With stolen payment cards, a cybercriminal can immediately make purchases under your name, or even drain your bank account. And what’s worse, this shady corner of the internet is only getting bigger. In June 2022, BidenCash released over 7.9 million payment card data dating from 2019 to 2022 on a cybercrime forum. However, the dump only contained 6,581 records exposing credit card numbers.
H Largest Group Of Crooks Online

Compared to harvesting phone numbers or email addresses, carding demands more risk, and potentially, more reward. The release of this data poses significant risks for financial institutions and individual cardholders alike. Learn the basics of credit card cards, including features, fees, and rewards to make informed decisions about your credit card usage. The price for cloned cards varies depending on the credit limit, with an average price of $171. Telegram carding groups have become a significant threat in the cybercriminal community, with tens of thousands of members easily accessible through the chat application.

A Beginner’s Guide To Effective WhatsApp Marketing In 2024
Contrary to popular belief, most carding platforms no longer hide in the dark web (i.e. the Tor network). The sites I’ve evaluated this year all had clear web addresses—with ‘.onion’ versions available for some of them. Then, on Dec. 17, an apparent raid by authorities saw several of the carding site’s servers seized, temporarily shutting down the illicit business. Join us as we break down and discover the methodologies of card fraud using our dark web monitoring tool, Lunar. Credit card prices also vary depending on the brand, with American Express being worth the most at 5.13 cents per dollar. These groups often originate from leaked credit card credentials, which have become a common phenomenon, particularly in the past months.
Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products. Established in 2022, Torzon market is one of the biggest and most diverse marketplaces on the dark web. It is considered very secure thanks to strict user validations and transparent payment and vendor review procedures. Its focus on financial fraud and high-value transactions has attracted a dedicated user base, contributing to its growing reputation and market value.
How Technology Is Evolving To Counter Card Fraud On The Dark Web
Unlike a credit card, a debit card is connected directly to your checking account, allowing fraudsters to immediately drain your account. Even if you report the fraudulent activity quickly and limit your losses, you may still face the issue of bounced checks or being late on payments, Krebs says. Adobe lost nearly 3 million customer credit card records in a large-scale attack by hackers in October 2013. This breach was part of a larger effort that saw data from over 150 million users stolen, and the company ultimately reached a roughly $1 million settlement with its customers over the incident. In June 2022, BidenCash dumped details for nearly 8 million credit cards, and in October 2022, it leaked for free the details of 1.2 million cards, with half of them issued by U.S. banks.
Cybersecurity News
- Thieves might install skimming devices on these machines to steal data from your magnetic strip.
- Virtual cards generate one-time use numbers that can be linked to your actual account, making them less susceptible to being stolen in data breaches.
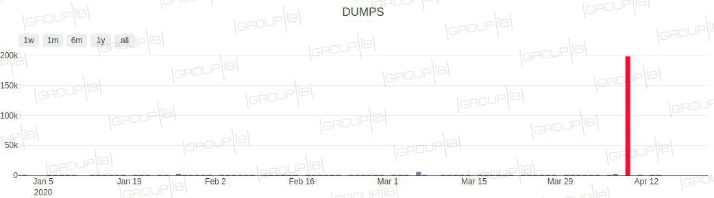
- After it relaunched in June 2022, BidenCash initiated a promotional campaign that included sharing a dump of 8 million lines of compromised data for sale, which included thousands of stolen credit cards.
- Although it offers leaks from many different countries, the site has a dedicated lookup and leak section for Canadian profiles, making it extremely easy to use for buyers interested in Canadian leaks.
- Furthermore, companies may be subject to regulatory action and fines for failing to protect consumer data adequately.
- You need to be over the age of 18 with a valid social security number that can be matched to a credit profile from the TransUnion credit bureau.
While stealing card data can sometimes be relatively easy, successfully using it is far more difficult. Transactions can be quickly flagged or blocked, making fraud attempts risky and unreliable. As a result, carding communities are developing new strategies to leverage existing online platforms and withdraw money from stolen credit cards. There’s an underground ecosystem where sensitive data is bought, sold, and traded—not just on the dark web, as you might expect, but also on publicly accessible websites, channels, and forums. Among these are platforms dedicated to carding—a cyber crime niche centered on the large-scale use and abuse of stolen credit card information.
Fraudsters use this data to create counterfeit credit cards or make unauthorized online purchases. B1ack’s Stash, on the other hand, emerged in 2024 and quickly gained attention by releasing millions of stolen credit card details for free—a tactic often used to attract cybercriminals. While it shares a similar purpose with Joker’s Stash, there is no confirmed connection between the two. Joker’s Stash was one of the largest and most infamous dark web carding marketplaces, operating from around 2014 until it voluntarily shut down in early 2021.
A Hacker Turned A Popular AI Tool Into A Cybercrime Machine
The FBI showed us sites on the dark web, one of them listed the items for sale complete with photos, descriptions, guarantees and even seller star ratings. Harris said, “this particular seller has a rating of 4 and a half out of 5 stars. So, it appears they have been doing this for a while and have some good customer service.” Alex Herrick is a seasoned web designer and digital strategist with over a decade of experience in the industry. Passionate about blending creativity with functionality, Alex specializes in crafting visually compelling websites that drive results. His expertise spans across web design, SEO, and digital marketing, making him a key contributor to Web Design Booth’s mission of empowering digital creators. Joker’s Stash still has imitators that masquerade as the now-defunct site, researchers say, with the goal of capturing that old traffic.
Using Tracker Apps To Monitor Your Card Data
If you suspect that your credit card information has been stolen through a data breach, contact your credit card issuer immediately and request a new card with a new account number. You can also place a fraud alert on your credit report to prevent potential further damage. Additionally, monitor your credit report for any signs of new accounts or unauthorized activity. In the unfortunate event that a credit card dump occurs, quick action is crucial. Companies must act promptly to notify affected customers, provide them with resources to protect their personal information, and work closely with law enforcement to identify and apprehend the responsible parties. Additionally, engaging a reputable data breach response firm can help mitigate damages and restore customer trust.
The data format, which includes user agents and victim IP addresses typically observed in both local and global phishing attacks, allows us to assert with high confidence that it originated from such activities. Prices for stolen credit card data depend on the volume, quality, and format of the information being sold. For instance, a single credit card number might cost between $0.10 and $25, while a dump of 10,000 records may sell for around $10 per record or more.
There are entire websites, channels, and forums dedicated specifically to carding. Unlike other types of stolen data—such as email lists or personal information—carding exists as its own distinct niche within the cyber crime ecosystem. Stolen credit card details are often sold on platforms and websites dedicated to, and branded as, carding websites. Financial institutions can proactively strengthen their defences by integrating intelligence derived from FraudAction. This involves leveraging insights from compromised credit card feeds into security protocols, enabling institutions to identify potential threats, block fraudulent transactions, and enhance overall risk management.
The Federal Trade Commission oversees a website called IdentityTheft.gov, which provides the appropriate steps to report and recover from credit card fraud. Unfortunately, if an unauthorized transaction has not yet occurred, it is nearly impossible to determine if your credit card information has been stolen. I’ve seen cases where security teams identified compromised card data from their institution appearing on the dark web weeks before they traced the actual breach point. This type of malware silently infect payment terminals and exfiltrate card data in real-time.
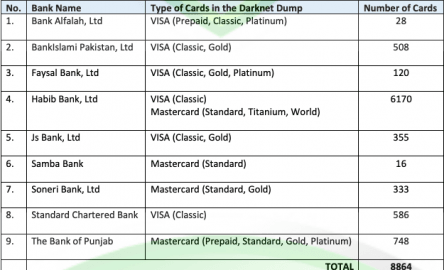
These criminals released the details of 740,858 credit cards, 811,676 debit cards, and 293 charge cards. The data dump disaster includes some complete names, expiration dates, CCV and unique email addresses. Dark web credit card numbers are stolen card details sold on hidden websites.



