Such content fuels a dangerous cycle of abuse, violence, and exploitation. It brings in vendor reviews from other places and verifies them using PGP signatures, so buyers can feel a bit more confident about who they’re dealing with. There’s also a premium account option for users who want extra benefits. And when it comes to paying, the site sticks to Bitcoin (BTC) and Monero (XMR) to keep transactions private. The dark web is designed in such a manner that it hides the identities and locations of its visitors.
KEY TAKEAWAYS Whether you are using Android or iPhone, you can easily access the dark web on your ph… Always use a fake name and a temporary email address when you buy something from the dark net shops. You can even use a secure email provider or a burner email address whenever you visit the dark web. According to Kaspersky, Librarian Ghouls APT continues its series of attacks on Russian entities. A detailed analysis of a malicious campaign utilizing RAR archives and BAT scripts. Then, you can set up 2FA (two-factor authentication) for that extra touch of security in case someone somehow figures out your password.
Top 7 Dark Web Marketplaces
Its look, design, options, and interface are exactly the exact copy of its competitor, but everything else, including buyers, vendors, and servers, is different. At its launch, the platform accepted payments through Litecoin, but now it has incorporated support for other payment methods like Monero and Bitcoin. The platform also cares about its users and uses PGP encryption and two-factor authentication to secure their data and communication. Cryptocurrencies, while offering enhanced privacy, also present significant risks. Users face vulnerabilities like market volatility, scams involving fake escrow services, compromised wallets, or theft through phishing schemes targeting crypto transactions.
- The darknet has become a cornerstone for secure and reliable drug trade, offering users unparalleled privacy and efficiency.
- When markets get compromised, we remove them immediately and issue warnings.
- Today, many organizations exist that are created only to handle these reports anonymously and effectively.
- For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography.
- Not every data breach advertisement on the dark web is the result of a genuinely serious incident.
- The marketplace is much more organized, which makes it easy to use and navigate.
Why Brand Monitoring And Threat Intelligence Are Stronger Together: 15 Key Benefits
We do not engage with darknet markets; our mission is exclusively dedicated to providing information for research and educational purposes. When one goes down, two more emerge with new ideas, better technology, and greater difficulty to track. It’s an ever-evolving ecosystem—constantly shifting, reinventing itself, and adapting. Although some of these markets prohibit certain extreme content such as violence or exploitation, most operate with very few rules beyond ensuring the security and anonymity of their users.
Future Trends To Watch:
Kaspersky DFI researchers observed more than 11 hacktivist movements and various actors across the region. While some of this growth may be attributed to the reposting or combining of older leaks, cybercriminals are clearly interested in distributing leaked data – whether new, old, or even fake. Consequently, in 2025, we are likely to witness not only a rise in company data hacks and leaks through contractors, but also an overall increase in data breaches. One of the biggest problems cybersecurity teams face isn’t a lack of tools — it’s too many alerts. And beware—while many explore out of curiosity or for research purposes, it’s important to remember that engaging with these platforms, even as an observer, can lead to serious legal and ethical consequences.
Trends Influencing The Dark Market 2024
As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web. Another notable security trick Wasabi uses to verify transactions is the Neutrino protocol. It assigns a task to the client instead of the server, eliminating server-related vulnerability. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction.
Use Active Monitoring Of Financial And Identity Theft

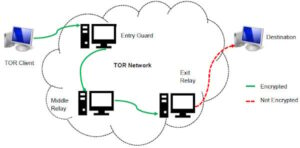
A network browser gives you access to sites with the ‘.onion’ registry operator. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software.
That’s why we maintain comprehensive safety guides, security recommendations, and OpSec protocols. Security audit results, uptime statistics, community sentiment analysis, vendor reliability scores. Lost nearly $3,000 worth of Bitcoin because he used a “verified” link from another directory that hadn’t been updated in eight months. The market had been exit scammed, but the old link redirected to a phishing clone. Bangkok vowed to conduct an autopsy, while US authorities had no interest in verifying the legitimacy of the suspect’s death.
Size Of Listings

Sure, you might come across listings for legit products like handcrafted jewelry or digital art, but those are few and far between. Some dark web marketplaces even host content that’s not just illegal but extremely harmful, so it’s really important to understand the risks before diving in. The first category includes classic marketplaces, which serve as one-stop shops for a wide range of illegal goods.

Advertised as “the most advanced darknet market ever,” OMG primarily provides illegal drugs, but also offers products like hacking utilities, banking information, and more. It first became active in early July 2020, with deposit volumes so low it appeared to be less of a darknet market and more a personal operation. However, nearly as soon as Hydra shut down, OMG began seeing high inflows for the first time, more than half of which came from Hydra counterparties.
ExpressVPN is an excellent choice for Tor and accessing the Dark Web. It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. The provider also offers a dedicated CyberSec suite that prevents annoying ads and blocks malware and trackers. NordVPN is one of the best VPNs to combine with the Tor browser whenever you want to surf dark sites. It offers top-of-the-line security and fast speeds for a smooth browsing experience on the dark web.

Tweak Tor Browser Settings
This system ensures that buyers can confidently select sellers with proven track records, reducing the risk of scams or low-quality products. Efficient navigation is facilitated by darknet market lists and onion URLs, which are regularly updated to ensure accessibility. These lists often include filters for categories, prices, and vendor reputation, streamlining the search process. Bitcoin remains the primary currency, offering anonymity and ease of use, though some markets are beginning to integrate alternative cryptocurrencies for added flexibility. These features collectively create an environment where the drug trade can thrive securely and efficiently, meeting the demands of a growing user base.