Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN. Unlike regular browsers that directly connect to websites via your ISP’s DNS, Tor anonymizes your journey by routing your request through several relays before reaching its destination. You should now be able to access the server via port 80 successfully. Hacking is identifying and exploiting weaknesses in computer systems and/or computer networks. Ethical hacking is about improving the security of computer systems.

Step 4: Avoid Clicking Suspicious Links
The exit node decrypts your traffic and thus can steal your personal information or inject malicious code. Additionally, Tor exit nodes are often blocked by websites that don’t trust them, and Tor over VPN can’t do anything about that, either. That information is hidden simply because most users won’t find it relevant.
Install The Tor Browser
Torch supports both V2 and V3 .onion addresses, ensuring compatibility with older and newer sites. Ahmia’s filtering kept me away from shady marketplaces peddling stolen data, saving me from potential scams. However, when I searched for a specific blockchain-related forum, Ahmia returned only two results, and I had to use Torch for broader coverage.

MITRE ATT&CK Framework Explained Your Guide To Cybersecurity Threat
Your ISP only sees the encrypted VPN traffic and won’t know you’re on Tor. A logless VPN, which doesn’t store any traffic logs nor session logs is highly preferable. Traffic logs are a bigger concern than session logs, but neither are good.
This enhances privacy against attacks but causes temporary downtime or broken links. Directories like Torlinks provide curated, categorized links for quick, structured access to trusted sites, pros including ease for beginners and reduced spam exposure. Cons are outdated entries and no keyword search, limiting discovery.

Choose An Overlay Network
When you search for something on Google or Bing, you’re using the clear web. What if your biggest cybersecurity risk isn’t a hacker in a distant country, but someone with a co… Struggling to find a simple way to access shared files across your company network? Regular browsers access much of the deep web, especially sites behind logins.
Anyone can access the dark web, and it’s not that complicated to do so. Just remember, if you want to explore the dark web, be very careful. This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware. Tails also protects you from possible malware, viruses, or keystroke loggers that may have already infected the computer, as it doesn’t run the operating system already installed on the device. The advantage of using a dedicated computer just to browse the dark web is that your main computer isn’t exposed to any of the threats or risks tied to entering the dark web.
Protecting Your Data: Preventing Personal Information Leaks
Instead of relying on traditional domain name system (DNS) servers, onion websites use cryptographic keys and hashes to generate their URLs and establish connections within the Tor network. To stay protected from potential security vulnerabilities, it’s important to keep your Tor Browser up to date. The developers of the Tor Browser regularly release updates that contain security patches and improvements. Configure the Tor Browser to check for updates automatically or periodically visit the official Tor Project website to download the latest version. When using the Tor Browser, it’s crucial to maintain and respect the privacy settings. The Tor Browser is automatically configured to provide a certain level of privacy and security.
Can I Be Traced, Tracked, Or Hacked If I Use Tor?
- Tor’s mobile browser, with 20% of users by 2025 (Tor Project metrics), drives demand for responsive, low-bandwidth engines.
- As an information security architect with over 10 years advising Fortune 500 companies on privacy technologies, I‘ve helped thousands of clients securely leverage the dark web.
- In contrast, VPN over Tor setups won’t protect your real IP address if Tor leaks, require more technical setup, and aren’t supported by many VPN providers.
- Don’t just rely on marketing materials; request a Proof of Concept (PoC).
- Fire up Tor, choose your engine, verify your .onion links, and dive in—just keep your digital armor on.
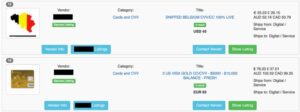
The right tools, like Forest VPN, can help you explore safely and securely. Let’s unpack the steps and safety measures you’ll need for this expedition. I’ve listed the best ways to access the dark web safely, including connecting to a VPN server and using private search engines. Still, there are plenty of good reasons to access it, like research, whistleblowing, journalism, and financial privacy. However, the Dark Web has gained infamy due to its association with illegal activities. Underground marketplaces, known as darknet markets, provide a platform for exchanging illicit goods and services, including drugs, weapons, counterfeit documents, and stolen data.
How Do I Access The Dark Web In 2025?
The dark web is full of malware, phishing scams, and other malicious threats that can compromise your device and personal data. Cybercriminals often disguise harmful files as legitimate downloads, making it easy to get tricked. It also prevents your IP address from being collected by cybercriminals on the dark web (this can happen if your traffic goes through a Tor server run by bad actors).
Examples Of Deep Web Content:
This setup is easy to configure, and you don’t need any special settings or features. Just turn on your VPN, wait for the connection to stabilize, and launch Tor. Your internet activity is still subject to exit node risks, so always use HTTPS and avoid entering any personal information on unencrypted sites. Even with Tor and a VPN, you’re not fully protected unless you also lock down your behavior. Most dark web leaks happen when users skip basic safety steps or reveal too much without realizing it.
Navigating the Dark Web can be a complex endeavor, but you don’t have to do it alone. Reputable organizations, security researchers, and privacy advocates provide a wealth of insights, tutorials, and software to help you explore safely and responsibly. Below are some trustworthy starting points and authoritative references. I2P is an anonymous overlay network designed primarily for peer-to-peer applications. There are many different ways to access the dark web, but navigating it can be tricky and dangerous if you don’t know what you’re doing. A VPN will give you an extra layer of protection and anonymity, making it much safer to explore the dark web.
Then individual applications must each be separately configured to work with I2P. You’ll need to configure your browser’s proxy settings to use the correct port on a web browser. For a number of technical reasons, it’s much faster and more reliable than Tor. The peer-to-peer routing structure is more advanced, and it does not rely on a trusted directory to get route information.
It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims. There are a number of services and tools available on the dark web, many of which can be used for nefarious purposes. We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better.
✅ Legal Content
In 2025, I tested OnionLand for a dark web news aggregator for a media trends piece. Searching “dark web news” triggered autocomplete suggestions like “onion news blog,” leading to a solid .onion site with daily updates on Tor-based journalism. However, one link led to a marketplace with questionable login prompts, forcing me to backtrack and verify via Torlinks. But the lack of filtering is a constant headache; I’ve learned to cross-check every link via directories or forums and keep my antivirus on high alert.