As such, the dark web has attracted many parties who would otherwise be endangered by revealing their identities online. Abuse and persecution victims, whistleblowers, and political dissidents have been frequent users of these hidden sites. But of course, these benefits can be easily extended to those that want to act outside of the constraints of laws in other explicitly illegal ways.
Limitations Of Using Tor
Venturing further into the deep web does bring a bit more danger to the light. For some users, portions of the deep web offer the opportunity to bypass local restrictions and access TV or movie services that may not be available in their local areas. Others go somewhat deeper to download pirated music or steal movies that aren’t yet in theaters. Locating surface web websites is possible because search engines can index the web via visible links (a process called “crawling” due to the search engine traveling the web like a spider). The content management system into which I am typing this article is on the Deep Web.
Table Of Contents

Your ISP can see that you’re connected to Tor, as the encryption takes place AFTER you connect to the browser. With this information, the ISP will likely know you’re on the dark web because Tor is mainly used for this purpose. You don’t want this suspicion because of the darknet’s reputation and notoriety. The so-called surface web is readily accessible to all of us and thereby, less interesting. Well, relying on Tor to keep you anonymous online is a good recipe for disaster – we’ll see why soon.
Can You Use The Tor Browser For Torrenting?

All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy. The place is as messy and chaotic as you would expect when everyone is anonymous, and a substantial minority are out to scam others. The dark web allows people to access and share all sorts of illegal and explicit material without judgment or censorship. The best way to find out is to check the “Have I Been Pwned” (HIBP) website. This website allows you to type in your email address or phone number and see if it’s been compromised in any data breaches.
Access The Dark Web Safely With Tor Over VPN
By following these steps, you’ll have I2P and Hyphanet set up for secure and private browsing on the dark web. Both networks have unique strengths, and while they aren’t as user-friendly as Tor, they offer excellent alternatives for those seeking robust privacy and decentralized communication options. For more advanced use, Hyphanet allows you to create and host your own freesites, participate in forums, and communicate anonymously with other users.
Should I Use The Tor Browser For Everything?
A vast number of URLs have domain endings such as “.onion”, which means that the URLs are only accessible by Tor users. The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more. Pixel Privacy believes in digital privacy and does not believe in using it for heinous and/or illegal activities, and so the focus of this article will be on legal activities.
Seizing Illegal Websites

As such, you should use it with caution, and probably only as the last resort. You can still access the Tor network through it, but it is not very safe. You can go to the onion.cab site directly via your regular browser, and get access to the Tor network. However, keep in mind that you must only use them as the last resource.
Before visiting any dark websites, get comprehensive cybersecurity software to help protect yourself from threats you may encounter. The websites you visit every day aren’t all there is to see on the internet — not even close. Beyond this “surface web” is the deep web, and within the deep web is the dark web. Then, use data breach monitoring software to help find out if your personal data has leaked onto the dark web. While Tor offers anonymity by routing your traffic through a decentralized network of nodes (onion routing), it shouldn’t be your only line of defense for privacy. Malicious actors and government agencies can run Tor nodes, compromising privacy and security.
Prior to joining CrowdStrike, Baker worked in technical roles at Tripwire and had co-founded startups in markets ranging from enterprise security solutions to mobile devices. He holds a bachelor of arts degree from the University of Washington and is now based in Boston, Massachusetts. The dark web offers both benefits and risks for users going into it, but the intent of the user will also impact this. Similar to using a standard web browser to access the open web, the act of using Tor or a dark web browser to access the dark web is not illegal in and of itself.

Are Dark Web Browsers Safe?
Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers. I strongly recommend surfing on the dark web using virtual machine software instead of your locally installed Windows. Because it’s easier to contain malware in a virtual environment, which can be fully controlled.
- With the dark web as dangerous as it already is, it’s best not to take the easy way out.
- Pixel Privacy believes in digital privacy and does not believe in using it for heinous and/or illegal activities, and so the focus of this article will be on legal activities.
- While NordVPN is undoubtedly a great service, it’s not without fault.
- The existence of an anonymous and hidden internet then allowed for alternative information channels and illegal websites to flourish.
- Each node decrypts just enough data to know the next destination but not the origin, making tracing the connection back to the user exceptionally difficult.
- No node can track the complete path the traffic has taken, and more importantly, neither can anyone who finds it on the other side.
You can now safely browse dark web websites and hidden wikis, but if you plan to do anything more than that, you’ll need to take several precautions. If you plan to purchase on a dark net marketplace or dark web commerce sites, you’ll need to create a fake identity. Remember only to make purchases using digital currencies and never provide any online banking login details.
Tor uses DuckDuckGo as its default search engine, which is expected for a privacy-focused browser. It doesn’t track your IP address, search history, and other personal data. The entry node knows your IP address but not the intended destination. The middle node knows the previous node but not your IP address or what you’ve requested online. The exit node knows what you’ve requested and connects you to it, but it doesn’t know your device and its IP address. Using NordVPN or even ExpressVPN or PIA seems to be beneficial for many users.
- Surface web search engines can’t access the darknet, but specialized dark web search engines can help you find what you’re looking for.
- By equipping yourself with the right tools like Forest VPN and Tor or Onion browsers, you can explore safely and securely.
- The Tor browser is your gateway to the dark web, allowing you to access .onion sites anonymously.
- We used it to jump onto various .onion marketplaces, forums, and directories, and it kept everything clean without any IP or DNS leaks, and no surprise disconnections.
- Always put your safety and legality first to ensure a secure browsing experience.
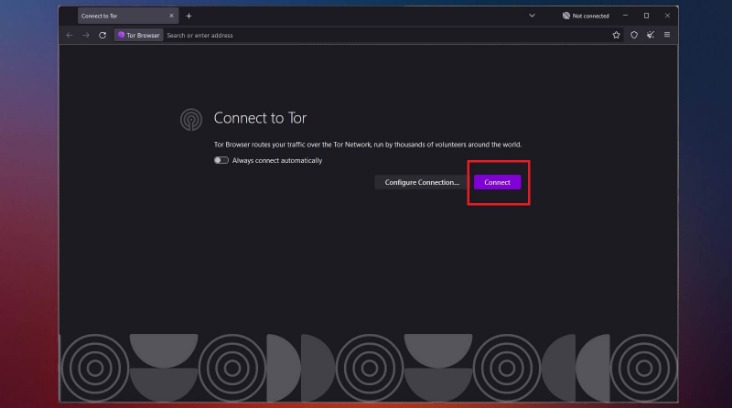
- Once downloaded, you can establish a connection to the Dark Web.
In a world of bulk data collection, surveillance, and personalized ad tracking, it’s up to us to take control of our personal privacy. For totally hiding all of your online antics, you’ll want to also use a VPN. Just remember, both the Tor Browser and VPNs will slow things down, so you’ll likely not be happy with streaming through the Tor Browser. Live OS options that can be run on nearly any computer by simply popping a USB stick in and booting from it include Subgraph OS, Freepto, and Tails.



