The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data. However, data is required for understanding, monitoring, and improving the network. Furthermore, data will help to detect attacks against the network and possible censorship events.
Best VPNs For Staying Safe And Anonymous On The Dark Web In 2025
Just maintain strict security measures and then go to the dark web; that’s all there is to it. Also, make sure it’s malware-free and that your hardware is optimized. As you’re about to see, accessing the dark web is pretty easy if you have the right tools. To learn how to safely access the Dark Web sites listed above, read our Dark Web Access Guide here. Dark web links operate on a system of layers (like an onion) where each layer encrypts traffic as it passes through multiple relays. Apart from the dark web markets that are operating online today, some raided platforms influenced many markets.
One of the most insidious dangers on the dark web is not just technical malware or hidden exploits, but the human element—scammers and con artists who rely on psychological manipulation. Social engineering attacks leverage trust, fear, curiosity, or urgency to trick users into revealing sensitive information, transferring funds, or compromising their anonymity. By learning to recognize these ploys and adopting defensive habits, you can significantly reduce the risk of becoming a victim. The Tor Browser looks and feels similar to a regular web browser but is configured to prioritize privacy and security by default. It blocks browser trackers and resists fingerprinting, which helps maintain your anonymity while browsing. The dark net is famous for being a hub of black market websites for buying and selling products and services.
What Are Onion Sites?
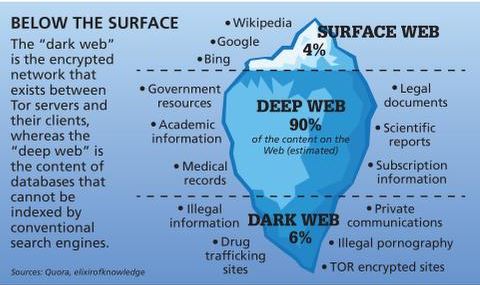
The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. Instead, you need a specific configuration, software, or authorization, such as Tor, to access it.

Essential Security Tips For Using Dark-Web Marketplaces
It features over 40,000 listings including narcotics, counterfeit items, hacking tools, and stolen data. The marketplace is well-known for its bug bounty programs and robust security mechanisms, including mandatory 2FA. By exploring these categories of resources, users can discover that the dark web’s landscape is more nuanced than popular portrayals suggest. Education, activism, journalism, and creativity all find refuge here, protected by layers of anonymity. However, it’s vital to approach each new platform with caution—vetting its authenticity, reputation, and purpose before fully engaging.
A Central Directory Of onion Links
But as long as you don’t knowingly engage in illicit activity on the dark web, you are completely fine. We ensured that the dark web sites we chose had reviews and feedback from real users on other forums; this way, we can be sure of the site’s reliability and legitimacy. The developers of ProtonMail recommend using the Tor browser to visit the dark web version of the service. This ensures greater security and privacy, making it much more difficult for snoopers to get in.
Which Darknet Market Is Safe
Just like Google, the dark web has some search engines present on it. Though they have their limitations, most of the time you’ll see irrelevant or spammy links for your search results. Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web). It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource.
Are Dark Web Links Illegal?
That’s helpful because Tor can suffer IP leaks and malicious actors can run Tor servers. Basically, if a Tor IP leak occurs before you connect to the VPN, your real IP address will be exposed. But if you connect to the VPN before connecting to Tor and an IP leak occurs, only the VPN’s IP address will be exposed. Yes, but you need to be cautious because there are many malicious sites on the dark web. The best way to do that is to get the link from legitimate sources, like The Hidden Wiki.
Legit Dark Web Sites: 50 Onion Links You Can Safely Explore Today

Hidden Wiki, although comprehensive, contains some very disturbing and very illegal info. While people and organizations do host legitimate and useful sites on the dark web, it’s still best to tread cautiously. Despite Tor’s privacy-focused design, malicious entities are more likely to target your data in transit and on .onion sites. Using Tor to access dark web links isn’t illegal, but your ISP will notice, and others may too.
- Data like this can also help estimate how many people actively access the dark web and how many hidden websites truly exist—you can even tell where the users are accessing from.
- Sci-hub has more than 80 million research documents, and more than 80% of the database contains journal research articles.
- The .onion version helps users in restrictive regions or those looking for more privacy.
- Essentially, it’s a search engine like Google or Safari, but unlike other search engines, it doesn’t track your browsing activity or collect user data.
I Legal And Ethical Considerations
To find .onion links for dark web sites, you’ll need to use a dark web search engine. Many of them are safe for beginners to use since they filter out dangerous/illegal content to only provide safe .onion links. My favorites are DuckDuckGo (usually the Tor browser’s default search engine), The Hidden Wiki, and Ahmia. Archive Today’s .onion link allows users to access its web page archiving service anonymously, preserving snapshots of websites for future reference. The platform has saved millions of web pages, ensuring information remains available even if the original sources are removed or changed.
Subscribing to forums or newsletters hosted on .onion domains can give you early warnings about impending crises. Learn the language, study the culture, and build connections with like-minded individuals who value independence over compliance. Welcome to this collection of darknet resources, curated exclusively for educational and informational purposes. This repository serves as a knowledge hub for individuals interested in understanding the structure, functionalities, and applications of the darknet. Please note that all material provided here is aimed at promoting awareness, responsible research, and ethical use of information.
History Of Darknet Markets
If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor. Activists, whistle blowers, and journalists also use the dark web to communicate securely with sources and news organizations. Wasabi Wallet is a Bitcoin wallet that not only hides all your data in the Tor network but also allows you to “join” your transactions with others to increase your anonymity.
ProPublica is a popular online publication that won five Pulitzers in 2016. It aims to expose abuses of power and betrayal of public trust through investigative journalism. Moreover, due to its popularity, many copycats of the Hidden Wiki exist. So don’t be surprised if you encounter different versions that claim to be genuine, and be very careful.
As you might expect, Bitcoin is the top cryptocurrency being used on the Dark Web. Chainalysis says that $790 million worth of cryptocurrencies were used to shop in darknet markets during 2019. While some studies have claimed that illegal Bitcoin activity is as high as 44%. The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access. These can include the previously mentioned illegal offerings, but can also include ultra-private information designed to be shared only with certain parties.