This encryption makes attribution and tracking more difficult for authorities and cybersecurity professionals. Conversely, transaction networks obtained from the blockchain contain the entire transaction data of the DWMs and U2U transactions, allowing a thorough investigation of the ecosystem as a whole. In fact, previous studies on DWM transaction networks have revealed crucial aspects of the ecosystem13,14,15.
You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom. Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It is a component of Whonix, an operating system that functions as a whole inside a virtual computer. It includes all the essential productivity software, including MS Word and an email client. The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address.
Common Scams And Fraudulent Activities On Darknet Markets
Even people with zero technical knowledge can buy phishing kits, ransomware, or stolen logins. If for any reason, you decide to visit these hidden corners of the web, ensure you at least study and understand the common traps. Getting familiar with the tactics scammers use will go a long way in helping you protect your online data and assets. Too-good-to-be-true investment offers are another classic scam on the dark web. Early participants may see some profit, but that money usually comes from new victims, not actual earnings.
How Do Dark Web Markets Work?
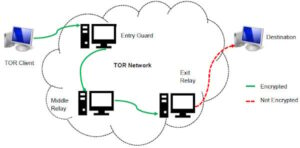
To access this marketplace, you must register, but before that, you must verify yourself as a human by passing a CAPTCHA test. These sites cater to cybercriminals seeking valuable data, such as credit card numbers, login credentials, and personal information. However, you can trace its roots to the development of technologies like the Tor network or Freenet. In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet. This was the initial framework for anonymous communication and file sharing. Later in 2022, the US Naval Research Laboratory built on Freenet’s idea to create a secure and encrypted network for sensitive communications, which was later released to the public as open-source software.
Top 5 Best Dark Web Marketplaces
When most people refer to the dark web, they are thinking about dark web/darknet marketplaces (DNMs). These are the primary sources of what the general public thinks of as “dark web.” Online marketplaces selling hacked credit cards, fake passports, malware kits, untraceable drugs, anything. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for.
- Then, you can set up 2FA (two-factor authentication) for that extra touch of security in case someone somehow figures out your password.
- Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced sanctions against Parsarad for his role as the administrator of Nemesis Market.
- In this era, it takes one wrong click and all your sensitive data ends up in the wrong hands.
- Since then, he has dedicated his career to writing extensively about crucial infosec, data privacy, and cybersecurity topics.
Features That Make WTN Market A Secure Platform
- The police referred to him only as Julian K. Shortly after Julian K.’s arrest, DarkMarket was shuttered by the German police.
- As cyber threats originating from the Dark Web continue to evolve, businesses—especially small and medium-sized enterprises (SMBs)—must implement proactive security measures to safeguard their sensitive data.
- These platforms also often have built-in encryption for communications and transactions, making it hard for law enforcement to track down the individuals involved.
- Buyers won’t come to the site if there’s nothing to buy, and sellers won’t come to the site if there’s no one to buy their products.
- Accessing blocked content can result in being placed on a watch list or imprisonment.
Indeed, some began life on the clear web before migrating to the dark web to evade surveillance or censorship. Forums cover the breadth of criminal activity but these examples show there is a particularly thriving community of cybercriminals sharing information, tutorials, access, and exploits. Onion sites can be safe in terms of privacy protection due to strong encryption, but they also host a significant amount of illegal content and scams. It’s important to only visit trusted sites and avoid clicking on suspicious links. Discover how to safely access dark web marketplace links while ensuring your privacy and security online.
Beware of sharing your financial details on the dark web, as this can result in identity theft and your bank account amount being stolen. The Torrez market is one of the biggest dark net marketplaces, also called a community-driven marketplace. It contains a good selection of product listings that range over 35,000 items.
For example, an insider or factory employee might quietly slip away with an unmarked gun and sell it online. Once it lands on a darknet marketplace, it becomes part of the illegal weapons trade. The site gives out free samples of the stolen data every now and then to gain more customers. With its fast rise to fame and focus on money fraud, it’s no surprise that cybersecurity experts are keeping a very close eye on this one.
The market offers things like malware, fake documents, and financial fraud services. This market is not open to the general public and is subject to a thorough vetting process to ensure its security. In fact, WeTheNorth is more of a private club than an open market – something its operators want. The first thing on the minds of many users when it comes to the dark web environment is illegal drugs. In fact, the Guardian referred to darknet markets as “the eBay of drug dealing,” and rightly so, illegal drugs are found in almost all the shops on the dark web. There are some things that you can’t find on the surface internet but are available in the darknet markets.
Exploring The Hidden Layers Of The Internet: Surface Web, Deep Web, And Dark Web
These software are also capable of launching DDoS attacks and phishing campaigns. Once many users begin to rely on the site and store funds in escrow, the operators disappear, taking all the money with them and leaving their customers and clients with nothing. Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit.

For instance, we cannot verify if an entity classified as seller is in fact a seller. Similarly, there is no unique choice for the classification parameters or ground truth for fitting them. In light of this, we have chosen the parameters conservatively, obtaining estimates for the number of sellers that are in general smaller than the ones produced by other methods. Second, our approach does not explicitly classify buyers, which are entities that were not classified as sellers. There is a gray zone in which some sellers and buyers may not be easily distinguishable in transaction networks. For instance, there may be sellers that make a small amount of transactions, or spend more than receive, which we would classify as buyers.

The Evolving Dynamics Of The Dark Web: Enterprise Security Implications
You can find a lot of goods and services packed with stealth high-level encryption, no JavaScript, and anti-DDoS protection. The dark web itself is not illegal, but it’s largely connected with unscrupulous and illegal operations. It is used by many for buying or selling items that are prohibited on the regular internet, like fake IDs, illegal drugs, and stolen data. In a world where data is a valuable asset and cyber threats evolve rapidly, understanding how dark web marketplaces operate is essential.

The Best Dark Web Markets To Consider In 2025
The social media giant is also aware of the many attempts by repressive regimes to restrict its access. After all, it enables users to connect and communicate with each other from around the world. Ransomware leak sites are publicity sites where ransomware groups share the details of their latest victims. However, they also play an important role in how these groups orchestrate and monetize their attacks.
Disable Java And ActiveX In Your Network Settings
Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites. The Dark Web Hub equips law enforcement, enterprises, MSSPs, and researchers with essential knowledge to navigate dark web threats. The strategies used by law enforcement to dismantle these marketplaces involve a mix of advanced technologies and old-fashioned detective work.
Best Dark Web Marketplaces Security Professionals Are Really Worried About
For a local machine configuration, he recommends a computer purchased for cash running Linux, using a local Tor transparent proxy. For operations security he suggests avoiding storing conversation logs, varying writing styles, avoiding mobile phone-based tracking and leaking false personal details to further obfuscate one’s identity. Since 2020, 2easy has sold massive stealer logs with sensitive data like passwords, bank cards, and initial access credentials. It supports operations in multiple languages and operates on both clearnet and Tor. Russian Market has consistently remained one of the most popular and valuable data stores on the dark web. Its affordability and reliability have earned it a loyal customer base.