When choosing a deep web search engine, start by identifying reputable providers. Reliable search engines often have a history of consistent performance and positive feedback from users. They prioritize your safety by offering secure connections and trustworthy results. A reputable provider ensures that you can explore the invisible web without unnecessary risks. DuckDuckGo’s dark web version brings the same commitment to privacy as its surface web counterpart. As one of the most privacy-focused search engines, it does not track your searches or store your personal information.
What’s The Difference Between Surface Web And Dark Web Search Engines?
It boasts a vast archive of over 400,000 pages, providing comprehensive coverage of .onion sites, including forums, blogs, and marketplaces. Onion websites are not indexed by the majority of conventional surface search engines. Using dark web search engines requires caution, and it’s crucial to remember that just because something is accessible doesn’t mean it’s safe. The dark web is a hidden part of the web that is not indexed by traditional search engines like Google and requires specialized software to access. If your team can find stolen credentials as soon as they appear on the dark web, you can be proactive about preventing an attack with specialized dark web search engines.
By leveraging AI-driven content generation, you can create high-quality materials that captivate your audience. This feature enhances the value of your output, making it ideal for both professional and academic applications. PageOn.ai’s intelligent presentation tools ensure your content stands out, improving overall engagement and effectiveness. Another major development was the rise of cryptocurrencies like Bitcoin.
What Is The Real Protection Offered By A VPN On Public Wi-Fi, And Is I
DuckDuckGo does not track your search history or collect personal data, making it a strong privacy-preserving option for searching both the surface and dark web. Regular search engines like Google use “crawlers” to index their pages, following links from known web addresses to index other linked pages. The dark web also uses a different protocol that a regular browser doesn’t follow. Finally, Google may not want content that appears on the dark web showing up in its search results. Kilos is a dark web marketplace search engine that lets users search for specific products they’re looking for. However, because Kilos is for the dark web, many of the items you may find may be unsafe or illegal.
AccuKnox Awarded Patent For Runtime Security Of Kernel Events

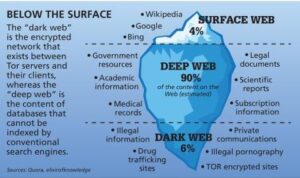
These websites are hosted on private server networks; therefore, you cannot reach them with Google or other standard search engines. Continue reading to learn more about the dark web and how to access it. On the other hand, the deep web is the hidden part of the Internet that contains private or restricted content that is not indexed by search engines. Unlike the surface web, you can’t access deep web resources directly through a search engine; they require login credentials or special permissions. In contrast, sites hosted on the dark web can only be accessed via onion routing with Tor, or another dark web browser.
Can I Get In Trouble For Using The Deep Web?
While the Tor browser provides a layer of anonymity, combining it with a VPN like Forest VPN adds an extra shield of security. Because your internet service provider can still see that you’re using Tor — a VPN masks this, encrypting your traffic and hiding your IP address. No matter where you browse the dark web from, you should exercise caution. Many dark web sites host illegal activities like gambling, drug trafficking, counterfeiting, cybercrime, and other illicit content. This includes the potential to pirate copyrighted material, which could also lead to legal consequences.
How Tor Nodes Work To Keep You Anonymous

While the dark web offers countless opportunities for discovery, it’s not without its dangers. Scams, malware, and illegal content abound, so it’s crucial to tread carefully. By using tools like Haystak and Forest VPN, you can minimize these risks and enjoy a more secure browsing experience.
By following these precautions, you can explore the dark web with a greater degree of safety and security. The dark web is a double-edged sword, offering anonymity but also posing significant risks. It’s a hub for illicit activities, with cybercriminals ready to exploit any weakness. Without the right precautions, your IP address could be exposed, leaving you vulnerable to hacking, tracking, or even identity theft.
FAQ: More About Onion Sites
Proton Mail is an anonymous email service that operates an onion site. Facebook’s onion mirror allows people to access it in countries that block the platform, allowing people to connect across digital borders. That said, the social network’s data collection and tracking practices may seem at odds with many of the principles motivating dark web users. Concerns about how Meta treats user data have led many people to delete their Facebook profiles or at least limit their social media presence.

Should I Use Services Like Web2Tor?
- These are designed to equip you with everything needed to choose the right tool.
- Plus, many .onion websites are created to be temporary or invite-only, so they may not even be active long enough to be indexed.
- Their URLs (aka dark web links) have .onion as the domain, instead of the common surface web domains like .com or .net.
- If you are a researcher, scholar, or expert looking for intricate and specific information that cannot usually be found on the surface web, then Cybersyn is your best asset.
- This raises the possibility of coming across dangerous content or a rogue website.
The Hidden Wiki (2007) revolutionized dark web navigation by introducing the first structured directory, categorizing .onion links into forums, marketplaces, and services. It became the dark web’s de facto entry point, akin to a digital yellow pages, but its manual curation limited scalability. Users relied on handwritten lists or email chains to share .onion links, with no centralized indexing. The lack of search tools made the dark web a fragmented, insider-driven space, inaccessible to most. Dark web search engines bridge this gap by crawling and indexing these hidden services, serving as the only way to navigate the Tor network’s uncharted terrain.

Freenet stores encrypted files across its distributed network, making it difficult to trace the origin or content of information shared within its dark web ecosystem. Standard web browsers like Chrome or Firefox won’t suffice to access the dark web. Specialized dark web browsers provide the necessary layers of encryption and anonymity.
The directory’s structure saved time, but its inconsistencies required extra legwork. Its open-source codebase, hosted on GitHub, invites community audits, ensuring trust. Ahmia’s defining feature is its commitment to filtering out illegal content, such as child abuse material, a rare stance in the dark web’s murky landscape. These tools are the dark web’s rogue librarians, mapping a realm where traditional rules don’t apply. They lack the scale or polish of surface web engines but are critical for exploring what’s deliberately hidden.
It provides indexed links to various .onion web pages, guiding users through the often treacherous waters of dark web browsing. Although The Hidden Wiki includes filters to block many dangerous sites, some risky links may still be present, necessitating caution as users explore. The U.S. Navy developed it to facilitate secure Internet communication between informants in other countries. In keeping with that attitude, the Central Intelligence Agency (CIA) launched a .onion website, enabling users to view their resources safely and anonymously from anywhere in the world.
This is especially beneficial for professionals in cybersecurity or research, who require quick access to specific types of information. However, time has changed, and now several services offer free dark web access with the least amount of technical knowledge. Ahmia’s integration with “Globaleaks,” an open-source project facilitating anonymous suggestions and comments, further enhances its functionality. Moreover, its collaboration with Tor2Web extends its accessibility beyond the Tor network, catering to a broader audience.