You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom. However, there are some significant variances in the background despite the similarities. For example, Whonix’s virtual workstation machine connects to the internal virtual LAN. It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy. One option is to try DuckDuckGo’s .onion version, which is great for privacy.
Risks And Threats On The Dark Web
This means your activities cannot be traced or your browser history exposed. The US Naval Research Laboratory developed The Onion Routing (Tor) project in the late 90s. A network browser gives you access to sites with the ‘.onion’ registry operator. Initially, the dark web was mainly used by government agencies, big businesses, hackers, and cybercriminals.
Be Cautious With Downloads
However, there are several “.onion” search engines like “onion.city”, “onion.to”, and “notevil” that you can use to find suitable marketplaces. Since you’ve now installed the Tor browser, you can safely browse dark web websites and other (previously) hidden websites. From this point onwards, you can enjoy complete anonymity and security while being able to access “.onion” websites and other dark web browser domains.
What Is The Dark Web? How To Access It Safely?
Social networks, such as Facebook, have created dark web versions of their sites to address privacy problems related to their surface web versions. ExpressVPN had created a .onion version of its website to allow greater privacy and anonymity for Tor browser users. Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine. To access the dark web, you’ll need a specific set of tools – more about that later in the step-by-step section.
Malicious exit nodes can monitor your traffic, and browser fingerprinting can track you. Governments also often monitor Tor usage, even if they can’t see your activity. It’s recommended to take safety precautions when accessing the dark web, even if you’re after legitimate content. Without a VPN, the first server in the Tor network (the entry node) can see your real IP address, and your internet service provider (ISP) can see that you’re accessing the dark web.
Accessing The Dark Web With Tor Browser And VPN
Additionally, make sure that you only download the Tor Browser from the official website. ExpressVPN is my top choice because it supports Tor traffic on all of its servers and works automatically without needing any additional configurations. It also provides super-fast speeds, and its no-logs policy has been independently audited and confirmed — this way, you know it doesn’t store any user data. Plus, it backs all first-time purchases with a 30-day money-back guarantee, so you can try it out risk-free.
Best Practices For Accessing The Dark Web
VPN-over-Tor breaks dark web compatibility, reintroduces trust in the VPN provider, and creates unnecessary complexity. By keeping an eye on these alternative platforms and trends, you gain a deeper understanding of how privacy, anonymity, and underground markets adapt to new technologies and challenges. As digital ecosystems morph, staying informed and agile will help you make the most of evolving privacy tools—or avoid stepping into ever-more complex traps.
Final Verdict: Is The Dark Web Illegal?
At the same time, the same infrastructure facilitates illicit trade, malware distribution and identity theft. The line between privacy and peril is often one of intent—and operational discipline. Law enforcement officials can exploit that weakness using “Tor-exit-node” monitoring techniques to expose users’ IP addresses and potentially trace activity back to the original users. If you’re on the dark web to engage in illegal activity and your traffic passes through a compromised exit node, your secrets can be exposed.
- You’ll find the more dangerous content and activity at the dark end of the deep web.
- For example, Whonix’s virtual workstation machine connects to the internal virtual LAN.
- My favorite antivirus in 2025 is Norton, which scored a 100% protection rating during my tests (handily beating the built-in protections on my devices).
- Accessing the dark web isn’t like surfing the web everywhere else online.
- There are a huge number of overlay networks to choose from, but some of the most popular include Tor, Freenet, and Riffle.
The most common of these browsers is Tor, which launched in 2002 and serves millions of users. Another is the Invisible Internet Project (I2P), which specializes in the anonymous hosting of websites on the dark web. Additionally, configure your security settings to provide maximum protection, such as firewall activation and using a VPN, while browsing the dark web.

What Is Identity And Access Management (IAM)? Benefits,
- Many people use Tor to avoid surveillance by government agencies, ISPs, or other entities monitoring online activities.
- You can access the dark web on mobile with a dedicated dark web browser app.
- For example, cyberattacks and trafficking are activities that the participants know will be incriminating.
- This network contains thousands of volunteers who operate proxy servers to route dark web requests.
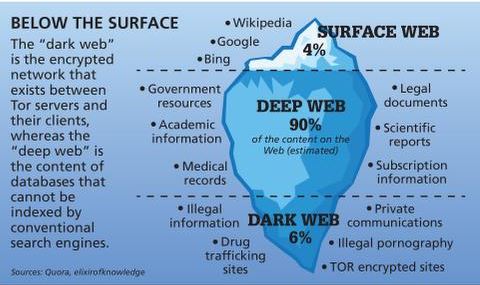
Here are some top tips for recognizing whether a service on the dark web is a scam or legitimate. NordVPN is offering a fully-featured risk-free day trial if you sign up at this page . You can use the VPN rated #1 with no restrictions for a month – great if you want to binge your favorite show or are going on a short trip. Although the dark web is a small portion of the internet, experts estimate it to account for 5% of all internet content (Spiceworks, 2025)2. According to McAfee, the deep web is about 10 to 20 times larger than the surface web, making up 90 to 96% of the internet3. But to see your personal account details or to make a purchase, you need to log in.
How To Access The Dark Web Safely
These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information. Next, disable Javascript in your Tor browser to prevent malicious scripts from attacking your browser sessions. You can disable Javascript by clicking on “Preferences” in the macOS app or “Settings” in the Windows app.
These are only a few of the .onion search engines that are available. While this doesn’t tell the exit node what your original IP address or your geographical location is, it could spy on your activity if the website you’re visiting isn’t a secured HTTPS website. But with the NSA setting up fake exit nodes, and growing concerns about the overall security of the network, you may need a VPN as well, if you want to ensure your privacy. Being hidden doesn’t translate into being completely protected from the possibility of tracking, or, when it comes to illegal activities, of risk.
The dark web, however, requires special software to access, as explained below. However, today’s most popular search engines — including Google, Bing, and DuckDuckGo — only index a portion of the internet. Yes, if you don’t use a VPN, your ISP can see that you’re connecting to the Tor network. Given the dangers of accessing the dark web, it’s crucial to take security precautions. Your information might be on the dark web if it was exposed in a data breach, sold, or stolen by hackers. To check, you can use dark web scanning or breach detection tools like Avast Hack Check or LifeLock Breach Detection to search for compromised data.
In this guide, we’ll explain what the dark web is, how to access it safely, and why using a VPN (Virtual Private Network) with Tor is essential for anonymity. What should you do if your information is found in a data breach or you think it’s been leaked somewhere? Change your passwords and watch out for suspicious activity on your credit reports. The dark web can certainly be dangerous — with no regulation, it’s a riskier place to hang out than the surface web.



