. Seizures of illegal crypto exchanges and marketplaces have made headlines. Government agencies have shut down platforms used for laundering cryptocurrency obtained through ransomware and fraud.
- I tested it 10+ times, and it always provided me with accurate search results.
- Unlike the surface web, it’s not indexed by traditional search engines, making it a haven for anonymity seekers.
- Today, many organizations exist that are created only to handle these reports anonymously and effectively.
- The Onion Project, or TOR is the predominant anonymous computer network.
- It’s a hidden collective of sites that you could only access through a special browser.
- While hiring a hacker might sound like something out of a movie, it’s a very real threat.
New darknet sites and markets continuously emerge to replace those that get shut down. The technology behind the darknet is actively maintained and continues to evolve. The dark web is a small part of the much larger “deep web,” which also isn’t indexed by search engines — but authorized users can access it using common web browsers. The deep web is made up of email platforms, workplace portals, subscription services, and banking websites — basically anything that requires a login. The “surface web,” on the other hand, is the publicly available part of the internet that search engines index. Dark web marketplaces are online marketplaces where people can buy and sell illicit goods and services under the protection of the anonymity of the dark web.

One of the biggest problems cybersecurity teams face isn’t a lack of tools — it’s too many alerts. And beware—while many explore out of curiosity or for research purposes, it’s important to remember that engaging with these platforms, even as an observer, can lead to serious legal and ethical consequences. Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data.
With 12,000+ users and 900+ vendors, it boasts a 95% vendor rating—ideal for quality-focused dark pool trading. Despite consistent results, this study has limitations that may be addressed in future work. First, while the dataset is preprocessed with state-of-the-art methods, there is no ground truth for validation, and this uncertainty propagates to our findings.
These platforms facilitate illicit trade, threatening personal security and national safety while fostering an environment of distrust. As cybercriminals continue to evolve, your awareness and proactive measures become necessary in safeguarding yourself and your community from the insidious effects of these dangerous marketplaces. Trends in emerging technologies point to enhanced security measures that can make dark web marketplaces more resilient against takedowns. You may encounter artificial intelligence being employed to analyze user behavior, potentially increasing the risk of exploitation for unsuspecting users.
Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault. Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC. Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide. Law enforcement officials are getting better at finding and prosecuting owners of sites that sell illicit goods and services. In the summer of 2017, a team of cyber cops from three countries successfully shut down AlphaBay, the dark web’s largest source of contraband, sending shudders throughout the network. Dark web surveillance involves monitoring information on the darknet, such as to identify compromised credentials being sold, or to track forums to anticipate (and prevent) cyberattacks.
Essential Security Tips For Using Dark-Web Marketplaces
Many need to cross international borders, and customs officials are cracking down on suspicious packages. The dark web news site Deep.Dot.Web teems with stories of buyers who have been arrested or jailed for attempted purchases. Still, for those willing to put up with the inconvenience, the dark web provides a memorable glimpse at the seamy underbelly of the human experience – without the risk of skulking around in a dark alley. IBM Security X-Force, for example, reported that 29% of its ransomware engagements in 2020 involved REvil. The criminal groups that developed the malware gets a cut of the affiliates’ earnings, typically between 20% and 30%.