
Credit card prices also vary depending on the brand, with American Express being worth the most at 5.13 cents per dollar. To avoid falling victim to these scams, it’s essential to be cautious when entering sensitive information online. Adding fullz to a card purchase increases the price by about $30 for a physical card and under a dollar for digital card info. A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data. All transactions are conducted through cryptocurrency payments, with coordination handled via Telegram contacts.
Million Stolen Credit Cards Given Away Free On Dark Web Forum
When a hacker writes up new malware, steals a database, or phishes someone for their credit card number, the next step is often toward dark net marketplaces. These black markets allow buyers and sellers to make anonymous transactions using a combination of encrypted messages, aliases, and cryptocurrency. Unlike a credit card, a debit card is connected directly to your checking account, allowing fraudsters to immediately drain your account. Even if you report the fraudulent activity quickly and limit your losses, you may still face the issue of bounced checks or being late on payments, Krebs says. Stolen credit cards are often used to make purchases at specific sites that don’t have protections against fraud.
Decoding Credit Card Fraud On The Dark Web
Carding groups and channels reach up to tens of thousands of members, as they are easy to navigate and readily accessible. Unlike carding shops, which primarily focus on the trade of information, carding forums serve a broader purpose within the cybercriminal community. On these forums, actors will often share techniques, hacking tools, strategies, and resources for conducting fraudulent activities. When engaging in any transaction, it is essential to take protective measures and precautions to safeguard personal information and privacy.
My Ex Stalked Me, So I Joined A ‘dating Safety’ App Then My Address Was Leaked
Some are looking for illegal stuff they can’t buy elsewhere, like drugs or counterfeit documents. It was the first big site where people could anonymously buy drugs using Bitcoin, and it gained a lot of attention, until it was shut down by the FBI in 2013. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down.
❓ FAQ (2025 CVV Store Real Talk)
And then there’s malware—click the wrong link or download the wrong file, and your device could get infected. GBHackers on Security is a top cybersecurity news platform, delivering up-to-date coverage on breaches, emerging threats, malware, vulnerabilities, and global cyber incidents. If you notice suspicious activity, you can pause or close your virtual card in a few clicks—–via either Privacy’s web app or mobile app—and Privacy will decline any subsequent payment requests on the card.
More Hidden Sites
It is essential to exercise caution, protect personal information, and prioritize online security at all times. The fraud industry is a vibrant and thriving ecosystem across the darknet and deep web. Financial cyber criminals will continue to exploit vulnerabilities across all financial systems and continue to trade and sell victim’s personal data and accounts for continued financial gain. Scams and carding fraud are key segments of this market while government benefits and unemployment system fraud have skyrocketed in the pandemic. Merchants and banks have had to increase their insurance to account for the increasing criminal activity around carding. Sometimes it’s helpful to also contact the merchant and notify them that a claim has been submitted with the credit company.
These generated numbers link to your real card but can be limited by merchant, amount, or time. I’ve investigated too many breaches where malware jumped from an infected office computer to the payment network. Require multi-factor authentication for high-risk transactions, but it needs to be implemented intelligently. When we spot cards from these BIN ranges appearing in bulk listings, it often indicates a breach somewhere in the payment chain.
- Others might be stolen through phishing attacks on companies, stealing their customers’ payment information.
- The platform’s activity has increased significantly over the past year, indicating its growing influence and market share in the underground economy.
- It is known for strong encryption protocols and anti-DDoS protections, ensuring reliable access and user anonymity.
- BidenCash, operational since March 2022, functioned as a centralized platform for buying and selling stolen payment card data, login credentials, and server access.
- This closure is the latest of a series of retirements in the field of illicit dark web marketplaces.
How To Use Privacy Cards
If the security on the website becomes compromised, the hacker only has access to the virtual card, helping you protect your actual financial data from being stolen or misused. The threat actor’s marketing strategy involves leaking a large number of credit cards to attract potential clients from hacking and cybercrime forums. This move is likely to increase the platform’s popularity and draw in new customers.
How To Access Dark Web Anonymously And Know Its Secretive And Mysterious Activities

Collecting used keystrokes is how hackers typically guess credit card numbers, PINs, and passwords. A data breach occurs when confidential or protected information is exposed to unauthorized people or endpoints. Our platform can detect any suspicious mentions about organizations, or stolen payment information to give as much time as possible to prepare for data breaches. These systems can often identify when stolen card data is being tested before major fraud attempts begin.
Some dark web marketplaces even host content that’s not just illegal but extremely harmful, so it’s really important to understand the risks before diving in. Holders of any credit cards, whether you know if they have been compromised or not, are advised to monitor bank statements for any suspicious or unusual activity. While the immediate threat from this marketplace has been neutralized, ongoing vigilance and public awareness remain crucial to protect against the persistent risk of identity theft and financial fraud. If you suspect your card details have been stolen, you should immediately call your bank or credit card company.
How Many Cards Are Still Active?
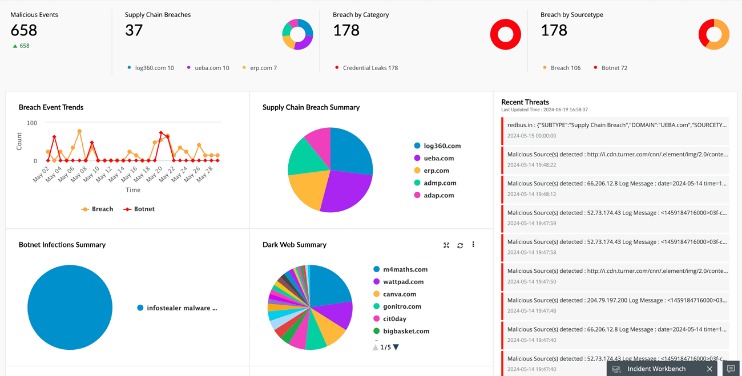
The black market for stolen credit cards is a massive illegal business, with cybercriminals getting their hands on card data in a number of ways. Point-of-sale card skimmers, targeted Magecart attacks on websites and info-stealing trojans are among their top tools for stealing credit-card data. In addition to just selling credit card details, some threat actors offer a “complete package” often referred to as “Fullz”. Fullz includes full personal details as well as financial details such as bank account details or social security numbers, which can be used for a full account takeover or identity theft.
Where Is A Card Number On A Credit Card: A Simple Guide
Card checkers are tools used by threat actors to verify the validity and authenticity of credit card information they purchase on the dark web. The cards were likely compromised online, using phishing, malware, or JavaScript-sniffers, which are increasingly popular among cybercriminals. Full or partial credit card details are commonly sold on the dark web, including BIN numbers, credit card numbers, expiration dates, and CVV numbers. Primarily focused on DDoS attacks, Dark Storm Team follows an opportunistic targeting strategy across various sectors. In addition to its cyber operations, the group also promotes hacking services for hire through its Telegram channel, offering DDoS attacks on protected websites and database dumps from organizations such as banks and airports. Established in April 2019 as a Russian-language group, EMP/mailpass/sqli Chat has since expanded into a global cybercrime discussion channel.



