Accessing the dark web isn’t like surfing the web everywhere else online. We don’t want to leave you with the impression that everything on the dark web is nefarious or illegal. The Tor network began as an anonymous communications channel, and it still serves a valuable purpose in helping people communicate in environments that are hostile to free speech. “A lot of people use it in countries where there’s eavesdropping or where internet access is criminalized,” Tiquet said. Successfully navigating this hidden world requires preparation, vigilance, and a thorough understanding of both the technical and ethical challenges at play.
Interacting With Online Communities
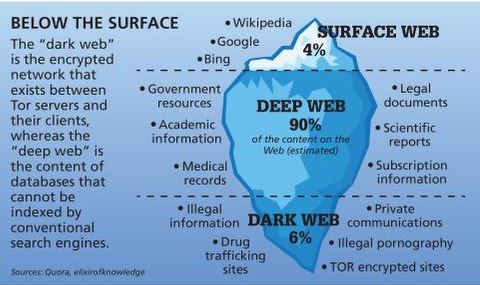
It allows you to access and browse websites anonymously, using masked IP addresses. You can only access the dark web with the Tor browser, which prevents tracking, surveillence, and ad targeting. The deep web is the next layer, and it encompasses a massive amount of online data that is not available for public consumption and not indexed by clear web search engines.
Key Points To Remember:
Cybercriminals often use the Dark Web to distribute ransomware, steal personal information, or commit fraud. The Surface Web is the portion of the internet that we interact with on a daily basis. It’s made up of websites indexed by search engines, such as Google, Yahoo, or Bing. These are the websites we visit without thinking twice, like news outlets, e-commerce sites, blogs, and social media platforms. There are numerous phishing sites, too, as explained earlier, designed to fool users into giving up their personal data.

Finally, Tor’s encryption system is quite complex, meaning it can be a very slow process to navigate from A to B across the web. If you value a speedy browsing experience, chances are Tor won’t be your browser of choice. Having said that, sometimes, it’s best to steer clear of the dark web entirely. Luckily, Clario Anti Spy is here to give you a worry-free digital experience.
- Onion links are URLs that end with .onion and can only be accessed through the Tor network.
- Hackers sell access to email accounts, social media profiles, or other information that can be used for identity theft.
- Therefore, it’s best to use a VPN no matter the personal device you’re using.
- Read on to learn the pros and cons of the dark web, how to access it, and get tips for staying safe.
- Surfshark works well with streaming platforms and is able to access geo-restricted content from the likes of Netflix, HBO, Hulu, and Disney+.
- This is why it’s important to visit only well-known, reputable sites with a history of providing safe, reliable information or services.
How To Safely Access The Dark Web
- The dark web’s hazards include many risks, related to network breaches or data compromises.
- In certain countries, the dark web facilitates political discourse and conversation that would otherwise be censored, outlawed, or eradicated in entirety.
- Accessing the Dark Web requires cautious navigation, and adhering to certain tips can help ensure a safer and more secure experience.
- The penalties for these offenses can range from fines to lengthy prison sentences, depending on the jurisdiction and severity of the crime committed.
Using a VPN in conjunction with the Tor Browser is an excellent way to keep your online travels secure and private. A VPN’s ability to hide your Tor usage from your ISP and from government authorities makes for a valuable addition to your online privacy arsenal. When you install the Tor Browser, it comes preconfigured with the most secure privacy settings. That means Javascript is disabled, extensions are disabled, and the browser is configured to warn you if an attempt is made to download a file and open it in another application. For example, randomly clicking a link can land you in extreme content, such as child pornography, which is a serious criminal offense to access.
Understanding The Risks
It is also essential to be cautious when interacting with others on the Dark Web, as not everyone may have good intentions. Avoid sharing personal information and be wary of any requests for sensitive data or financial transactions. Finally, it is advisable to use encrypted messaging services, such as PGP (Pretty Good Privacy), for secure communication on the Dark Web.
Drug Trafficking Sites
Remember only to make purchases using digital currencies and never provide any online banking login details. By implementing these security measures, you can significantly enhance your online safety while accessing the dark web. However, it’s important to understand that no system or practice can offer absolute security. Always exercise caution and stay informed about the latest security practices to mitigate risks effectively. When using Tor Browser, it is important to note that while it provides a higher level of anonymity, it does not guarantee complete protection. It is still possible for malicious actors to monitor online activities, especially if users engage in unsafe browsing practices or download suspicious files.
NordVPN adheres to a strict no-logs policy, which has been twice verified by independent auditors. This allows you to use public WiFi privately and without fear of hacking. There’s no chance of your real IP address leaking, while it benefits from some of the fastest speeds on the market. In many cases, people fall victim to fake marketplaces, where they pay for products (such as illegal substances or hacking tools) but never receive what they paid for.
Anonymity Is In Your Hands

By being aware of the potential risks, following recommended security practices, and using the Dark Web responsibly, you can navigate this hidden part of the internet more safely and effectively. The Dark Web is a fascinating and mysterious realm of the internet that offers both benefits and risks for those who choose to explore it. While it provides anonymity, privacy, and access to censored information, it is important to approach the Dark Web with caution and adhere to ethical guidelines. If you come across illegal activities or believe you have encountered a scam on the Dark Web, consider reporting it to the appropriate authorities. Providing information can assist in combating illicit activities and protecting others from falling victim to scams.
The Dark Web is a complex, multifaceted space, shrouded in secrecy and filled with both intrigue and danger. It serves as a vital tool for people seeking anonymity and privacy, offering protection to those living under oppressive regimes or looking to communicate securely. However, it is also a haven for illegal activities, cybercrime, and dark trade. Many cybersecurity and tech experts recommend using a VPN whenever you want to access the dark web via the Tor Browser or any other specialist browser. A quality VPN like ExpressVPN will encrypt your internet traffic and mask your IP address, providing an extra layer of anonymity when establishing the initial Tor connection.

Friends & Links
First, it’s difficult to track and monitor activity on the dark web since much of it is encrypted. The best way to find out is to check the “Have I Been Pwned” (HIBP) website. This website allows you to type in your email address or phone number and see if it’s been compromised in any data breaches. If your information has been compromised, then it’s likely that your phone number is also on the dark web. The big downside is that your ISP will know you are using Tor, which is cause for concern in some places and will put many people off using this method. In this instance, too, it is important to use a logless VPN and pay with Bitcoin if you can to stay anonymous.
VPN over Tor requires you to place trust in your ISP but not your VPN and is best if you want to avoid bad Tor exit nodes. Some consider VPN over Tor more secure because it maintains anonymity throughout the entire process (assuming you pay for your VPN anonymously). Although the official Tor Project advises against VPN over Tor, both methods are superior to not using a VPN at all. Put simply, the deep web is all the information stored online that isn’t indexed by search engines. You don’t need special tools or a dark net browser to access most of the deep web; you just need to know where to look.

Viruses and hacker forums are prevalent, with various types of malware and opportunities for illegal hacking services, which could compromise your personal devices. Webcam hijacking, through remote administration tools, presents a privacy invasion risk, highlighting the importance of physical safeguards like covering webcams when not in use. If you log into personal accounts on the dark web or visit websites with tracking scripts, then your activity may be tracked.



