
Dark web markets have exploded in scale and reach in 2025, becoming the most dangerous hubs for trading drugs, stolen data, and hacking tools. These anonymous marketplaces—operating mainly on the Tor network—are now a primary threat vector for businesses and cybersecurity professionals. These platforms also often have built-in encryption for communications and transactions, making it hard for law enforcement to track down the individuals involved. The cloak of secrecy provided here is what keeps these dark web marketplaces bustling with illegal activities, posing a significant challenge for cybersecurity experts and authorities worldwide. Just like traditional e-commerce sites, darknet markets provide a platform for vendors to connect with potential buyers to facilitate transactions. Darknet markets, though, are notorious for the sale of illicit products.
How Complex Are Dark Web Marketplaces Currently?
Yes, the darknet still exists and continues to operate through networks like Tor, I2P, and Freenet. While law enforcement regularly shuts down illegal marketplaces, the underlying infrastructure remains functional. New darknet sites and markets continuously emerge to replace those that get shut down. The technology behind the darknet is actively maintained and continues to evolve. Its intuitive interface and advanced search features make it easy to find local and global products.
What Makes A Dark Web Market Different From Regular Online Stores?

With 25,000+ users and 3,000+ vendors, it’s the gold standard for escrow security and scale. The dark web, an enigmatic subset of the internet, operates as an encrypted and anonymous network inaccessible through standard web browsers. Unlike the surface web, which is indexed and easily searchable, or the deep web, which houses private databases and unindexed content, the dark web is a haven for covert activities.
A high degree of security measures further safeguards users on dark web marketplaces. Buyers and sellers alike use encryption tools, fake identities, and VPNs to add extra layers of protection. These markets employ robust protocols that protect transactions from law enforcement, making it challenging for even the most skilled cyber professionals to trace activity back to its origin. Dark markets are online platforms on the darknet where illegal goods and services are traded. You can find drugs, weapons, stolen data, and counterfeit documents on these marketplaces.

Incognito Secures

While the Tor browser boosts privacy, pairing it with a VPN adds a critical layer of security. On the dark web, traffic is routed through multiple server nodes that don’t log activity, obscuring the user’s origin and enabling anonymous communication. If you’re curious about what’s going on in the dark web next year, you’re in the right place. I’ve been digging into marketplaces like Abacus and AlphaBay for a while now, and this page breaks down what’s hot in 2025. You’ll find reviews, quick tables with the nitty-gritty details, and some practical tips on using Monero (see how) or setting up PGP (check it out).
It asks you to pay the merchant fee if you want to sell something, preventing the buyers from getting scammed. The vendors aren’t required to register or apply for a vendor account while using this platform. It ensures the buyer’s identity is kept hidden and accepts payments through cryptocurrencies, including Bitcoin, Litecoin, Ethereum, and Monero.
Did The Silk Road Marketplace Go Under?
These insights help researchers and privacy advocates understand where Tor is most relied upon, often highlighting global patterns in censorship, surveillance, and the demand for online anonymity. The CIA’s onion site allows users to securely report threats or suspicious activity, especially in regions where online surveillance is common. Its presence on the dark web also supports intelligence gathering and helps track cybercriminal activity.
The Top 10 Darknet Marketplaces Of 2025
If you’re into a darknet market with a community pulse and solid uptime, Bohemia Dark Market’s climbing the ranks—give it a spin if you like a vibe that’s less corporate, more crew. Classic darknet markets sell diverse illegal goods; data stores focus on leaked or stolen data like credentials, databases, and ID records. The first category includes classic marketplaces, which serve as one-stop shops for a wide range of illegal goods.

Why You Need Automated Dark Web Monitoring
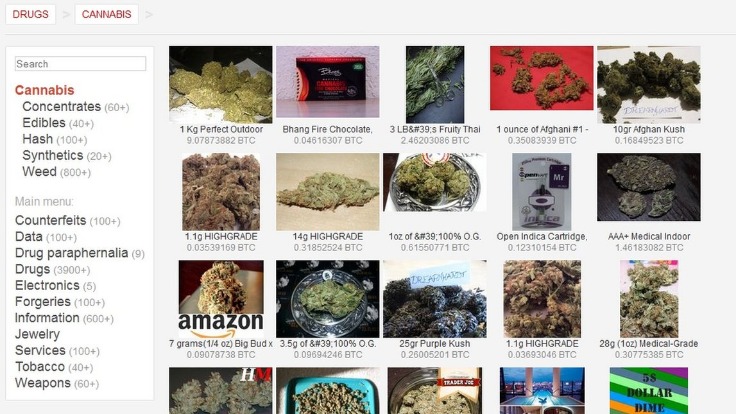
This expanded reach, combined with anonymity, only makes it easier for them to grow their operations without getting caught immediately. Purchases through links on our pages may yield affiliate revenue for us. We review and list tools and products without bias, regardless of potential commissions.
- These resources can be instrumental for businesses with limited budgets.
- Silk Road was once the most well-known dark web marketplace, but after its shutdown, many new markets took its place.
- Darknet markets trace their origins to the early 2000s, with the advent of Tor in 2002 by the U.S.
- This extra privacy makes it much harder for authorities to track down who runs these markets and where they are located.
- Whatever the outcome of the CyberBunker trial, the operation against Xennt has provided police with an Aladdin’s cave of information on other criminal activity.
The anonymity and lack of rules that define darknet marketplaces are exactly what make them breeding grounds for fraudulent activities. Of course, the promise of secrecy and unfiltered access might lure you in, but those same features are what make the environment so risky. Just like on the regular internet, phishing is a big problem on the dark web as well. Fraudsters create fake versions of popular darknet sites to trick users into entering login details or personal data.
Besides ever increasing hosting costs, the site will have to contend with authorities, attacks from hackers, and the occasional disgruntled market administrator. Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products.
The website allows a personalized searching experience, where you can search according to your geographical location, country-specific, and keyword or price-specific search results. If you ever decide to explore the dark web, protecting your identity is crucial. Most people start by using the Tor Browser, which hides your IP address. One of the most common is the exit scam, where a marketplace suddenly disappears and takes everyone’s money with it.



