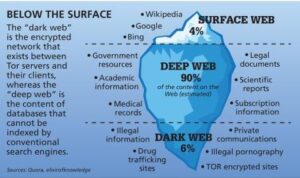
A piece of Deep Web is the Dark Web which can only be accessed through browsers like Tor and Freenet for navigation. Though using the Tor is completely legal and legitimate but there is some content that cannot be accessed as it is a punishable offence. The size of the Deep Web surpasses the Surface Web while remaining secure as an Internet zone. Almost 90% of all the websites are on Deep Web and are majorly used by Government agencies, corporations amongst others. These websites are protected behind the security walls, authentication form and password.
How Does Tor Browser Work?
I hope that now you have certainly got knowledge relating to access to the dark web in India. Now you probably won’t go and access the dark web if you want to live an easy life without any problematic hassles from the world of the dark web. India needs strong cyber laws and provisions in the Indian Penal Code, 1860.
- While it offers anonymity and privacy, these benefits come with considerable dangers, including exposure to illegal content, cybersecurity threats, and potential legal consequences.
- However, the dark web is also known for being a hub for illicit activity.
- In fact, these supposed “dark web” browsers are not tethered exclusively to this portion of the internet.
- The dark web is a common gathering place for hackers and other cybercriminals, which can make browsing the dark web a risky activity.
Tracking Cryptocurrency Transactions

Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for. You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe.
Silk Road And The Birth Of Illegal Marketplaces

Law enforcement agencies in many countries monitor the dark web to combat illegal activities. Cracking down on many illegal marketplaces on the dark web is the result of such monitoring. So, you risk being flagged or investigated for visiting certain sites, even without criminal intent. Policing involves targeting specific activities of the private web deemed illegal or subject to internet censorship.
Protect Yourself Online

You are not required to provide your personal information to create an account. The email service is available both on the surface and on the dark web. The BBC news website has a special .onion site, which you need to access via the dark web. Its goal is to offer anonymous access to the content without being censored, no matter where you live.
How To Protect Yourself From The Dark Web
However, there are browsers that are developed for the dark web, such as the Tor Browser. But the process is not as simple as that, there are safety measures and privacy concerns that should be taken into consideration. To be on the safe side, we recommend combining the Tor or onion browser with a secure VPN, such as NordVPN. When used in unison, these tools seal the security and privacy vulnerabilities of the Tor network, keeping you anonymous as you roam the streets of the dark web. No, the dark web isn’t illegal, but what you do while in the underbelly of the internet matters. A lot of illegal activity takes place on the dark web, and engaging in any of that activity can be a criminal offense.
Risks And Precautions
Websites are usually labeled with registry operators like “.com” and “.org” and can be easily located with popular search engines. If your work or lifestyle requires you to use the dark web, however, there are ways to protect yourself. Just as you need the right tools to access the dark web, you also need the right protections to be able to stay safe on it. The dark web isn’t entirely bad, but it’s clear that it can be deeply dangerous. It’s a hotbed of crime — both physical and digital — and anyone who dares enter it would be exposing themselves to those dangers. That’s why, as cybersecurity experts and safety advocates, we don’t recommend accessing the dark web.
For this reason, you cannot browse through these sites using your default search engine. Established in 2012, the platform is a time capsule that collects snapshots of websites. These onion addresses will remain online even if the original page disappears.
It includes all the essential productivity software, including MS Word and an email client. The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. I2P, or the Invisible Internet Project, allows you to access the ordinary and dark web.

As you can probably imagine, that’s exactly what threat actors on the internet want to hide their nefarious deeds. A repository of sites that can’t be found by traditional search engines, the dark web is as intriguing as it is dangerous. We take a deep dive into what the dark web is and the dangers it poses. That said, many of the actors on the dark web are highly skilled digital adversaries who can easily outmaneuver basic security measures. As a leading cybersecurity vendor, CrowdStrike cautions all organizations and individuals to refrain from using the dark web. Bitcoin is the most widely recognized and utilized cryptocurrency on the dark web.

In the summer of 2017, a team of cyber cops from three countries successfully shut down AlphaBay, the dark web’s largest source of contraband, sending shudders throughout the network. Dark web websites look pretty much like any other site, but there are important differences. That’s “a special-use top level domain suffix designating an anonymous hidden service reachable via the Tor network,” according to Wikipedia. Browsers with the appropriate proxy can reach these sites, but others can’t.
It offers a Reddit-like interface, where you can learn everything you need to know about darknet websites and spotting the real from the scammers. For the record, there are more scam sites for every genuine one, and it’s good to have a discussion forum about this. One must always keep their tools, softwares, and operating systems up to date. Computer systems that are unpatched against undiscovered holes in their programming, are more likely to be vulnerable and affected by scams, hacking and other such issues. Software developers regularly investigate such weaknesses and let out updates when it comes to such issues and one must always protect their devices by regularly accepting these updates. At times, the individual may be charged with both, i.e., imprisonment and a fine.
- As per these Rules, companies that store personal, sensitive data of individuals must take certain measures and follow proper security standards to safeguard it from being hacked or leaked.
- While there are other browsers you can use to get on the dark web, Tor is usually recommended as the best for most people in terms of the features it offers and the ease with which anyone can make use of it.
- The dark web is filled with information theft from malware-infected users.
- People living in countries with internet censorship can access news through these websites as they are untraceable due to high security.
- Naval Research Lab as a system of decentralized, anonymous nodes to enable anonymous online communication.
- The takedown of AlphaBay, a major dark web marketplace, was achieved through international cooperation, demonstrating the importance of cross-border collaboration.
What Are Some Regulatory Challenges Faced By Authorities And Agencies Relating To The Dark Web?
Note that Hidden Wiki links sometimes lead to unsafe content, so be wary about what you click. Use your common sense to steer clear of online scams and illegal activity. A dark web browser, like the Tor browser, is designed to access hidden networks. It routes traffic through several encrypted nodes, concealing user identity and location. These browsers grant access to.onion sites not indexed by normal search engines, allowing anonymous browsing.
Some individuals access the dark web to share sensitive information or leak documents without actually revealing their true identity. Several platforms (one of them being SecureDrop) allow whistleblowers to pass on sensitive information securely, to journalists. The dark web started to become known to the Indian public when there was an increase in cybercrime all across the world. As the internet became widespread, so did the awareness and usage of the dark web, for numerous reasons, which were both legal and illegal. In the early 2010s, India saw the emergence of dark web marketplaces, which were quite similar to those seen globally, such as the Silk Road. Staying informed and making informed decisions are key to navigating the dark web responsibly.