
From here, you can visit any Onion website and enjoy the dark web safely and without worries of ISP tracking and surveillance. We can say the same about private networks belonging to companies and other entities. Some hospitals even have classified medical records you can’t access just like that. It is a relatively new provider but offers better features than most established VPNs.

Use Active Monitoring Of Financial And Identity Theft
More seriously, free VPNs – particularly those offered as standalone services – sometimes make money by selling your data to third parties. These aren’t the type of products you should use to keep you safe while exploring the dark web. Internet traffic is secured using adjustable levels of encryption. You can choose 256-bit for maximum protection or 128-bit if you want a faster connection. There are multiple protocol options available and protection against IPv6 leaks and DNS leaks.
Preparing To Access The Dark Web
While such stories can cast the dark web in a negative light, it’s worth noting that there are numerous legal and beneficial activities accessible through it. I advise sticking to well-known, reliable sites and taking extra precautions to ensure your security. Browsing the dark web puts you at risk of cyberattacks such as DDoS attacks, botnets, and other malware or viruses.
Step 6: Access The Tor Browser On Tails OS
- But contrary to popular belief, not everything found on the dark web is criminal in nature.
- Also, try its services risk-free with the 30-day money-back guarantee.
- Yes, Tor offers a portable version that can run from USB devices.
- Because of this, not many people are willing to give it a shot except if they have a very good reason.
- The content produced on this website is for educational purposes only and does not constitute investment advice or recommendation.
While you can visit the obscure part of the internet without a VPN, it’s better to go with one. Here are our favorite choices that work well and support Tor Over VPN perfectly. If you don’t know where to start, you can use The Hidden Wiki to find a few dark web domains. Simply copy the URL of the site you want to visit, press Enter, and you’re all set. The button above leads you to its website where you can claim an exclusive 70% discount for the 2-year plan. Click the button, get the provider for around $3.3/mo, and install it on your device.
We recommend that you use only the Tor browser to access the deep, dark web, if you must. If you fancy exploration, we’ve listed nine other options as well. In your browser settings (like the NoScript extension in Tor), you will want to disable JavaScript and other active scripts. By disabling, you reduce such attacks’ potential (especially on untrusted websites).

Do I Need A VPN To Access The Dark Web On My Phone?
However, note that dark web search engines don’t index as many sites as regular search engines, so results can sometimes be limited or outdated. The Tor Browser is an open-source web browser created for anonymous browsing and to evade censorship. It routes users’ traffic through thousands of volunteer-run servers called nodes/relays. These nodes/relays and the websites operating on them make up the Tor network, or as it is more generally named, the dark web. Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for.
How To Get Started With Tor Browser – A Web Browser Designed For Privacy
VPN-over-Tor breaks dark web compatibility, reintroduces trust in the VPN provider, and creates unnecessary complexity. It’s extremely rare and only useful in very specific cases, like if your VPN is only accessible through Tor. With this setup, your ISP sees Tor usage, and your VPN provider sees the final traffic after it leaves Tor.
Protecting Yourself From Dark Web Dangers
Knowing if your information is on the dark web is a critical part of protecting yourself from threats. Dark web monitoring tools are similar to a search engine (like Google) for the dark web. The most common of these browsers is Tor, which launched in 2002 and serves millions of users. Another is the Invisible Internet Project (I2P), which specializes in the anonymous hosting of websites on the dark web. You might think the dark web is a place of pure mystery, but really, it’s a realm of both intrigue and utility. Whether you’re curious or cautious, accessing it on your phone is not as daunting as it seems.
- It hides the use of Tor from your ISP and protects you if your Tor connection is compromised in some way.
- With your VPN active and Tor installed, you’re now ready to connect.
- This routing, through at least three nodes distributed worldwide, introduces latency, especially when there’s congestion on specific nodes.
- However, some nations have banned or restricted its use due to security concerns.
- Tor is by far the most widely used dark web network and is the biggest network in terms of content and activities.
Law Enforcement And Dark Web
No, while it hides your IP address and traffic, there are still vulnerabilities. Malicious exit nodes can monitor your traffic, and browser fingerprinting can track you. Governments also often monitor Tor usage, even if they can’t see your activity. It’s recommended to take safety precautions when accessing the dark web, even if you’re after legitimate content.
Tor Vs Alternative Solutions: What’s Best For You?

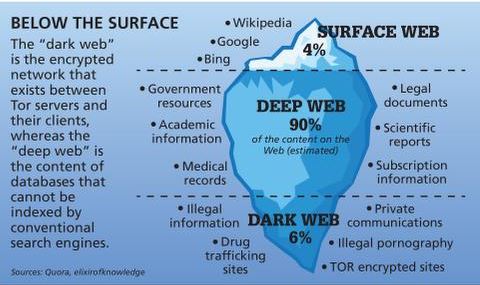
The dark web, which is what I’m discussing here, is a small subset of the deep web, and refers to websites that are specifically trying to stay out of sight. Darknet markets facilitate transactions for illegal goods and services. Silk Road was one of the first dark web marketplaces and it allowed users to trade multiple types of nefarious goods and services, including weapons and identity fraud resources. While many dark marketplaces have been shut down by authorities, new ones soon appear in their place.
While some studies have claimed that illegal Bitcoin activity is as high as 44%. The dark web is also a place for scammers to attract vulnerable and unwitting victims. The platform is also used by governmental cyber departments to identify and track potential criminals or offenders. You can never be sure who’s really behind the other end of the line. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information.

When you click through from our site to a retailer and buy a product or service, we may earn affiliate commissions. This helps support our work, but does not affect what we cover or how, and it does not affect the price you pay. Neither ZDNET nor the author are compensated for these independent reviews. Indeed, we follow strict guidelines that ensure our editorial content is never influenced by advertisers. There are a few reasons why the dark web isn’t stopped or shut down.

Some people opt for a virtual machine (VM) or a live operating system (such as Tails) that runs off a USB stick and leaves no trace once you shut it down. A good antivirus software can detect, quarantine, and remove threats before they can damage your device or acquire any sensitive information. My favorite antivirus in 2025 is Norton, which scored a 100% protection rating during my tests (handily beating the built-in protections on my devices). Be aware, however, that there are sites for absolutely everything, from the benign to the very illegal. There are some websites you can absolutely get in legal trouble for even visiting, so proceed with the utmost caution.



