They also use it to encrypt their communications and keep their identities under wraps via Tor — especially in countries where reading or sharing content could lead to harm. Whether or not you’re on the dark web, Facebook loves to collect data. Your information could easily end up elsewhere, so think twice about what you post online. While no single tactic is foolproof, a layered approach—combining technical, operational, and psychological defenses—greatly improves your safety and confidence when navigating the dark web.
Ready To Explore Web Data At Scale?

In due course, the framework was remodeled and made public as a secure browser. An easy way to find content on the dark web is to receive a link from someone who already knows about it. Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged.
Identity Theft And Financial Fraud
Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for. You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe.
A Dark Web Search Engine

Together, we can build a strong defense against the risks posed by the dark web and ensure your organization’s safety in the digital realm. The reputational damage inflicted by a breach can be just as devastating. Customers may lose trust in an organization’s ability to safeguard their data, resulting in client attrition and long-term harm to the business’s brand. A study by IBM found that 83% of consumers will stop doing business with a company after a major security incident. While no approach is foolproof, a thoughtful, criteria-driven strategy ensures a more secure and beneficial experience on the dark web. As most malware is designed for Windows, another way to stay safe is to switch to a different operating system.
That all is for general internet activities, you can guess how crucial having a VPN is when you hop onto something like the dark web. Then, you can set up 2FA (two-factor authentication) for that extra touch of security in case someone somehow figures out your password. If you ever have to connect to public Wi-Fi, make sure to use a VPN to keep your browsing safe and private. Sometimes, you might be hacked by using weak passwords or even just connecting to unsecured Wi-Fi on public networks.
What Should I Do If I Accidentally Access A Dark Web Store?
Hence, you never know when a popular .onion site is going to vanish, or even die. Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). The best thing is to actually understand how to find the fresh, new links.
Chainanalysis, a blockchain analysis firm, conducted research that shows that the revenue decreased from $3.1 billion (2021) to $2 billion (2024). As mentioned earlier, launching a cyberattack doesn’t require any hacking skills. Even people with zero technical knowledge can buy phishing kits, ransomware, or stolen logins. Like ransomware, criminals can buy software and inject your devices with viruses. With it, they can spy on people, steal their sensitive data, or secretly control their devices.
This Developer Declares That Your Data Is
We highly recommend using a strong VPN like NordVPN to stay safe and private. Later, the CIA released its onion website to provide worldwide access. It is important to note that the people or journalists who use ProPublica to spread their truth recognize the risk of doing so. As a result, we want you to stay safe and anonymous by using a paid VPN service whenever you surf this dark web platform. Onion sites are far safer to use as they are hidden deep within the deep web. Also, since users can only access them using the Tor browser (with its high-end encryption), users can be rest assured their identities and locations remain hidden.
Analysis indicates that the average price for listings (with at least one sale) was anywhere from four to eight times the median listing price on Apollon. The observed distance between these grew with vendors with larger number of units reported sold. The best VPNs will anonymize your browsing by encrypting the connection between your device and the VPN provider. This makes it extremely difficult for your ISP or anyone with access to your internet records to know which sites you visit or apps you use. You can also find a few free VPN services, but be aware of the risks if you’re still using legacy VPNs in your organization.

Invest In Dark Web Monitoring Tools

The Tom and Jerry Store, an online storefront claiming to have a long-standing presence in the dark web drug market, promises high-quality drugs and seamless shipping from the Netherlands. However, this platform reveals itself to be a dangerous trap that compromises the safety and well-being of its customers. Reports from disillusioned customers reveal a pattern of subpar products and a complete disregard for customer satisfaction. Furthermore, the Tom and Jerry Store’s brazen promotion of high-quality cocaine with free shipping is deeply troubling. By offering a potent and potentially harmful substance, this platform neglects the responsibility it holds towards the health and safety of its customers. Such practices demonstrate a blatant disregard for ethical boundaries and highlight the dangerous nature of the Tom and Jerry Store’s operations.
- This encryption makes attribution and tracking more difficult for authorities and cybersecurity professionals.
- Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web.
- You can see all the product categories the marketplace deals with on the homepage.
- If you pay for something and it never arrives, you may well not be able to track down the seller to get your money back.
It saves a select version of each page and preserves it even after upgrades have taken effect on the original site. However, not all books on this site are legally available, so they don’t have copyrights. That means you may violate copyright laws while downloading books, so use a VPN to protect yourself from any legal repercussions if you have a dire need to use it. You can access thousands of issues, from the most popular to the most niche. It is one of the best sites on the dark web to find your favorite comics.
You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. The dark web also helps individuals communicate about or sell illegal items such as weapons, drugs, malware, etc. Many people see hacked information and stolen card data being sold on the dark web. For example, you can find information unavailable to the public and share data privately while protecting your online identity.
And it’s still essential to use strong passwords and two-factor authentication (2FA) to help keep your account secure. Overall, dark-web marketplaces inherently involve substantial risk, and users must thoroughly understand these threats. Although dark-web marketplaces utilize technologies like Tor and I2P to enhance anonymity, these methods are not foolproof.
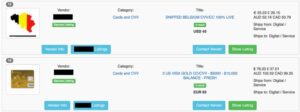
BidenCash became known for regularly leaking huge amounts of stolen credit card data and personal information — often for free. This strategy, along with a strict sign-up process, helped it grow fast. The goal is simple — make financial fraud easy and get as much attention as possible. From drug sales and breached data to scam services and malware, dark web markets are some of the most dangerous corners of the internet. These markets mimic traditional e-commerce websites, but instead of second-hand books or vintage jackets, they traffic in illegal goods and criminal services. Transactions in these underground markets prioritize anonymity and security to evade detection.