It offers a secure and anonymous way to handle transactions on the dark web. While it is not free, the small fee is a fair trade for the privacy and reliability it provides. Following these precautions and being mindful of ethical use cases will allow you to navigate the dark web more safely. Always monitor potential threats and stay aware of the risks involved. The surface web—which we use for searching day-to-day information—is only its tip. Many more layers of hidden content can be found below—in the deep and dark web.
Can You Be Traced On Tor?
This group is tied to the broader BidenCash ecosystem and focuses on discussions around stolen financial data. Members exchange tips on using compromised credit cards, highlight recent data dumps, and discuss market-related updates. BidenCash is known for releasing large batches of credit card information publicly to attract buyers, with one of the most recent leaks exceeding 900,000 cards. Many cybercriminal groups announced their support for Durov and continue to rely on Telegram’s strong encryption and familiar infrastructure. There are many other channels on Telegram as well the other arrays of life, which serve as a great source of entertainment and information for Telegram users.
Search Engine List – Onion Links (
It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself. Hackers spend a lot of time on the dark web, and it’s not too difficult to get access to hacking tools and data leaks in this part of the internet. However, it’s much harder to get at the people who are doing the uploading and downloading. Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for.
News & Whistleblowing
I have to admit to having a soft spot for Tunnels, an onion website about underground “urban” exploration. Apart from having that “As above, so below” vibe, Tunnels is a great source of info for users who are into dark urban history. The website contains pictures and videos of various cavern-like structures, shafts, and possibly escape tunnels.
Related Articles From The Safe Browsing Section
You risk landing on malicious pages with phishing, malware, or illegal content. Candle is a lightweight, open-source dark web search engine with basic search functionality and high speed. Due to law enforcement takedowns and security reasons, .onion addresses are frequently rotated. One of the most insidious dangers on the dark web is not just technical malware or hidden exploits, but the human element—scammers and con artists who rely on psychological manipulation.
Absence Of Malicious Content And Practices
This added layer of security keeps your identity hidden and shields you from online threats. They help users find real dark web links, verify them through uptime tracking, and avoid dangerous clones. Whether you’re browsing out of curiosity or pursuing sensitive research, using dark web sites that are safe in 2025 is a matter of both security and responsibility. Many directories are outdated or cloned, while others include malicious .onion addresses. That’s why we’ve hand-picked twelve trusted .onion sites that continue to provide value, privacy, and reliability.
Dark Web Links For News
Different dark web search engines cater to various needs, offering varying levels of privacy, security, and ease of use. Venus crawls and gathers a wide array of onion sites, ensuring you have access to the latest information available on the dark web. The search engine doesn’t impose censorship, meaning you can find a broad spectrum of sites, including those that may be illegal or disturbing. OnionLand offers a clean design with a simple user interface that includes search suggestions. The search engine allows you to look for old V2 onion addresses, images, and content on I2P.
Lastly, many .onion services shut down intentionally, either temporarily or permanently. Operators might close their sites due to security concerns, legal risks, lack of funding, or shifting priorities. In some cases, they deliberately relocate to different .onion addresses to enhance security, evade detection, or maintain anonymity, leaving behind outdated and inactive links. Torch is one of the oldest dark web search engines, and it’s generally considered one of the safest. It has some advertisements on its home page, but they’re for popular searches and services to help get you started. It has indexed more than 1.5 billion pages from over 260,000 .onion websites, so you’ll easily be able to find what you’re looking for.
Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe. Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. Activists and government critics prefer to remain anonymous, fearing repercussions if their identities are revealed. Besides, victims of crime may want to hide their identities from their perpetrators. Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble.
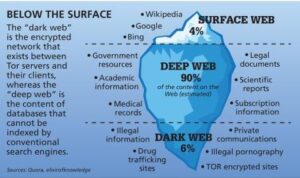
Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.

🕶️Staying Anonymous On The Dark Web
- While some of these markets operate legally within certain jurisdictions, many are known for illegal activity.
- For these reasons, it’s a good idea to safeguard your online activities with NordVPN while using the dark web.
- The BBC, among others, is blocked in countries like North Korea or China because of the government’s strict censorship policies.
- While its name may indicate danger, the dark web can actually be a safe place.
OnionName lets you generate an .onion domain name that starts with a specific keyword — like onionamev33r7w4zckyttobq3vrt725iuyr6xessihxifhxrhupixqad.onion/, which is OnionName’s dark web link. The keyword in that example is “onioname,” which is right at the start of the .onion link. With a readable site name like that, people will know what to expect when they click on the link. The website has received six Pulitzer Prizes for its grassroots-based journalism.

Onion Links: How To Access Them
Our mission is to offer reliable tech help and credible, practical, science-based life advice to help you live better. As I’ve previously said, it’s a good idea to keep your interactions with the dark web to a minimum, unless you can absolutely trust the people you’re dealing with. You’ll often see a sign in stores that says “look, don’t touch,” and it’s not a bad adage to bear in mind as you navigate around the dark web. For obvious reasons—I don’t want to get you or me into trouble, after all—I’m not going to get too specific when it comes to what you can find for sale on the dark web. A lot of transactions are handled via cryptocurrencies such as Bitcoin, which is relatively (but not completely) private and anonymous.


The extra connection layers can act as a significant burden to your browsing experience if you’re doing something that is bandwidth intensive. As we mentioned above, when you connect to Tor your data first goes through an entry node, which can see your IP address. By connecting to a VPN before using Tor, you mask your real IP address before it reaches this entry node, adding an extra layer of security and anonymity.
- Just like Facebook, this is no random namesake; it is a legitimate platform from which to reach the CIA anonymously.
- It’s a hidden collective of sites that you could only access through a special browser.
- Put simply, the dark web refers to websites that have their IP addresses hidden or disguised.
- This network of more than 6,000 relays conceals the user’s location from anybody engaging in online surveillance, as well as the websites visited.
Hidden networks also host a range of resources that can inform, educate, and support individuals who value anonymity. From uncensored libraries to secure whistleblowing channels, these platforms can offer benefits difficult to find on the clear web. This article aims to shed light on the more constructive side of the dark web, guiding readers toward reputable resources and reliable information.