You’ll need to configure your browser’s proxy settings to use the correct port on a web browser. For built-in Tor over VPN functionality, NordVPN operates specialized servers that automatically route you through the Tor network. You don’t even need to use Tor Browser, but keep in mind other browsers can still pass identifying information through the network. Alternatively, there’s IPVanish who claim to be the world’s number one VPN for Tor and comes highly recommended, you can save 60% on the annual plan here.
Best Onion Sites To Discover On The Dark Web In 2024
Typically, any reference to the visible web will be to common websites with a familiar internet domain extension. So, even though it does exist on the internet, Google doesn’t index any of these pages or content. Google considers the majority of the content on the entire web highly irrelevant and useless to its users. That’s why such a large percentage (as much as 94%) of the entire web is not returned in Google Search. Though secure against everyday threats, Tor is vulnerable to targeted attacks from state-level actors. A common inquiry from Tor users is if they should use a VPN to add an extra layer of protection.

As long as users take the necessary precautions, no one knows who anyone else is in the real world. Users’ identities are safe from the prying eyes of governments and corporations. The dark web, or dark net, is a small part of the deep web that is kept hidden on purpose.
Downloaded files could have malware in them that may be designed to de-anonymize you or infect your device. If you must download something from the dark web, only download files and run them using a completely isolated virtual machine. Understanding and knowing how to safely access this part of the internet is an important digital skill for today’s era. Although it requires more work, it provides tech-savvy users with a more familiar interface with better security for accessing Tor through a proxy.
How To Access The Dark Web Using The Tor Browser?
- The tradeoff is that you don’t get personalized search results, as DuckDuckGo doesn’t collect user data.
- You can use the Tor browser on Linux, macOS, Windows, Android, and iOS, and below are the steps for downloading and installing on each operating platform.
- Password managers and anonymous email services prevent unauthorized access and ensure private communications.
- If you are reading this, you’ve likely heard about how the Tor Browser can help protect your internet privacy and anonymity online.
- On the internet, Google’s reach barely scratches the surface.
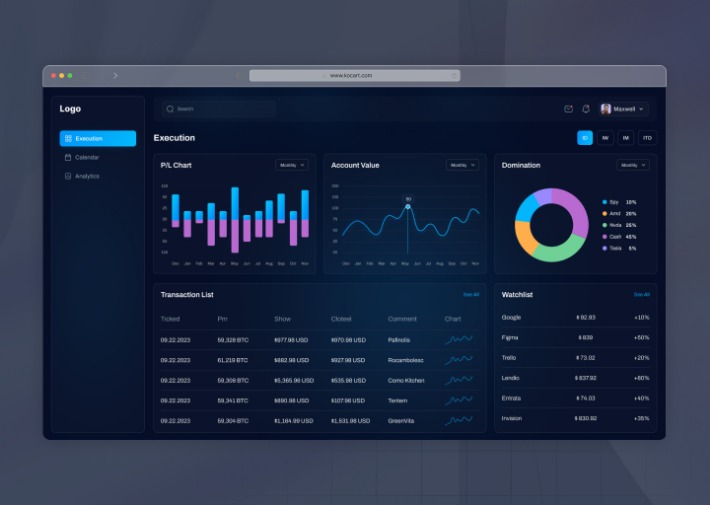
For example, state-level actors can execute traffic correlation attacks, wherein they monitor both incoming traffic at the entry nodes and outgoing traffic at the exit nodes. By observing these patterns, they can link a Tor user’s request to a server and reveal their intended destination. Tor traffic is decrypted at the exit node, which opens a vulnerability for malicious actors to inject malware or intercept traffic.

Can I Be Traced, Tracked, Or Hacked If I Access The Dark Web?
Did you know that Google only shows you a glimpse of all the websites that actually exist? The last time I checked, it’s estimated that the entire web is roughly 500 times larger than what Google returns in Google Search. When you run Tor Browser for the first time, you will see the option to connect directly to the Tor network, or to configure Tor Browser for your connection. Practice safe, smart digital habits if you must use Tor to log into personal accounts. For instance, always use strong passwords that mix letters and symbols, making them hard to guess. Use different passwords for each account so that a single compromised account doesn’t affect others.
A Free App For Android, By Looklikeaydn
When pixels display black, they’re “deactivated” and, consequently, consume no power. Yes, dark mode can help save power, but only in certain situations and on specific types of screens. Changing Outlook’s appearance affects all Office applications, not just Outlook. Microsoft Word, Excel, PowerPoint and other apps will also switch to the selected theme. Live OS options that can be run on nearly any computer by simply popping a USB stick in and booting from it include Subgraph OS, Freepto, and Tails.
Requirements (Latest Version)
Although content on the dark web is not as ‘indexed’ compared to the one on the clear web, you can still use search engines to find stuff. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen. Unlike regular browsers that directly connect to websites via your ISP’s DNS, Tor anonymizes your journey by routing your request through several relays before reaching its destination.
Exit Node Vulnerabilities
When using Tor, sometimes you will find exactly what your looking for, and you will wish you didn’t start using it sooner. It’s pretty evident that there’s a lot of harmful dissuasive information to drive people away from using tor specifically for this reason. All those story’s give people the wrong idea about this tool, and they don’t understand the power Tor offers. Obviously there is problems with both sides, but the positivity of Tor, outside of the anonymity purposes, needs to be acknowledged more. Then there’s the less popular VPN over Tor, which is advised against by the official Tor Project.
Can You Go To The Dark Web With Incognito Mode?
If you want to use Tor privately, you can use either a VPN or Tor Bridges (Tor nodes that are not publicly indexed). Tor users in the USA, in particular, may want to use a VPN, which will be faster and more reliable. The easiest way to access Tor is through a special browser known as the Tor Browser.
The U.S. Army developed “onion routing” to protect intelligence communications online. Later on, the underlying Tor code was released into the wild under a free license, leading to the formation of the Tor Project. In 2008, the first Tor Browser was released, making it easier for any internet users to access the dark web. The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose. The deep web contains sites and pages that are often prevented from being indexed by search engines and contain unlinked content. It can also reside in web archives, non-HTML pages, and so forth.
How To Install The Tor Browser On All Linux-based Devices
For obvious reasons—I don’t want to get you or me into trouble, after all—I’m not going to get too specific when it comes to what you can find for sale on the dark web. A lot of transactions are handled via cryptocurrencies such as Bitcoin, which is relatively (but not completely) private and anonymous. Another private cryptocurrency you’ll find being used is Monero, which prides itself on being untraceable. The dark web, for the uninitiated among you, is a virtual neighborhood beyond the borders of the normal, everyday internet (which includes the website you’re looking at right now).
Search Anonymously And Explore Dark Web
Assume that everyone and every site is trying to take advantage of you. Avoid giving up real information, don’t log into your personal accounts, and don’t engage in conversations that could identify you. Setting up NordVPN will ensure that it encrypts your connection, so your ISP cannot see that you are using Tor. It’s your necessary cloak of invisibility for the trip there.
The Tor Project also offers the Tails operating system for users who prefer a complete privacy solution for accessing the dark web safely. The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment). Part of what makes the dark web the dark web is that you can’t access it through your normal web browser, nor can you look something up on it via a Google search.



