Additionally, it can promote financial inclusion and help bridge the gap between traditional banking and the unbanked population. Embracing digital payments and the SBD can help Solomon Islands move towards a more efficient and inclusive economy. When choosing the best payment method for online bill pay, it’s important to consider your personal preferences and needs. If you prioritize security and low fees, a bank transfer or digital wallet may be a better choice.
Mitigating Risks: Dark Web Monitoring For Payment Security
Regularly review the marketplace’s guidelines and stay updated on any changes or new security measures. When stolen data is exposed on Dark Web marketplaces, businesses face regulatory penalties, financial losses, and loss of customer trust. Small businesses, in particular, are vulnerable due to limited cybersecurity resources, making data breaches one of the top cybersecurity threats they encounter.
Dark Web: The Dark Web’s Role In Facilitating Credit Muling Networks
The use of Monero has also been driven by its lower transaction fees compared to Bitcoin, making it more cost-effective for dark web transactions. While Bitcoin remains the most widely used cryptocurrency on the dark web, there has been a growing adoption of privacy-focused coins like Monero. The untraceable nature of Monero transactions, along with lower transaction fees, has made it an attractive option for those seeking to maintain their privacy to a greater extent. This trend highlights the continued interest in anonymity and security within the dark web community. Marketplaces rely on encryption, hidden services, and distributed infrastructure to protect users and stay online despite takedown efforts. Even when sites are shut down, dynamic communities such as carding forums often reappear under new names, making them hard to eliminate completely.
After buying stolen credit card information, fraudulent actors use carding bots to validate the information. These bots automate the process of making small transactions on e-commerce websites to test if the card is active, and they can be used without triggering fraud alerts. Another crucial function of online forums and chatrooms is the provision of support and guidance to credit mules. Newcomers to the network can seek advice from more experienced members on topics such as how to avoid detection, handle suspicious transactions, or navigate potential obstacles. For instance, a novice credit mule might seek advice on the best methods to withdraw funds without arousing suspicion from financial institutions. The community’s collective knowledge and experiences can provide valuable insights and help individuals optimize their operations.
Best Ways To Pay Anonymously Or Privately
- Additionally, make sure to use reliable courier services to ensure timely and secure delivery.
- The decentralized nature of cryptocurrencies allows for greater anonymity and privacy compared to traditional payment methods.
- Law enforcement agencies and cybersecurity experts must stay one step ahead, constantly adapting and evolving their strategies to counter the ever-changing tactics employed by malicious actors.
- The sale of stolen data on the Dark Web presents a persistent and evolving threat to businesses of all sizes.
- Cybercriminals often disguise malware within legitimate-looking files to trick users into compromising their own security.
Unlike credit and debit cards, which often come with transaction fees ranging from a few cents to a percentage of the purchase amount, e-checks eliminate these additional costs. This is particularly beneficial for businesses and individuals who frequently make large transactions or online purchases, as the savings can quickly add up. In the ongoing debate of COD vs. Card payments, it’s clear that Cash on Delivery remains relevant and beneficial from various angles. While digital payment methods offer their own advantages, COD continues to be a critical lifeline for a vast demographic of shoppers who value trust, convenience, and financial inclusion. Its enduring presence in the e-commerce world underscores its adaptability and resilience in the face of technological advancements.
Avoiding Scams And Law Enforcement
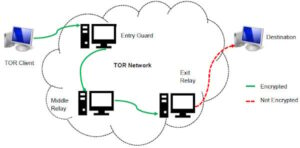
Exploring the dark web and engaging in selling activities can be a thrilling and potentially profitable venture. However, it is important to approach it with caution, diligence, and adherence to ethical boundaries. Before diving into the world of dark web marketplaces, it’s important to have a basic understanding of what the dark web is. Unlike the surface web, which is accessible to everyone through search engines, the dark web is a hidden network that requires specialized software, such as Tor, to access. This encrypted network grants users anonymity by bouncing their internet traffic through multiple nodes, making it almost impossible to trace their activity back to them.
Typically, you load funds into your virtual card account, and then create a disposable card that draws from this balance. These cards aren’t issued in your name, and you can load them with cash at retail locations without providing any personal information. Even if a hacker were to steal your prepaid card data, the potential loss is limited to the card’s balance. You’ll have to buy gift cards specifically for the platform you want to purchase from, making it less flexible than your normal credit card.

Security Tips For Using Cryptocurrency On Dark-Web Marketplaces
It is a collection of websites and online platforms that are not indexed by search engines and require specific knowledge or access to enter. This unique characteristic makes the dark web an appealing space for those seeking privacy and anonymity. Bitcoin, the digital cryptocurrency that operates on a decentralized blockchain, has become increasingly popular in recent years as a means of conducting transactions online. However, there is a hidden side to Bitcoin that exists on the dark web, a secretive corner of the internet where privacy and anonymity are prized above all else. Choosing the right payment method depends on individual preferences, financial habits, and the context of the transaction. Businesses should offer a variety of options to cater to diverse customer needs, ultimately optimizing conversion rates and enhancing the overall user experience.
NFC Fraud Wave: Evolution Of Ghost Tap On The Dark Web
Techniques such as digital footprint analysis, cryptocurrency tracing, and undercover operations are employed to infiltrate marketplaces, gather evidence, and execute effective takedowns. These efforts demonstrate the commitment to combating cybercrime and limiting the reach of these dangerous platforms. By implementing these practices, you can ensure secure and efficient transaction handling on the dark web. Prioritize clear communication, trustworthy payment methods, and proactive customer service to build a solid foundation of customer trust and loyalty. It’s important to note that accessing the dark web carries both risks and responsibilities.
- Furthermore, the increased use of dark web bitcoin mixers has gained attention from law enforcement agencies.
- Bitcoin’s digital nature, combined with its decentralized nature, made it an ideal currency for these transactions.
- The card skimmer illegally captures the credentials of cards inserted into the machine.
- On the dark web, Bitcoin has been the preferred method of payment due to its decentralized nature and its ability to ensure privacy for users.
- By utilizing cryptocurrency tumblers and mixers, credit muling networks can ensure that the funds they receive cannot be easily traced back to their illegal origins.
Bitcoin mining, a crucial process for validating and recording transactions on the digital currency’s decentralized blockchain, requires significant computational power. As the popularity of cryptocurrency has surged in recent years, so has the demand for mining equipment and energy. However, some individuals and organizations have found a way to exploit the dark web’s anonymity and privacy features to engage in illicit mining activities. In addition to scams, the dark web is also teeming with other fraudulent activities related to Bitcoin. Some individuals may offer to sell Bitcoin at below-market rates, only to disappear after receiving the payment.
Crucially, she also outlines what service providers—including telcos, financial services, and insurers—can do to help protect consumers from carding in today’s shifting cyber threat landscape. Responses from cybersecurity professionals are increasingly focused on comprehensive strategies to combat dark web threats. You should be aware that initiatives like threat intelligence sharing and public-private partnerships are becoming more common. Further compounding these issues is the rise of decentralized marketplaces, which operate on peer-to-peer networks, making them inherently more difficult to target. Coupled with the use of anonymizing tools like Tor and VPNs, cybercriminals can obfuscate their identities and locations, posing a constant challenge for investigators. Furthermore, the international nature of these crimes requires collaboration between various jurisdictions, which can lead to delays and gaps in enforcement.

The dark web has become a notorious hub for illegal activities, and credit card fraud is no exception. Criminals exploit the anonymity and encryption features of the dark web to buy and sell stolen credit card information. This underground marketplace offers a range of stolen credit card details, including card numbers, CVV codes, and even full personal information. The rise of cryptocurrency, particularly Bitcoin, has created new opportunities and challenges within the dark web ecosystem.

Within the dark web, credit muling networks thrive by sharing information and techniques. Criminals exchange tips on how to avoid detection by banks and law enforcement, discussing the best methods to open bank accounts using forged documents or stolen identities. They also share strategies for transferring funds without raising suspicion, such as using cryptocurrency exchanges or prepaid cards. This exchange of knowledge allows credit muling networks to evolve and adapt, making it increasingly challenging for authorities to combat these activities effectively. Behind the scenes of dark web transactions, various anonymity measures enhance the security of both users and their financial dealings.
Exploring The Dark Web: Understanding Its Role In Cybersecurity Threats
For fledgling criminals who don’t know how to use stolen credit cards, there are plenty of free and paid tutorials for carding on the dark web. Due to the anonymity provided by the Dark Web, traditional cybersecurity measures are often ineffective in monitoring illegal activities. This reinforces the necessity for cybersecurity assessments and Dark Web monitoring services to identify and mitigate emerging threats.
Sophisticated methods like live admin panels and payment cloaking make scams harder to detect. Live admin panels allow real-time interception of victim data and OTPs (one-time passwords), enabling high-success fraud. In the past few years, cases of financial fraud have also spiked, partly fuelled by the dark web, where criminals are able to interact and share techniques and targeted next victims. According to Cybernews, financial fraud-related listings comprise a significant portion of dark web activities, accounting for over 34% of total listings. You will never know when you stumble upon illegal materials, inadvertently download malicious software, or expose yourself to identity theft. But if you must visit the dark web for ethical reasons, here are some safety precautions.