This search field allows you to perform regular, but now anonymized, web searches through DuckDuckGo’s Tor site. Prior to Keeper, Darren served as an advisor to JiWire, now called NinthDecimal. NinthDecimal is the leading media and technology service provider for the WiFi industry. He was formerly the Chief Financial Officer and a principal shareholder of Apollo Solutions, Inc., which was acquired by CNET Networks.
How To Access The Dark Web
Funnily enough, the deep web is the largest part of the internet! It’s online and you can access it but your friend or family can’t. This is usually done to prevent tracking and website shutdowns typical for this part of the internet. The trick with these onion websites is their accessibility, which is made possible only with Tor. Tor is an abbreviation for The Onion Router and now, we can see why.
Potential Malware
- Law enforcers can use custom software to infiltrate the dark web and analyze activities.
- The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China.
- You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom.
- And though some dark web marketplaces offer user reviews, not all do.
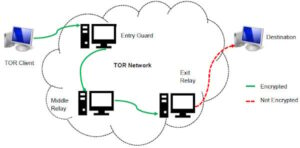
Millions of customers’ personal data, including names, addresses, bank account and credit card account information, and many other forms of sensitive data. The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. The core principle of the Tor network was first developed by U.S. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online. The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose.
While many dark web websites, like the former black market website Silk Road, are used to facilitate criminal activity, there are also plenty of legitimate dark web websites. ProPublica is a non-profit, Pulitzer Prize-winning news outlet that focuses on abuses of power and issues of public trust. ProPublica’s investigative journalism can upset powerful interests, so the outlet joined the dark web to help their journalists and readers access their content anonymously.
Learn how to safely access the dark web with this comprehensive guide for beginners. Remember, the Tor browser connects to the internet differently than regular browsers in an attempt to increase your anonymity online. These URLs are usually very long, consisting of a random jumble of letters and numbers. Though you likely won’t remember the addresses of onion websites, you can find these URLs on various websites on the internet. Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault. Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC.
We also prefer this method because of VPN’s all-encompassing security. This allows you to go online anonymously and without ISP monitoring. The key is to encrypt your traffic BEFORE you use Tor so that your ISP (Internet Service Provider) doesn’t see you’re in the Tor network. You can go on the dark web safely, use legal sites, and enjoy the experience without worries.

How To Access The Dark Web On Android And IOS
Malicious actors and government agencies can run Tor nodes, compromising privacy and security. In fact, there have been instances where attackers controlled hundreds of Tor nodes. Many people use it for privacy-focused communication, whistleblowing, or accessing restricted information in censorship-heavy regions.

Which Wallet Best For Darknet Market

The actor connected from an unknown VM and authenticated to multiple services via the USER1 account. The actor authenticated to multiple services from a compromised Global Domain Administrator account (USER2). The actor also authenticated to the Common Internet File Service (CIFS) on various endpoints.
Swap Data In Countries That Censor The Internet
However, it is important to note that not all websites on the Dark Web are illegal or malicious. There are legitimate uses for the Dark Web, such as anonymous communication and accessing information in countries with strict internet censorship. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites. You can access many other sites via the Tor browser, and your requests will be routed through multiple servers to avoid monitoring.

Can I Access Dark Web Websites On Mobile?
The dark web allows people to access and share all sorts of illegal and explicit material without judgment or censorship. The best way to find out is to check the “Have I Been Pwned” (HIBP) website. This website allows you to type in your email address or phone number and see if it’s been compromised in any data breaches.
How To Access The Dark Web Safely: A 2025 Beginner’s Guide
Unlike the surface web, you can’t access deep web resources directly through a search engine; they require login credentials or special permissions. In many places, including the U.S., the UK, and the EU, accessing the dark web is legal for legitimate purposes. However, many sites on the dark web host illegal content or activities, and engaging with those can lead to serious legal consequences.
Tor Over VPN
Websites on the dark web have .onion addresses, and they operate differently from regular sites. However, many activities conducted on the dark web may be illegal, so it’s important to stay informed and cautious while navigating. With the right tools like Forest VPN and the Tor browser, you can navigate this hidden part of the internet with enhanced security and peace of mind. Always prioritize your safety and stay informed to enjoy a secure browsing experience.

This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.
ZLibrary hosts free file-sharing access to academic texts, scholarly articles, and general-interest books. It often hosts copyrighted materials without permission, violating many countries’ copyright laws. Downloading or distributing such material is against the law and can have legal consequences.