In 2022, federal authorities uncovered a major skimming ring that installed covert devices on gas station pumps throughout the Southeastern United States, compromising thousands of cards before detection. Ane-SIM allows users to quickly switch between operators withoutneeding a physical SIM card or a traditional internet connection,making cybercriminal operations extremely mobile. In addition, various cybercriminal channels have been identified that offer equipment to orchestrate fraud via NFC, including NFC readers, compatible cards (white plastic), encoders, and other devices.

Carders Want Your Credit Card Info
Over time, BHF has become a notable forum in the Russian cyber landscape because of its seemingly technically skilled community and an organized structure (hence, authorities aren’t able to seize it yet). It also has a premium sales section where cybercriminals can get more exclusive products. However, its most-used feature, as per our research, is the tiered membership system that’s almost similar to BreachForums. A premium user has access to the private Telegram channels that include an exclusive leak channel that’s unavailable to regular members.
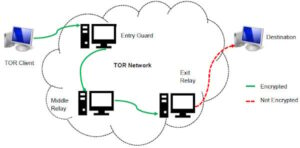
Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading. Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet. Based on our observations from analysis on dark web data using Lunar, we’ve identified the top 7 marketplaces on the dark web in 2025. We developed Lunar to monitor the deep and dark web, including dark web marketplace sites.
Purchasing Gift Cards Fraudulently
Some users want to expand and bolster their hacking skills, and hence they go to forums and look for ransomware groups. Also, you’ll find various users in the dark web message boards bragging about some of the attacks that they’ve successfully pulled off. Some users are in the forums trying to engage in smear campaigns against the competing forums. Moreover, the forums use cryptocurrencies like Bitcoin as the only mode of transactions. The digital currencies provide anonymity, and they’re hard to trace, which makes them the best option for illegal transactions. Given that these are online transactions, the parties involved want a channel that they’re sure of getting the services or goods they purchase.
Drops may be willing accomplices recruited online or unwitting individuals tricked into acting as recipients through fraudulent job postings or online scams. Once drops receive the items, they forward the goods to the criminals or reship them to another intermediary, further distancing the original perpetrators from direct involvement. Marketplaces frequently employ an escrow system, temporarily holding cryptocurrency payments until buyers confirm that the purchased credit card data is valid and functional.
Why Monitor Deep And Dark Web Credit Card Sites?
Immediately upon completing the transaction, buyers receive access to the purchased data. This information is usually delivered electronically within the marketplace, either displayed directly or provided as encrypted files accessible via secure downloads. From here, buyers proceed to utilize this stolen information to commit fraud—typically by making unauthorized online purchases, creating counterfeit physical credit cards, or initiating financial transfers. Globally, financial institutions and businesses spend billions more each year attempting to prevent, detect, and recover from fraudulent transactions.
Prevoty Is Now Part Of The Imperva Runtime Protection

Obtaining card details with sniffing or skimming tools is no simple matter—to go down this route, a cyber criminal has to find a way of installing their scraping tool on the target, whether it’s digitally or physically. Carding is often linked to broader cybercrime tactics such as phishing, credential stuffing and malware attacks. For businesses, carding can lead to chargebacks, financial losses, regulatory scrutiny and reputational damage, particularly if sensitive customer data is also exposed during an attack. Forum reputation and account age are big giveaways about the credibility of a threat actor; the more likely a new cybercriminal employee will follow through on what they promise to deliver for their employer. One forum user recently explicitly stated they don’t even look at posts from users with low reputations and short forum tenures.
Phishing And Vishing

Discussions on carding forums often include how to bypass security systems, target specific companies or use “fresh” data from recent breaches. Monitoring these forums is critical for threat intelligence teams seeking early warning of card fraud campaigns and/or leaked corporate data. Businesses whose data is compromised often aren’t aware until fraudulent activity is detected or their data appears on underground marketplaces. In recent years, I’ve observed some shifts in how carding is carried out—changes that mirror broader developments in both technology and threat intelligence research.
Enhanced Cybersecurity
See our 2022 typologies report for the latest money laundering trends or contact us for a demo. Announcing the seizure, the US Department of Justice noted that the service sold illicitly-acquired personal information of 24 million victims – including names, dates of birth and social security numbers. The seizure was conducted on June 7th through cooperation with authorities from Latvia and Cyprus. Stick to cryptocurrency, avoid downloading anything, and don’t share any personal info.
However, thetechnology behind NFC (Near Field Communication) has been aroundsince the early 2000s, with the first NFC-enabled phone launched byNokia in 2006. As NFCtechnology became more widespread, reports of fraud and cardingincidents started to emerge, mainly as mobile payment systems likeGoogle Wallet and Apple Pay were introduced. To overcome these challenges, Webz.io offers a stable and continuous flow of information from dark web forums and a tool to analyze that data. You can access deep and dark web data through our dark web API and perform detailed data analysis with Lunar.
- It’s the best way that users can make open communications as well as share sensitive data without exposing themselves.
- Businesses are expected to monitor for suspicious activity, secure payment infrastructure and respond swiftly to emerging threats.
- As the internet grew, carding moved online, leading to new techniques, such as phishing and hacking into company databases to steal large volumes of credit card information.
- As for the credit cards, the file itself features cards with an expiry date from 2023 to 2026.
- Get a live demo of our security operations platform, GreyMatter, and learn how you can improve visibility, reduce complexity, and manage risk in your organization.
- This is because resellers of stolen card data are likely to pivot to other large-scale dump forums.
Cybercriminals can exploit NFC vulnerabilities to access personal information stored on devices or NFC-enabled ID cards, leading to further misuse of the victim’s identity. NFC fraud can result in significant financial losses, especially when attacks are scaled. Forexample, the “Ghost Tap” attack allows cybercriminals torelay stolen NFC payment data to make unauthorized purchases. Eventhough individual transactions may be small, the cumulative lossescan be substantial when applied at scale.
Hacking Tools
But the shutdowns and disappearances appear to be having an impact on some users, who are starting to get worried. Monitoring these sites also helps track the effectiveness of security investments. I can’t stress this enough, your point-of-sale systems should never share a network with general-purpose computers or IoT devices. We’re not just looking for individual red flags, we’re building comprehensive risk profiles based on dozens of different indicators. Modern payment processors use device fingerprinting and behavioral analytics to spot suspicious patterns.
Additionally, set up credit card notifications to track transactions in real time, helping you catch any unauthorized activity quickly. A dark web carding market named ‘BidenCash’ has released a massive dump of 1,221,551 credit cards to promote their marketplace, allowing anyone to download them for free to conduct financial fraud. Carders use a range of tools and tactics to evade detection while committing fraud.
Cryptocurrencies provide a decentralized and anonymous means of conducting transactions, making them an attractive option for carders looking to cash out their ill-gotten gains. Bitcoin mixers, also known as tumblers, further enhance anonymity by obfuscating the transaction history. However, the use of cryptocurrencies also introduces new challenges, such as fluctuating exchange rates and the need to convert digital assets into traditional currencies. The release of this data poses significant risks for financial institutions and individual cardholders alike. For instance, BidenCash saw a surge in user activity following its free data leaks.