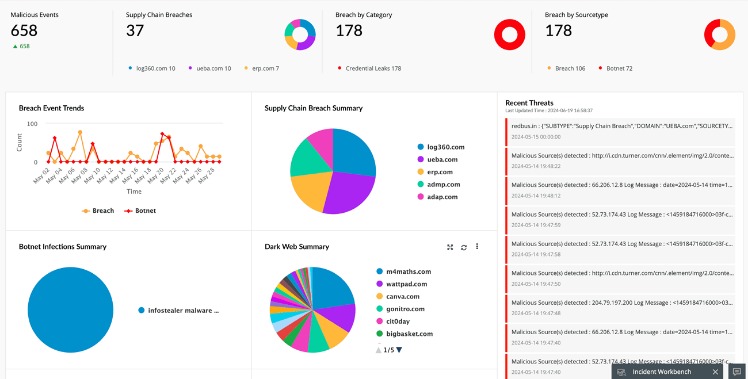
So, instead of “facebook.com”, the URL can look like “12ls834mfdg8.onion”. Download Tor Browser to experience real private browsing without tracking, surveillance, or censorship. With Tor Browser, you are free to access sites your home network may have blocked. In today’s digital era, where information is constantly on the move across all digital platforms, an…
Risks And Dangers Of The Dark Web

Hidden, encrypted and out of reach of traditional search engines, the dark web is a place where anonymity rules. Users slip into this shadowy realm using a anonymizing browser, like Tor (The Onion Ring) browser, and a Virtual Private Network (VPN) to protect their identity and secure their connection. However, the software that popularized the dark web is The Onion Router (Tor), which launched on September 20, 2002. The U.S. government’s Naval Research Laboratory developed Tor for members of the U.S. intelligence community to use the Internet without risk of identification. Before we explain how to venture into this part of the internet, we need to see what you’re setting yourself up for.
Security solutions like anti-virus software protect your system and network from malware and other threats. The dark web, being a hub for criminal activities like identity theft and malware distribution, exposes you to various security threats like malware or phishing. While Tor offers anonymity by routing your traffic through a decentralized network of nodes (onion routing), it shouldn’t be your only line of defense for privacy. Malicious actors and government agencies can run Tor nodes, compromising privacy and security. In fact, there have been instances where attackers controlled hundreds of Tor nodes.

It’s easy to move your data away from Google Drive to services like Proton Drive, which automatically secures your files with end-to-end encryption. With our Google Drive alternative, you remain in control even after you share a file with others by limiting who can access it with password protection. While Google Chrome is popular, it’s also known for collecting significant amounts of user data. Alternative browsers like Brave, Tor Browser, and Mozilla Firefox will allow you to keep your online activity private. However, even our free accounts provide you with strong privacy protections not available from Big Tech. Your messages and data are protected with end-to-end and zero-access encryption, meaning no one can access your most valuable, sensitive data — not even us.
VPN Over Tor
- Despite this, there may be legitimate reasons people choose to use the dark web, including political dissidents and those who want to keep certain information private.
- If you’re unsure about the legal boundaries in your country, consulting a knowledgeable attorney or reviewing reputable sources of legal information is a prudent first step.
- Many people install a VPN as well, but then you’re putting your trust in an additional third party to not track your activities or report them to anyone else.
- And though some dark web marketplaces offer user reviews, not all do.
These settings can be found in the Router Console’s configuration panel. Accessing the Tor network through Tails OS (The Amnesic Incognito Live System) on a thumb drive is a highly secure way to browse the dark web anonymously. Tails is a portable operating system specifically designed for privacy, and it includes the Tor Browser by default. Here’s a step-by-step guide to setting up Tails on a USB thumb drive and using it to access Tor.
Ways Small To Midsize Businesses Can Stay Safe In The Cloud
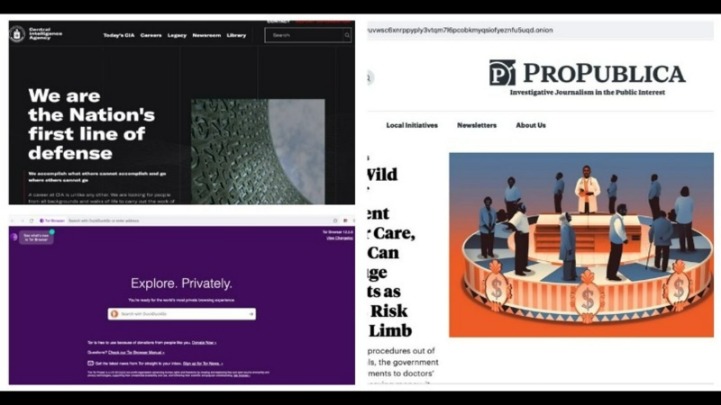
You might visit the dark web seeking anonymity or unique services, but this anonymity also attracts scammers. You may encounter fake marketplaces promising illicit goods or services but delivering nothing after payment. As dark web websites are not moderated, they can host a wide range of malware, such as ransomware, keylogger, and remote access Trojan. You can inadvertently download malicious software by visiting these websites, infecting your system.
Privacy-focused search engines like Brave Search, Qwant, and Kagi don’t track you or collect your personal data to target you with ads. From search engines to messaging apps, browsers to cloud storage, other European alternatives can give you the tools to take back control. Also known as the “surface web”, the clear web is the World Wide Web(new window) we’re all familiar with. It’s a collection of websites connected to each other via hyperlinks that are easily searchable using search engines such as Google. Indeed, Proton offers an onion dark web version of our website so that people in some of the most repressive parts of the world can access our services.
Our Network
The content of all these pages is stored on Google’s servers, but it’s mostly outdated, old content; smartphone app content; journals; court records; private social media profiles, and much more. Therefore, you should understand the legal risks of accessing the dark web before you venture into this murky world. On the surface web, you can contact your credit card company or law enforcement for help.
How To Minimize Risks:
Dark web monitoring platforms provide secure communication channels for individuals seeking to expose information without fear of retribution. Additionally, the Dark Web serves as a haven for those in censored environments, offering access to restricted information and enabling the free expression of opinions. To access the dark web safely, it’s necessary to use a dark web browser like Tor in combination with trusted dark web directories and search engines to help you find reliable sites. You should also make sure your device is protected by strong antivirus software, and consider using a VPN to mask your activity on the dark web. The deep web refers to any web content that is not indexed or pages that can’t be found with a search engine.
Myth: It’s Entirely Illegal
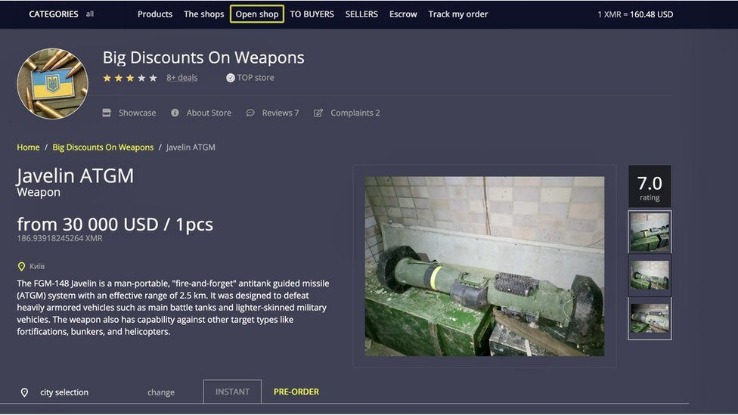
If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites. Another great source to find and explore dark web marketplaces or other sections is to visit Reddit’s resourceful forum. You can look for information on /r/deepweb, /r/TOR, or /r/onions, of which the latter is useful to find hidden wikis and more. Many of these Reddits have rules prohibiting linking to illegal sites and services, so you likely won’t find anything illegal there. Social networks, such as Facebook, have created dark web versions of their sites to address privacy problems related to their surface web versions.

To safeguard yourself against phishing, fraud, and other threats, it’s crucial to verify the authenticity of links before engaging with any dark web platform. When delving into the dark web, maintaining stringent security and preserving your anonymity aren’t just advisable—they’re essential. Threats here range from malicious actors looking to harvest your personal data to hidden exploits designed to compromise your system. A careless misstep can lead to exposure, malware infection, or worse. To protect yourself, it’s crucial to combine multiple security layers, stay vigilant, and adopt best practices tailored for the hidden corners of the internet.
Initially designed for secure military communications, it evolved into a broader tool for online anonymity, later expanding to public use with the Tor network. Many dark internet users favor Tor which uses a network architecture originally developed by the U.S. Naval Research Lab as a system of decentralized, anonymous nodes to enable anonymous online communication. When accessing the dark web, the first step is to install a dark web-friendly browser on your computer.
The following are key risks of accessing the dark web you should be aware of. ZDNET tested the best VPNs available based on speed, number of servers, security features, price, and more. ExpressVPN is our pick for the best VPN overall, thanks to its fast and reliable connection and the wide range of platforms it works on. No longer restricted to dial-up, many of us now consider access to a stable high-speed internet connection a critical element of our daily lives. We pay our bills online, check our bank statements, communicate via email, find information, and maintain a presence on social media.
This is where a VPN comes in, and a reliable VPN like NordVPN (read our NordVPN review here) can do wonders for you. However, while Tor is great, safe, and whatever you think, it’s not as great as another component – a VPN. We must explain that Tor is safe on paper but practice has shown that this browser can fail you. You might’ve heard of the domain extension called “.onion“, which sits at the end of each dark web website. Indeed, these websites use “atypical” names and domains to present themselves.



